Social engineering targets human psychology to manipulate individuals into revealing sensitive information or performing actions that compromise security, often bypassing technical safeguards. Technical exploitation involves directly attacking software vulnerabilities, hardware flaws, or network weaknesses to gain unauthorized access or control over systems. Effective cybersecurity requires a balanced defense strategy that addresses both human factors and technological vulnerabilities to mitigate risks comprehensively.
Table of Comparison
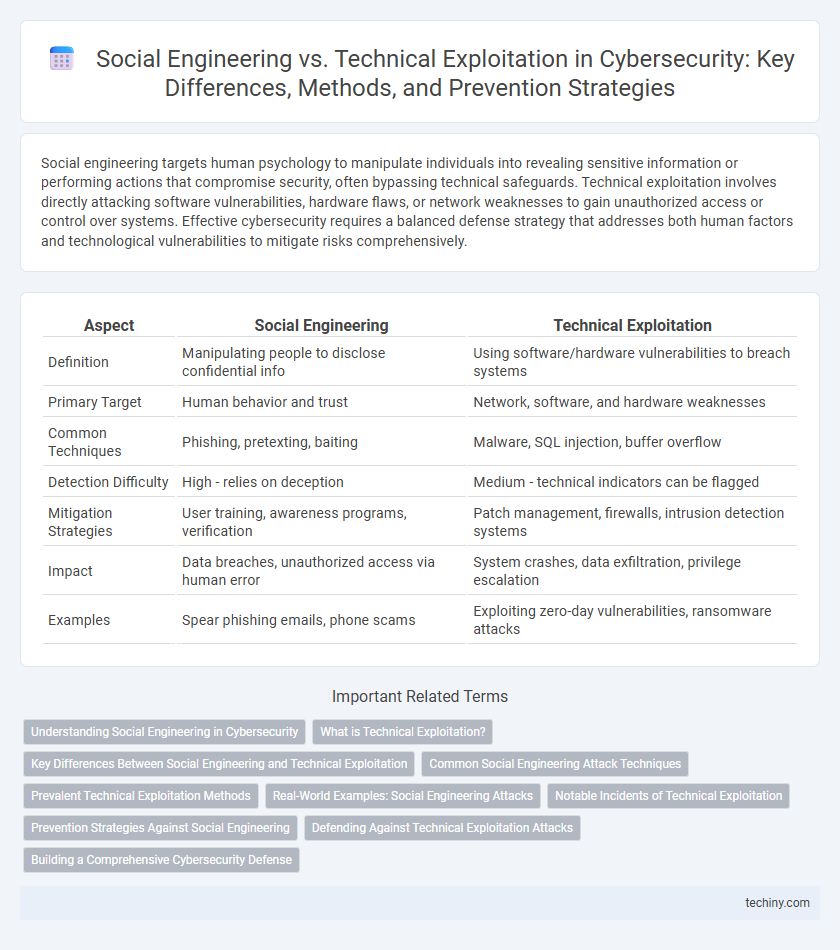
| Aspect | Social Engineering | Technical Exploitation |
|---|---|---|
| Definition | Manipulating people to disclose confidential info | Using software/hardware vulnerabilities to breach systems |
| Primary Target | Human behavior and trust | Network, software, and hardware weaknesses |
| Common Techniques | Phishing, pretexting, baiting | Malware, SQL injection, buffer overflow |
| Detection Difficulty | High - relies on deception | Medium - technical indicators can be flagged |
| Mitigation Strategies | User training, awareness programs, verification | Patch management, firewalls, intrusion detection systems |
| Impact | Data breaches, unauthorized access via human error | System crashes, data exfiltration, privilege escalation |
| Examples | Spear phishing emails, phone scams | Exploiting zero-day vulnerabilities, ransomware attacks |
Understanding Social Engineering in Cybersecurity
Social engineering in cybersecurity exploits human psychology to manipulate individuals into divulging confidential information or granting unauthorized access, bypassing technical defenses. Common tactics include phishing, pretexting, and baiting, which leverage trust, fear, or curiosity to compromise security. Understanding these techniques is crucial for developing effective awareness training and preventive measures against non-technical threats.
