Sandbox environments isolate and analyze suspicious files or code in a controlled setting, preventing potential malware from affecting the main system. Honeypots mimic real systems or networks to attract attackers, capturing their techniques and behaviors for study. Both tools enhance threat detection but serve distinct roles in cybersecurity strategy.
Table of Comparison
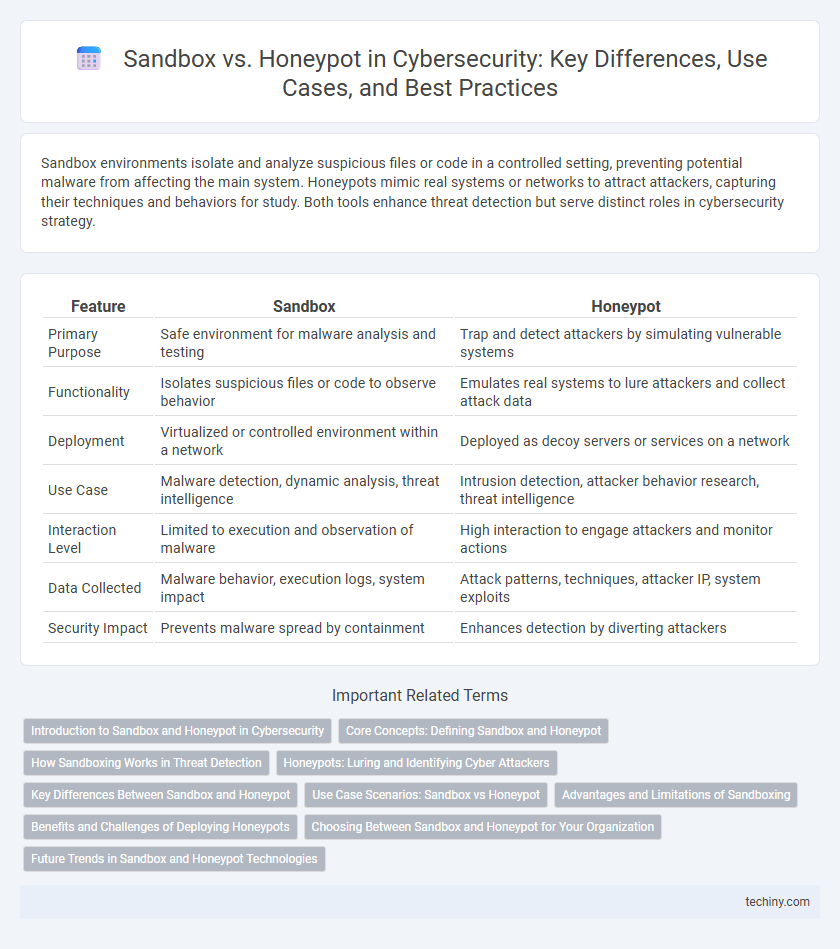
| Feature | Sandbox | Honeypot |
|---|---|---|
| Primary Purpose | Safe environment for malware analysis and testing | Trap and detect attackers by simulating vulnerable systems |
| Functionality | Isolates suspicious files or code to observe behavior | Emulates real systems to lure attackers and collect attack data |
| Deployment | Virtualized or controlled environment within a network | Deployed as decoy servers or services on a network |
| Use Case | Malware detection, dynamic analysis, threat intelligence | Intrusion detection, attacker behavior research, threat intelligence |
| Interaction Level | Limited to execution and observation of malware | High interaction to engage attackers and monitor actions |
| Data Collected | Malware behavior, execution logs, system impact | Attack patterns, techniques, attacker IP, system exploits |
| Security Impact | Prevents malware spread by containment | Enhances detection by diverting attackers |
Introduction to Sandbox and Honeypot in Cybersecurity
A sandbox in cybersecurity is an isolated environment designed to safely execute and analyze suspicious code without risking the host system, often used for malware detection and behavior analysis. A honeypot is a decoy system deliberately configured to attract and trap attackers, enabling security teams to monitor attack methods and gather intelligence. Both tools enhance threat detection but serve distinct roles, with sandboxes focusing on containment and analysis, while honeypots are used for deception and intelligence gathering.
