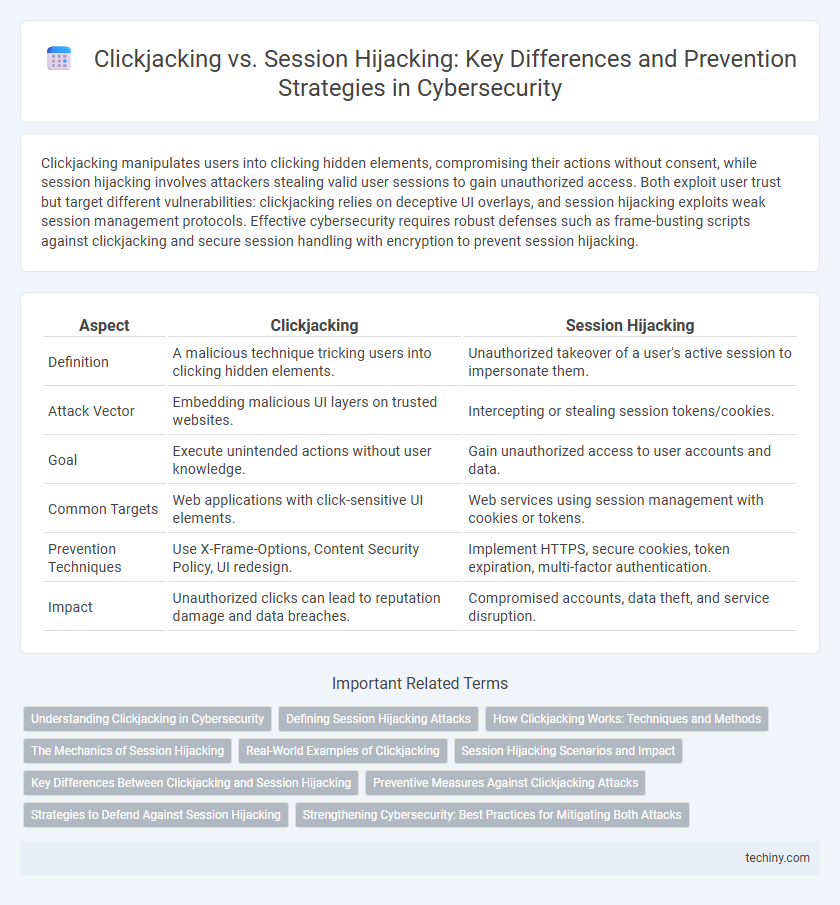
Clickjacking manipulates users into clicking hidden elements, compromising their actions without consent, while session hijacking involves attackers stealing valid user sessions to gain unauthorized access. Both exploit user trust but target different vulnerabilities: clickjacking relies on deceptive UI overlays, and session hijacking exploits weak session management protocols. Effective cybersecurity requires robust defenses such as frame-busting scripts against clickjacking and secure session handling with encryption to prevent session hijacking.
Table of Comparison
| Aspect | Clickjacking | Session Hijacking |
|---|---|---|
| Definition | A malicious technique tricking users into clicking hidden elements. | Unauthorized takeover of a user's active session to impersonate them. |
| Attack Vector | Embedding malicious UI layers on trusted websites. | Intercepting or stealing session tokens/cookies. |
| Goal | Execute unintended actions without user knowledge. | Gain unauthorized access to user accounts and data. |
| Common Targets | Web applications with click-sensitive UI elements. | Web services using session management with cookies or tokens. |
| Prevention Techniques | Use X-Frame-Options, Content Security Policy, UI redesign. | Implement HTTPS, secure cookies, token expiration, multi-factor authentication. |
| Impact | Unauthorized clicks can lead to reputation damage and data breaches. | Compromised accounts, data theft, and service disruption. |
Understanding Clickjacking in Cybersecurity
Clickjacking exploits a user's browser by overlaying invisible or disguised elements to trick clicks into performing unintended actions, compromising security and privacy. This attack manipulates web interfaces, causing users to unknowingly execute malicious commands such as changing settings, initiating transactions, or granting permissions. Effective defenses against clickjacking include frame-busting scripts, X-Frame-Options headers, and Content Security Policy (CSP) frame-ancestors directives.
