Cyberespionage involves covert operations aimed at stealing sensitive information from governments or organizations to gain strategic advantages without direct conflict. Cyberwarfare escalates to offensive cyberattacks designed to disrupt, damage, or destroy critical infrastructure or military systems, often as part of broader geopolitical conflicts. Understanding the distinctions between these threats is essential for developing targeted cybersecurity defenses and national security policies.
Table of Comparison
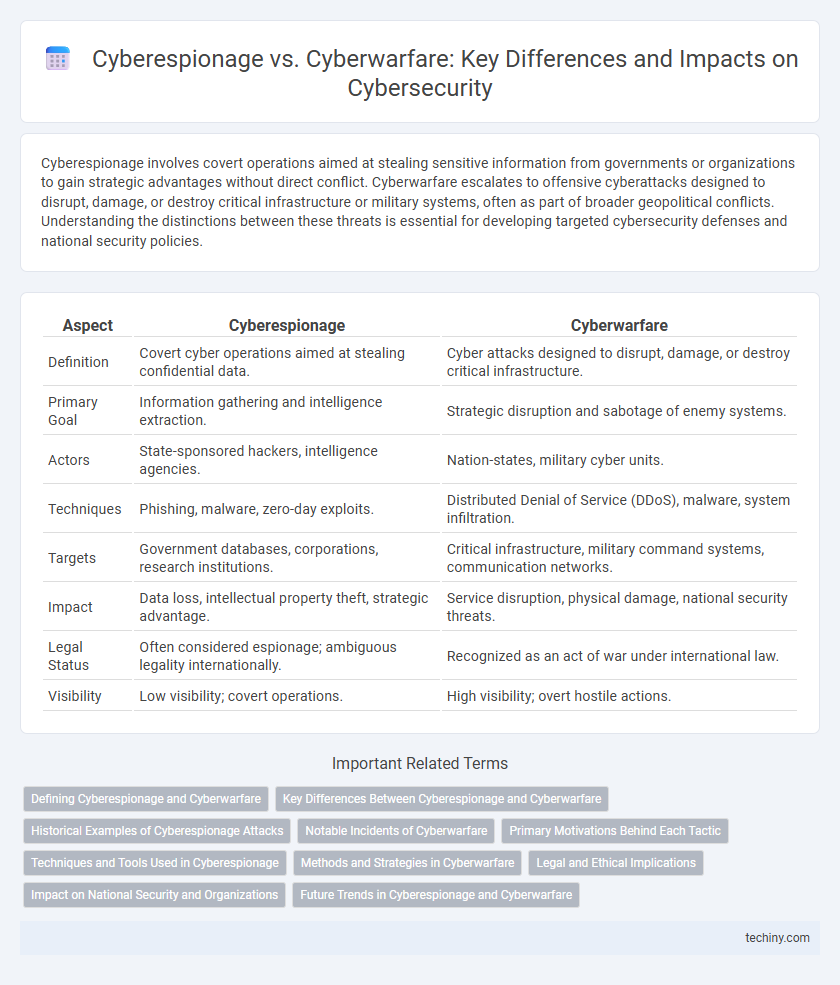
| Aspect | Cyberespionage | Cyberwarfare |
|---|---|---|
| Definition | Covert cyber operations aimed at stealing confidential data. | Cyber attacks designed to disrupt, damage, or destroy critical infrastructure. |
| Primary Goal | Information gathering and intelligence extraction. | Strategic disruption and sabotage of enemy systems. |
| Actors | State-sponsored hackers, intelligence agencies. | Nation-states, military cyber units. |
| Techniques | Phishing, malware, zero-day exploits. | Distributed Denial of Service (DDoS), malware, system infiltration. |
| Targets | Government databases, corporations, research institutions. | Critical infrastructure, military command systems, communication networks. |
| Impact | Data loss, intellectual property theft, strategic advantage. | Service disruption, physical damage, national security threats. |
| Legal Status | Often considered espionage; ambiguous legality internationally. | Recognized as an act of war under international law. |
| Visibility | Low visibility; covert operations. | High visibility; overt hostile actions. |
Defining Cyberespionage and Cyberwarfare
Cyberespionage involves covertly infiltrating computer systems to steal sensitive information for strategic advantage, often conducted by state-sponsored actors targeting governments or corporations. Cyberwarfare encompasses offensive and defensive operations in cyberspace aimed at disrupting, damaging, or controlling critical infrastructure and military assets to impair an adversary's national security. Both activities leverage sophisticated malware, hacking techniques, and intelligence gathering but differ in intent, with cyberespionage focused on information collection and cyberwarfare on direct confrontation and damage.