Core Concepts: Defining Sandbox and Honeypot
A sandbox is a controlled and isolated environment designed to safely execute and analyze suspicious code or applications without risking the host system. A honeypot acts as a decoy system or network resource intentionally exposed to attackers to detect, monitor, and study malicious activities. Both tools enhance cybersecurity by providing insights into threats but serve distinct purposes: sandboxes focus on malware analysis, while honeypots emphasize intrusion detection and threat intelligence gathering.
How Sandboxing Works in Threat Detection
Sandboxing isolates suspicious files or code in a controlled virtual environment to observe their behavior without risking the host system's security. By executing potentially malicious programs in this contained space, sandbox solutions identify malware signatures, anomalous activities, and zero-day threats in real time. This proactive threat detection method helps cybersecurity teams analyze unknown threats, enabling faster incident response and reducing false positives.
Honeypots: Luring and Identifying Cyber Attackers
Honeypots serve as decoy systems designed to lure cyber attackers by mimicking vulnerable network resources, enabling the capture of attack patterns and techniques in real-time. They provide critical insights into attacker behavior, including malware deployment methods and exploit attempts, facilitating proactive threat intelligence. By isolating attacker activity, honeypots reduce the risk to legitimate systems while enhancing incident response and cybersecurity defenses.
Key Differences Between Sandbox and Honeypot
A sandbox is an isolated environment designed to safely execute and analyze suspicious code or applications without affecting the host system, while a honeypot is a decoy network resource intended to attract and trap attackers to study their behavior and gather threat intelligence. Sandboxes prioritize dynamic malware analysis by observing real-time interactions within a controlled space, whereas honeypots focus on deception and detection by mimicking vulnerable systems to lure adversaries. Key differences include their purpose--sandboxing emphasizes containment and analysis, whereas honeypots emphasize threat intelligence and attack tracking--and deployment, with sandboxes often running in virtualized or containerized settings and honeypots integrated into actual network environments.
Use Case Scenarios: Sandbox vs Honeypot
Sandboxes are primarily used to safely execute and analyze suspicious files or code in a controlled environment, preventing potential malware from affecting production systems. Honeypots serve as decoy systems designed to attract and monitor attackers, capturing data on intrusion techniques and behavior for threat intelligence purposes. While sandboxes focus on dynamic malware analysis and prevention, honeypots emphasize deception and proactive threat detection in cybersecurity defense strategies.
Advantages and Limitations of Sandboxing
Sandboxing enhances cybersecurity by isolating suspicious code or files within a controlled environment, minimizing the risk of malware spreading to critical systems. Its advantages include safe analysis of unknown threats, real-time behavior monitoring, and effective prevention of zero-day attacks. Limitations involve resource-intensive setups, potential evasion by sophisticated malware, and failure to replicate complex system interactions accurately.
Benefits and Challenges of Deploying Honeypots
Honeypots offer significant benefits in cybersecurity by attracting and isolating malicious attackers, enabling detailed analysis of attack methods and improving threat intelligence. They enhance early threat detection and reduce false positives by mimicking vulnerable systems, but challenges include the risk of being exploited as a launchpad for further attacks and the need for constant monitoring and maintenance to ensure effectiveness. Deploying honeypots requires careful resource allocation and expertise to interpret captured data accurately while avoiding legal and ethical issues.
Choosing Between Sandbox and Honeypot for Your Organization
Choosing between a sandbox and a honeypot depends on your organization's cybersecurity goals; sandboxes provide isolated environments for safely analyzing suspicious files or code, while honeypots attract and monitor attacker behavior to gather intelligence. Sandboxes excel in malware detection and behavioral analysis without risk to production systems, whereas honeypots offer insight into attacker tactics but require careful configuration to avoid becoming security liabilities. Evaluating factors like threat intelligence needs, resource availability, and risk tolerance will guide the optimal deployment of these defensive technologies.
Future Trends in Sandbox and Honeypot Technologies
Future trends in sandbox and honeypot technologies emphasize enhanced AI-driven behavior analysis to detect sophisticated cyber threats in real-time. Integration of cloud-native architectures allows scalable deployment and improved interaction capturing across diverse environments. Advances in machine learning algorithms enable dynamic adaptation to evolving attack strategies, increasing the effectiveness of threat containment and intelligence gathering.
Sandbox vs Honeypot Infographic
 techiny.com
techiny.com