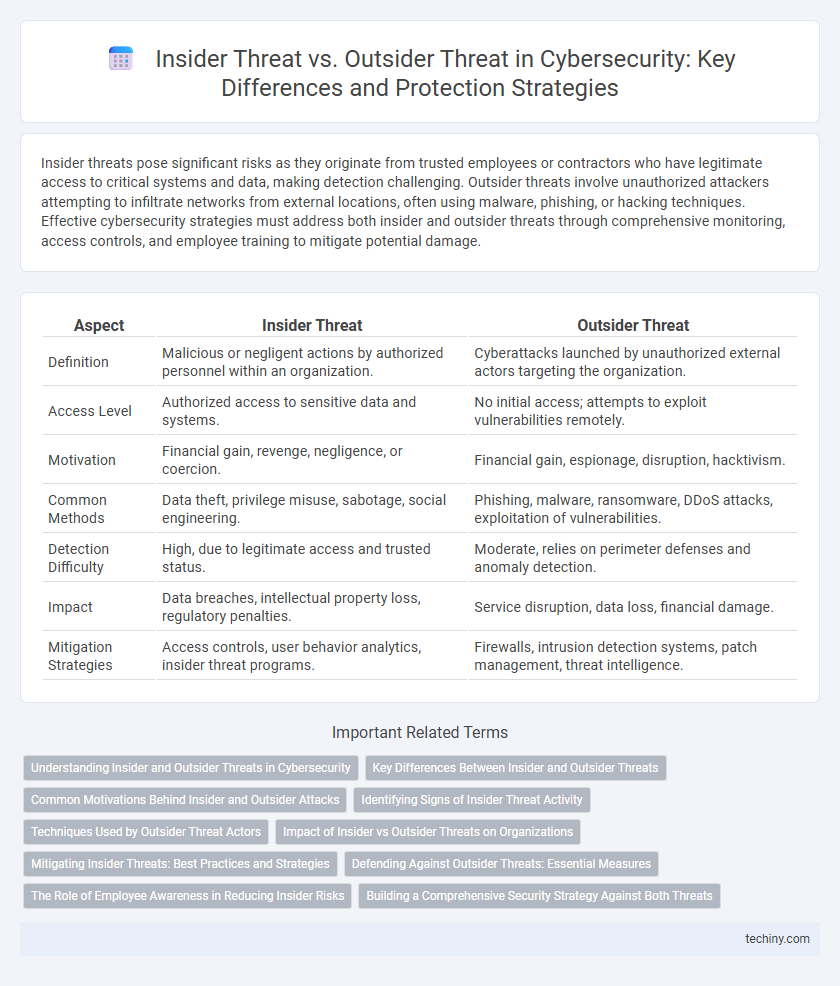
Insider threats pose significant risks as they originate from trusted employees or contractors who have legitimate access to critical systems and data, making detection challenging. Outsider threats involve unauthorized attackers attempting to infiltrate networks from external locations, often using malware, phishing, or hacking techniques. Effective cybersecurity strategies must address both insider and outsider threats through comprehensive monitoring, access controls, and employee training to mitigate potential damage.
Table of Comparison
| Aspect | Insider Threat | Outsider Threat |
|---|---|---|
| Definition | Malicious or negligent actions by authorized personnel within an organization. | Cyberattacks launched by unauthorized external actors targeting the organization. |
| Access Level | Authorized access to sensitive data and systems. | No initial access; attempts to exploit vulnerabilities remotely. |
| Motivation | Financial gain, revenge, negligence, or coercion. | Financial gain, espionage, disruption, hacktivism. |
| Common Methods | Data theft, privilege misuse, sabotage, social engineering. | Phishing, malware, ransomware, DDoS attacks, exploitation of vulnerabilities. |
| Detection Difficulty | High, due to legitimate access and trusted status. | Moderate, relies on perimeter defenses and anomaly detection. |
| Impact | Data breaches, intellectual property loss, regulatory penalties. | Service disruption, data loss, financial damage. |
| Mitigation Strategies | Access controls, user behavior analytics, insider threat programs. | Firewalls, intrusion detection systems, patch management, threat intelligence. |
Understanding Insider and Outsider Threats in Cybersecurity
Insider threats originate from within an organization, involving employees, contractors, or partners with legitimate access who misuse their privileges to cause harm. Outsider threats come from external actors like hackers, cybercriminals, or state-sponsored groups attempting unauthorized access through phishing, malware, or exploitation of vulnerabilities. Effective cybersecurity strategies require comprehensive detection and mitigation measures addressing both insider misuse and external attacks to protect sensitive data and maintain system integrity.
