Social engineering manipulates human psychology to exploit trust and extract sensitive information, while phishing specifically uses deceptive emails or messages to trick victims into revealing credentials or clicking malicious links. Both tactics rely on psychological manipulation rather than technical vulnerabilities, making user awareness critical for prevention. Effective cybersecurity training emphasizes recognizing suspicious behavior and verifying communications to reduce the success of these attacks.
Table of Comparison
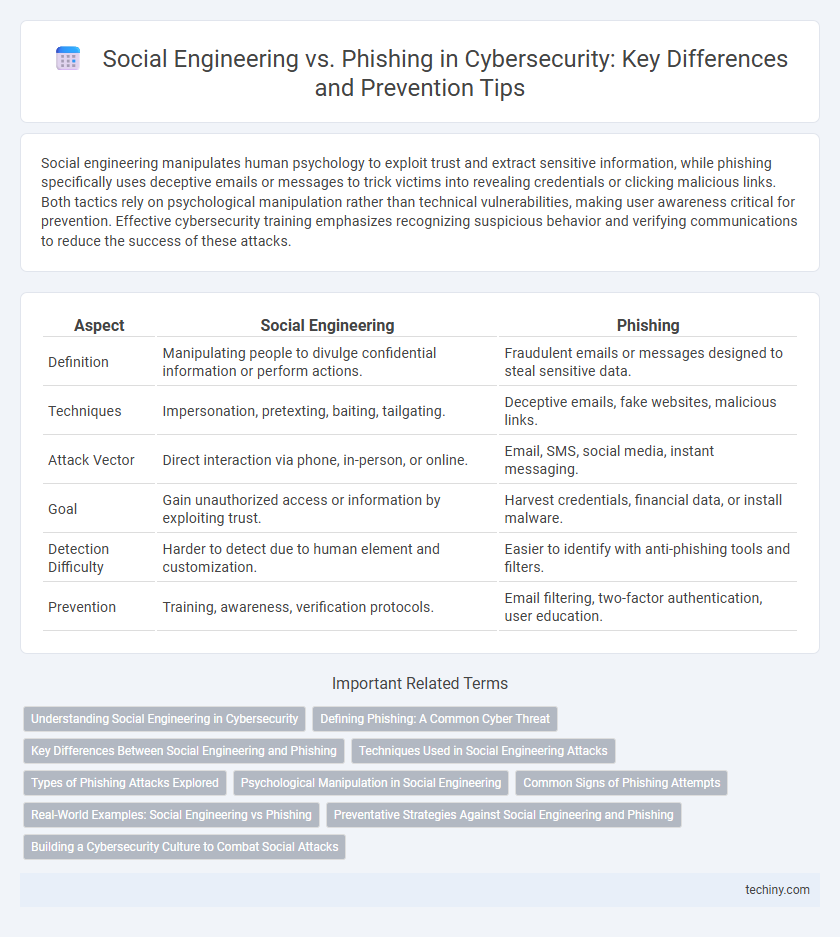
| Aspect | Social Engineering | Phishing |
|---|---|---|
| Definition | Manipulating people to divulge confidential information or perform actions. | Fraudulent emails or messages designed to steal sensitive data. |
| Techniques | Impersonation, pretexting, baiting, tailgating. | Deceptive emails, fake websites, malicious links. |
| Attack Vector | Direct interaction via phone, in-person, or online. | Email, SMS, social media, instant messaging. |
| Goal | Gain unauthorized access or information by exploiting trust. | Harvest credentials, financial data, or install malware. |
| Detection Difficulty | Harder to detect due to human element and customization. | Easier to identify with anti-phishing tools and filters. |
| Prevention | Training, awareness, verification protocols. | Email filtering, two-factor authentication, user education. |
Understanding Social Engineering in Cybersecurity
Social engineering in cybersecurity exploits human psychology to manipulate individuals into divulging confidential information or performing actions that compromise security. Unlike phishing, which primarily uses deceptive emails or messages to trick victims, social engineering encompasses a broader range of tactics including pretexting, baiting, and impersonation. Recognizing these varied methods is crucial for developing effective defense strategies and enhancing organizational cybersecurity awareness.