What is Technical Exploitation?
Technical exploitation involves leveraging software vulnerabilities, hardware flaws, and network weaknesses to gain unauthorized access or control over systems. Common methods include exploiting zero-day vulnerabilities, buffer overflows, malware injection, and network protocol attacks. This approach targets the technical infrastructure of an organization rather than manipulating human behavior, as seen in social engineering tactics.
Key Differences Between Social Engineering and Technical Exploitation
Social engineering exploits human psychology and behavior to gain unauthorized access, relying on deception, manipulation, and trust, whereas technical exploitation targets vulnerabilities in hardware, software, or network systems to breach security protocols. Social engineering attacks include phishing, pretexting, and baiting, while technical exploitation involves malware deployment, zero-day vulnerabilities, and buffer overflow attacks. The primary distinction lies in the attack vector, with social engineering manipulating people and technical exploitation manipulating technology.
Common Social Engineering Attack Techniques
Common social engineering attack techniques include phishing, spear phishing, pretexting, baiting, and tailgating, which manipulate human psychology to gain unauthorized access. Phishing remains the most prevalent method, targeting users with deceptive emails to steal credentials or distribute malware. These tactics exploit trust and human error rather than system vulnerabilities, contrasting with technical exploitation that relies on software weaknesses and code flaws.
Prevalent Technical Exploitation Methods
Prevalent technical exploitation methods in cybersecurity include phishing attacks, ransomware deployment, and zero-day vulnerabilities targeting software weaknesses. Attackers leverage exploits such as SQL injection, buffer overflow, and cross-site scripting (XSS) to gain unauthorized access or manipulate systems. Exploiting unpatched software and using advanced persistent threats (APTs) remain common strategies for compromising networks and stealing sensitive data.
Real-World Examples: Social Engineering Attacks
Social engineering attacks manipulate human psychology to gain unauthorized access, as seen in the 2011 RSA SecurID breach where attackers used phishing emails to compromise employee credentials. Another notable example is the 2013 Target data breach, initiated by social engineering tactics that targeted HVAC contractors to infiltrate the retailer's network. These real-world cases highlight the critical need for employee training and robust verification protocols to counteract social engineering threats effectively.
Notable Incidents of Technical Exploitation
Notable incidents of technical exploitation include the 2017 Equifax breach, where attackers exploited a vulnerability in the Apache Struts framework, compromising sensitive data of over 147 million individuals. The 2013 Target breach involved leveraging a third-party vendor's credentials to infiltrate the network, resulting in the theft of 40 million credit and debit card records. In 2014, the Sony Pictures hack exploited malware and zero-day vulnerabilities, causing significant data leaks and operational disruption.
Prevention Strategies Against Social Engineering
Effective prevention strategies against social engineering prioritize employee training programs to recognize phishing attempts, pretexting, and baiting tactics. Implementing multi-factor authentication and strict access controls minimizes the risk of unauthorized access caused by manipulated human behavior. Regular security audits and simulated social engineering attacks enhance organizational resilience by identifying vulnerabilities before attackers exploit them.
Defending Against Technical Exploitation Attacks
Implementing multi-layered security measures, such as firewalls, intrusion detection systems, and regular software patching, is crucial for defending against technical exploitation attacks. Employing endpoint protection solutions and continuous network monitoring helps identify and mitigate vulnerabilities exploited by malware or zero-day attacks. Conducting regular security audits and employee training on identifying suspicious activities reduces the risk of successful breaches through exploited technical flaws.
Building a Comprehensive Cybersecurity Defense
Building a comprehensive cybersecurity defense requires integrating strategies that address both social engineering and technical exploitation. Social engineering exploits human psychology to manipulate individuals into divulging sensitive information, while technical exploitation targets system vulnerabilities through software or hardware weaknesses. Combining endpoint protection, employee training, multi-factor authentication, and regular vulnerability assessments ensures a robust defense against these multifaceted cyber threats.
Social Engineering vs Technical Exploitation Infographic
 techiny.com
techiny.com