Key Differences Between Insider and Outsider Threats
Insider threats originate from individuals within an organization who have authorized access, often exploiting their privileges to cause harm or steal data, whereas outsider threats come from external attackers aiming to breach security defenses. Insider threats typically involve deliberate abuse or negligence by employees, contractors, or partners, while outsider threats rely on techniques like phishing, malware, or hacking to gain unauthorized access. Understanding these key differences enables organizations to implement tailored security measures such as access controls, user behavior monitoring, and robust perimeter defenses to mitigate both risk types effectively.
Common Motivations Behind Insider and Outsider Attacks
Insider threats often stem from motivations such as financial gain, revenge, or coercion, leveraging privileged access to exploit organizational vulnerabilities. Outsider threats are commonly driven by financial profit, political motives, or espionage, targeting systems through malware, phishing, or hacking techniques. Understanding these distinct motivations enhances the development of tailored cybersecurity strategies to mitigate risks effectively.
Identifying Signs of Insider Threat Activity
Identifying signs of insider threat activity involves monitoring unusual access patterns, such as employees accessing sensitive data outside of their job scope or working hours. Increased data downloads, unauthorized use of privileged accounts, and inconsistent behavior changes, like sudden disinterest or disgruntlement, often signal potential insider risks. Effective detection relies on continuous behavioral analytics and integration of endpoint monitoring tools to spot deviations from normal user activities.
Techniques Used by Outsider Threat Actors
Outsider threat actors primarily use techniques such as phishing, malware deployment, and exploitation of software vulnerabilities to infiltrate networks. These attackers often employ social engineering tactics to manipulate employees into revealing sensitive information or downloading malicious software. Advanced methods include zero-day exploits and DDoS attacks aimed at disrupting operations and gaining unauthorized access to systems.
Impact of Insider vs Outsider Threats on Organizations
Insider threats often result in more severe organizational damage due to the attacker's access to sensitive systems and knowledge of internal processes, enabling targeted and stealthy attacks. Outsider threats typically rely on exploiting external vulnerabilities, causing disruptions like data breaches and ransomware attacks, which can be mitigated with perimeter defenses. Understanding the distinct impacts helps organizations prioritize internal monitoring and strengthen perimeter security to reduce overall risk.
Mitigating Insider Threats: Best Practices and Strategies
Mitigating insider threats requires implementing comprehensive access controls, continuous monitoring, and employee training programs designed to recognize suspicious behavior and potential policy violations. Employing advanced behavioral analytics and data loss prevention (DLP) tools helps identify anomalies that signal insider risks, while establishing clear incident response protocols ensures swift containment and remediation. Regular audits and fostering a security-aware organizational culture reduce vulnerabilities posed by insiders with malicious intent or negligent actions.
Defending Against Outsider Threats: Essential Measures
Robust firewall configurations and intrusion detection systems are critical in defending against outsider threats by monitoring and blocking unauthorized access attempts. Implementing multi-factor authentication (MFA) strengthens security by requiring multiple verification steps to access sensitive systems. Regular software updates and patch management close vulnerabilities that cybercriminals commonly exploit in outsider attack vectors.
The Role of Employee Awareness in Reducing Insider Risks
Employee awareness plays a critical role in reducing insider threats by empowering staff to recognize and report suspicious activities, thereby preventing potential data breaches and sabotage. Training programs focused on identifying phishing, social engineering, and unusual access behaviors significantly decrease the risk of malicious insider actions. Organizations that invest in continuous awareness campaigns experience fewer insider-related incidents compared to those relying solely on technical defenses.
Building a Comprehensive Security Strategy Against Both Threats
A comprehensive cybersecurity strategy integrates advanced monitoring tools and employee training to detect and mitigate insider threats, such as data leaks or unauthorized access by trusted personnel. Simultaneously, robust perimeter defenses like firewalls, intrusion detection systems, and threat intelligence platforms are essential to defend against outsider threats, including cyberattacks from hackers and malware infiltration. Combining internal behavior analysis with external attack prevention creates a resilient security posture that addresses the full spectrum of potential breaches.
Insider Threat vs Outsider Threat Infographic
 techiny.com
techiny.com