Defining Phishing: A Common Cyber Threat
Phishing is a prevalent cyber threat that involves deceptive tactics to trick individuals into revealing sensitive information such as passwords, credit card numbers, or personal data. This attack typically employs fraudulent emails, websites, or messages appearing to be from legitimate sources to exploit human psychology. Understanding phishing as a distinct form of social engineering highlights its reliance on manipulation rather than technical hacking.
Key Differences Between Social Engineering and Phishing
Social engineering manipulates human psychology to gain unauthorized access, targeting individuals through various tactics such as pretexting, baiting, or tailgating. Phishing is a specific type of social engineering that primarily uses fraudulent emails or messages to deceive victims into revealing sensitive information or downloading malware. The key difference lies in social engineering's broader scope of interaction methods versus phishing's reliance on electronic communication channels.
Techniques Used in Social Engineering Attacks
Social engineering attacks utilize psychological manipulation techniques such as pretexting, baiting, and tailgating to exploit human trust and gain unauthorized access to sensitive information or systems. These methods often involve impersonation, creating urgency, or leveraging social norms to deceive victims into divulging credentials or clicking malicious links. Phishing, a subset of social engineering, specifically uses deceptive emails or websites to trick users into revealing personal data or downloading malware.
Types of Phishing Attacks Explored
Phishing attacks encompass various types such as spear phishing targeting specific individuals or organizations, whaling aimed at high-profile executives, and clone phishing where legitimate emails are duplicated with malicious links. These tactics exploit social engineering principles by manipulating trust and urgency to deceive victims into revealing sensitive information or downloading malware. Understanding these diverse phishing methods is crucial for implementing effective cybersecurity defenses and user education programs.
Psychological Manipulation in Social Engineering
Social engineering leverages psychological manipulation techniques to exploit human trust and manipulate individuals into revealing confidential information or granting system access. Techniques such as pretexting, baiting, and impersonation exploit cognitive biases and emotional triggers to bypass technical security measures. Unlike phishing, which primarily uses deceptive emails, social engineering encompasses a broader range of psychologically driven tactics tailored to manipulate human behavior directly.
Common Signs of Phishing Attempts
Common signs of phishing attempts include suspicious email addresses that mimic legitimate organizations, urgent or threatening language prompting immediate action, and unsolicited requests for personal or financial information. Phishing messages often contain poor grammar, spelling errors, and unexpected attachments or links leading to malicious websites. Awareness of these indicators is critical for detecting social engineering tactics aimed at compromising cybersecurity defenses.
Real-World Examples: Social Engineering vs Phishing
Social engineering tactics exploit human psychology to manipulate victims into revealing confidential information, as seen in the 2011 RSA breach where attackers used spear-phishing emails to gain network access. Phishing schemes like the 2020 Twitter Bitcoin scam involve fraudulent messages impersonating trusted sources to steal credentials or money. Both methods highlight the importance of multi-layered security awareness training and robust technical defenses to mitigate these sophisticated cyber threats.
Preventative Strategies Against Social Engineering and Phishing
Implementing multi-factor authentication and regular employee training on recognizing suspicious communications significantly reduces the risk of social engineering and phishing attacks. Deploying advanced email filtering systems and verifying sender identities can prevent malicious links and attachments from reaching end users. Maintaining updated software and fostering a culture of cybersecurity awareness are crucial in strengthening organizational defenses against these threats.
Building a Cybersecurity Culture to Combat Social Attacks
Building a cybersecurity culture emphasizes continuous employee training and awareness to recognize and thwart social engineering and phishing attacks targeting organizational vulnerabilities. Implementing strict policies, simulated phishing exercises, and encouraging vigilance reduces the success rate of these tactics by fostering an environment of skepticism and verification. Embedding cybersecurity principles into daily workflows strengthens human defenses, aligning with technical safeguards to provide comprehensive protection against social attacks.
Social engineering vs phishing Infographic
 techiny.com
techiny.com