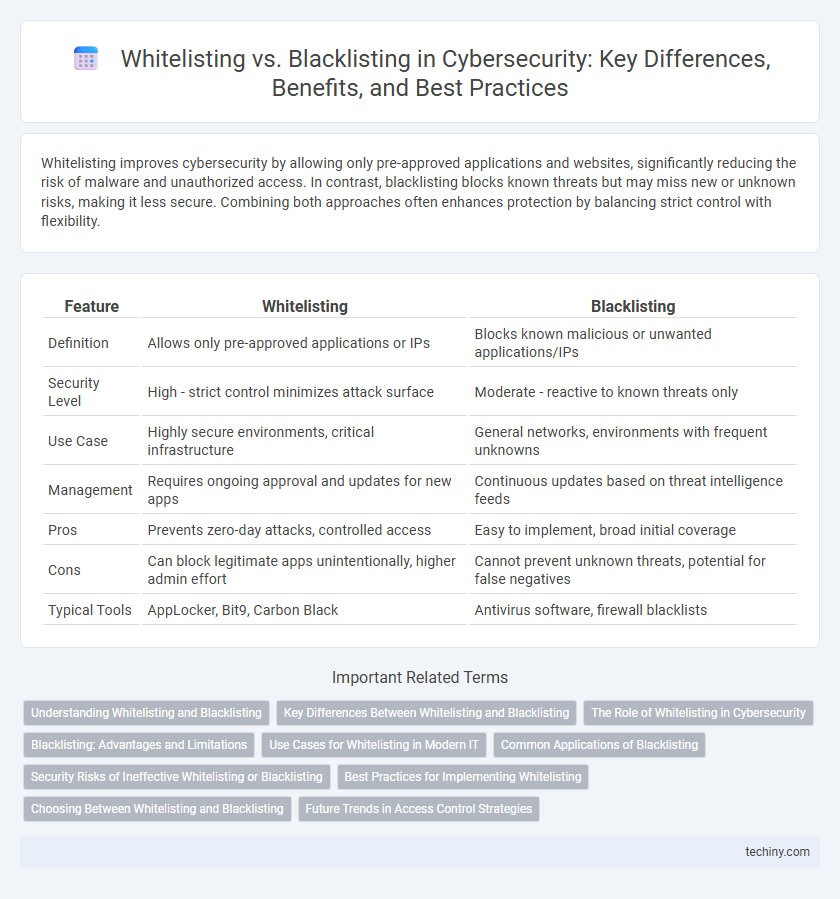
Whitelisting improves cybersecurity by allowing only pre-approved applications and websites, significantly reducing the risk of malware and unauthorized access. In contrast, blacklisting blocks known threats but may miss new or unknown risks, making it less secure. Combining both approaches often enhances protection by balancing strict control with flexibility.
Table of Comparison
| Feature | Whitelisting | Blacklisting |
|---|---|---|
| Definition | Allows only pre-approved applications or IPs | Blocks known malicious or unwanted applications/IPs |
| Security Level | High - strict control minimizes attack surface | Moderate - reactive to known threats only |
| Use Case | Highly secure environments, critical infrastructure | General networks, environments with frequent unknowns |
| Management | Requires ongoing approval and updates for new apps | Continuous updates based on threat intelligence feeds |
| Pros | Prevents zero-day attacks, controlled access | Easy to implement, broad initial coverage |
| Cons | Can block legitimate apps unintentionally, higher admin effort | Cannot prevent unknown threats, potential for false negatives |
| Typical Tools | AppLocker, Bit9, Carbon Black | Antivirus software, firewall blacklists |
Understanding Whitelisting and Blacklisting
Whitelisting and blacklisting are fundamental cybersecurity strategies used to control access and enhance system security. Whitelisting permits only pre-approved applications or IP addresses, minimizing risks by allowing known safe entities, while blacklisting blocks known malicious or unwanted items, offering broader but less precise protection. Implementing whitelisting reduces exposure to zero-day attacks and unauthorized access, whereas blacklisting requires constant updates to address emerging threats effectively.