Key Differences Between Cyberespionage and Cyberwarfare
Cyberespionage primarily involves covert cyber activities aimed at gathering intelligence, typically targeting sensitive information from government, military, or corporate networks without detection. Cyberwarfare, by contrast, encompasses aggressive, often disruptive or destructive cyberattacks designed to undermine, disable, or destroy critical infrastructure, communication systems, or military assets during conflict. The key differences include intent--espionage seeks secret information extraction, whereas warfare involves hostile actions to impair adversary capabilities--and scale, with cyberwarfare generally involving larger, more overt operations that can impact national security on a broader level.
Historical Examples of Cyberespionage Attacks
Notable historical examples of cyberespionage attacks include the 2010 Stuxnet worm, which targeted Iran's nuclear facilities and marked a significant escalation in state-sponsored cyber operations. The 2015 Office of Personnel Management (OPM) breach exposed sensitive data of over 21 million U.S. government employees, attributed to Chinese state actors. These incidents illustrate the strategic use of cyberespionage to gather intelligence and disrupt adversaries without escalating to open cyberwarfare.
Notable Incidents of Cyberwarfare
Notable incidents of cyberwarfare include the 2007 cyberattacks on Estonia, where coordinated Distributed Denial of Service (DDoS) assaults disrupted government and financial services, attributed to Russian state actors. The 2010 Stuxnet worm targeted Iran's nuclear facilities, demonstrating sophisticated cyber capability to physically disrupt critical infrastructure. More recently, the 2017 WannaCry ransomware attack affected over 150 countries, crippling healthcare and transportation systems, highlighting the geopolitical impact of state-sponsored cyber operations.
Primary Motivations Behind Each Tactic
Cyberespionage primarily targets confidential information for political advantage, economic gain, or intelligence gathering to inform strategic decisions. Cyberwarfare aims to disrupt, damage, or destroy critical infrastructure, communication networks, and command systems to weaken adversaries during conflicts. Understanding these distinct motivations is crucial for developing tailored cybersecurity defense mechanisms and policies.
Techniques and Tools Used in Cyberespionage
Cyberespionage employs advanced persistent threats (APTs), spear-phishing campaigns, and zero-day exploits to infiltrate targeted systems covertly, enabling prolonged data exfiltration. Tools such as remote access trojans (RATs), keyloggers, and custom malware facilitate stealthy monitoring and extraction of sensitive information. Command and control (C2) servers coordinate these operations, while encryption and proxy networks like Tor ensure attackers maintain anonymity and evade detection.
Methods and Strategies in Cyberwarfare
Cyberwarfare employs sophisticated methods such as distributed denial-of-service (DDoS) attacks, zero-day exploits, and advanced persistent threats (APTs) to disrupt critical infrastructure and military communication systems. Strategies emphasize coordinated cyber offensives combined with electronic warfare and psychological operations to degrade enemy capabilities and morale. Nation-states invest heavily in cyber command centers and AI-driven threat detection to enhance real-time response and resilience against cyber intrusions.
Legal and Ethical Implications
Cyberespionage operates in a complex legal gray area, often violating national sovereignty and international law without clear enforcement mechanisms, raising profound ethical questions about privacy and state accountability. Cyberwarfare involves state-sanctioned attacks that challenge existing international humanitarian laws, necessitating new legal frameworks to address the proportionality and distinction of cyber operations targeting civilian infrastructure. Both activities complicate global cybersecurity governance, demanding robust ethical standards and transparent policies to balance national security interests with respect for human rights.
Impact on National Security and Organizations
Cyberespionage targets sensitive government and corporate data, undermining national security by exposing confidential information and intellectual property to foreign adversaries, which can compromise defense strategies and economic competitiveness. Cyberwarfare involves state-sponsored attacks that disrupt critical infrastructure, communication networks, and military systems, posing direct threats to public safety and national stability. Both forms of cyber conflicts force organizations to invest heavily in cybersecurity measures, incident response, and resilience planning to mitigate potential damages and protect national interests.
Future Trends in Cyberespionage and Cyberwarfare
Emerging trends in cyberespionage indicate an increase in AI-driven attacks that can autonomously bypass traditional security measures to extract sensitive information. Future cyberwarfare tactics are expected to integrate quantum computing capabilities, enabling unprecedented speed and complexity in offensive operations targeting critical infrastructure. The convergence of cyberespionage and cyberwarfare techniques highlights a growing focus on hybrid threats combining stealthy data breaches with disruptive cyberattacks to achieve strategic geopolitical objectives.
Cyberespionage vs Cyberwarfare Infographic
 techiny.com
techiny.com