Defining Session Hijacking Attacks
Session hijacking attacks involve unauthorized access to a user's active session by intercepting or stealing session tokens, allowing attackers to impersonate the legitimate user without needing login credentials. Unlike clickjacking, which tricks users into clicking hidden elements, session hijacking targets the communication between the user and the web server, exploiting vulnerabilities such as session fixation, cross-site scripting (XSS), or network sniffing. Effective prevention requires implementing secure cookie attributes, token expiration policies, and robust encryption protocols to safeguard session integrity.
How Clickjacking Works: Techniques and Methods
Clickjacking manipulates users into clicking hidden or disguised web elements by overlaying transparent iframes or buttons on legitimate webpages, tricking them into performing unintended actions. Techniques include UI redressing, where attackers use CSS and JavaScript to conceal malicious frames, and cursorjacking, which manipulates pointer events to redirect clicks. These methods exploit user interface vulnerabilities without requiring direct system access, enabling attackers to hijack clicks for stealing credentials or authorizing unauthorized transactions.
The Mechanics of Session Hijacking
Session hijacking exploits the vulnerability in web sessions by intercepting or stealing a user's session token, allowing unauthorized access to personal accounts or sensitive data. Attackers utilize methods such as packet sniffing, cross-site scripting (XSS), or session fixation to gain control over active sessions without the user's knowledge. This breach bypasses authentication by masquerading as the legitimate user, posing significant risks to confidentiality and data integrity in cybersecurity.
Real-World Examples of Clickjacking
Clickjacking exploits user interface vulnerabilities by tricking users into clicking hidden elements, famously demonstrated in the Facebook "Likejacking" attack that covertly gained likes for malicious pages. Another real-world example includes the 2010 Twitter clickjacking incident where users were unknowingly redirected to malicious sites containing harmful scripts. These attacks manipulate browser behavior without user suspicion, posing serious risks to account integrity and personal data security.
Session Hijacking Scenarios and Impact
Session hijacking occurs when attackers steal or manipulate active user sessions to gain unauthorized access to web applications, often exploiting vulnerabilities in session management or insecure communication channels. Common scenarios include theft of session cookies through cross-site scripting (XSS), man-in-the-middle attacks, or session fixation, leading to compromised user accounts and sensitive data breaches. The impact of session hijacking can result in financial losses, identity theft, and severe reputational damage for organizations due to unauthorized transactions and exposure of confidential information.
Key Differences Between Clickjacking and Session Hijacking
Clickjacking manipulates a user into clicking hidden elements on a webpage, leading to unintended actions, while session hijacking involves intercepting or stealing a user's active session token to gain unauthorized access. Clickjacking exploits user interface vulnerabilities, whereas session hijacking targets authentication and session management mechanisms. Protection against clickjacking includes frame busting scripts and Content Security Policy, whereas session hijacking defenses emphasize secure cookies, encryption, and multi-factor authentication.
Preventive Measures Against Clickjacking Attacks
Implementing frame busting scripts and utilizing the X-Frame-Options HTTP header significantly reduce the risk of clickjacking attacks by preventing malicious websites from embedding legitimate pages within iframes. Content Security Policy (CSP) directives, particularly frame-ancestors, allow precise control over which domains can frame the website, enhancing protection against UI redressing. User education on verifying trusted sites and avoiding suspicious links complements technical measures by reducing the likelihood of successful clickjacking exploitations.
Strategies to Defend Against Session Hijacking
Effective defense against session hijacking includes deploying secure cookie attributes like HttpOnly and Secure, enforcing multi-factor authentication (MFA), and ensuring encrypted communication through TLS/SSL protocols. Continuous monitoring of session anomalies and implementing short session timeouts further reduce risks by limiting the window for attackers. Employing intrusion detection systems (IDS) and regularly updating software also fortify defenses against unauthorized session access.
Strengthening Cybersecurity: Best Practices for Mitigating Both Attacks
Implementing multi-factor authentication (MFA) and regularly updating software patches are critical for mitigating clickjacking and session hijacking attacks. Employing Content Security Policy (CSP) headers and frame busting techniques effectively prevents clickjacking by restricting unauthorized framing of web pages. Session hijacking risks diminish through secure cookie attributes like HttpOnly and Secure, alongside continuous monitoring of user sessions for unusual activities.
Clickjacking vs Session Hijacking Infographic
 techiny.com
techiny.com