Key Differences Between Whitelisting and Blacklisting
Whitelisting allows only pre-approved applications, IP addresses, or users to access a system, providing a proactive security approach by minimizing attack surfaces. Blacklisting blocks known malicious entities while allowing all others, which can leave systems vulnerable to unknown threats or zero-day exploits. The key difference lies in whitelisting's restrictive allowance versus blacklisting's permissive blocking, influencing overall security posture and management complexity.
The Role of Whitelisting in Cybersecurity
Whitelisting plays a crucial role in cybersecurity by allowing only pre-approved applications and processes to run, significantly reducing the risk of malware infections and unauthorized access. It offers a proactive defense mechanism that blocks unknown or potentially harmful software before execution, unlike blacklisting, which relies on identifying threats after they emerge. Implementing application whitelisting enhances endpoint security, enforces strict policy control, and minimizes the attack surface against zero-day exploits and advanced persistent threats.
Blacklisting: Advantages and Limitations
Blacklisting in cybersecurity offers the advantage of blocking known malicious IP addresses, domains, and applications, providing a targeted defense against recognized threats. This approach enables organizations to quickly respond to emerging dangers by updating blacklists with new entries. However, blacklisting's limitations include its inability to prevent zero-day attacks or unknown threats, as it relies on prior knowledge of malicious entities, and it may result in false positives that block legitimate activities.
Use Cases for Whitelisting in Modern IT
Whitelisting is ideal for environments requiring stringent security controls, such as financial institutions and healthcare providers, where only pre-approved applications and devices are permitted to operate. It effectively prevents zero-day attacks and unauthorized software installations by allowing only vetted programs to run, reducing the attack surface significantly. This use case is particularly beneficial in critical infrastructure systems and endpoint protection strategies, ensuring compliance with regulatory standards and enhancing overall network integrity.
Common Applications of Blacklisting
Blacklisting is commonly applied in cybersecurity to block malicious IP addresses, domains, and email senders associated with phishing and spam attacks. Network administrators often use blacklists to prevent access to known harmful websites and restrict traffic from suspicious sources. Endpoint security solutions implement blacklisting to deny execution of unauthorized or potentially dangerous software applications.
Security Risks of Ineffective Whitelisting or Blacklisting
Ineffective whitelisting can expose systems to zero-day attacks by allowing unknown or insufficiently vetted applications to run, while poor blacklisting fails to block emerging threats due to its inability to catch new malicious files or IP addresses. Both methods, if not dynamically updated with threat intelligence, increase vulnerability to malware infiltration and data breaches. Maintaining real-time monitoring and regular policy updates is critical to mitigate security risks associated with gaps in whitelist or blacklist enforcement.
Best Practices for Implementing Whitelisting
Implementing whitelisting in cybersecurity requires maintaining an up-to-date list of approved applications, IP addresses, or processes to ensure only trusted entities gain access to critical systems. Regularly auditing and monitoring the whitelist enhances protection against unauthorized software and malware while minimizing false positives that can disrupt operations. Integrating automated tools for dynamic policy enforcement and combining whitelisting with other security measures like endpoint detection and response (EDR) provides a robust defense against evolving cyber threats.
Choosing Between Whitelisting and Blacklisting
Choosing between whitelisting and blacklisting in cybersecurity depends on the specific security requirements and operational environment of an organization. Whitelisting offers stricter control by allowing only pre-approved applications or IP addresses, minimizing the risk of unknown threats but requiring intensive management and potential usability constraints. Blacklisting provides more flexibility by blocking known malicious entities, yet it may fail to prevent zero-day attacks or unknown vulnerabilities due to its reactive nature.
Future Trends in Access Control Strategies
Future trends in access control emphasize a shift from traditional blacklisting toward dynamic whitelisting frameworks powered by AI and machine learning to enhance threat detection and minimize false positives. Adaptive whitelisting integrates behavioral analytics and zero-trust principles, enabling continuous verification of user identities and device compliance in real time. The convergence of predictive analytics with context-aware access policies drives more granular, automated control over network and application access, improving resilience against evolving cyber threats.
Whitelisting vs Blacklisting Infographic
 techiny.com
techiny.com