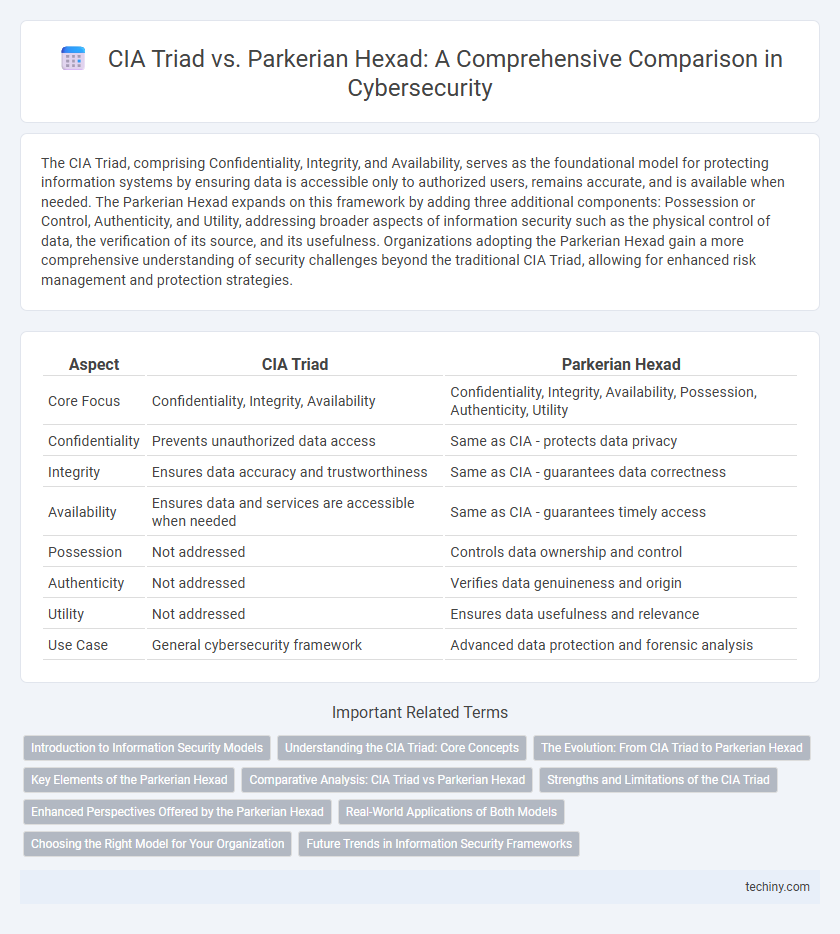
The CIA Triad, comprising Confidentiality, Integrity, and Availability, serves as the foundational model for protecting information systems by ensuring data is accessible only to authorized users, remains accurate, and is available when needed. The Parkerian Hexad expands on this framework by adding three additional components: Possession or Control, Authenticity, and Utility, addressing broader aspects of information security such as the physical control of data, the verification of its source, and its usefulness. Organizations adopting the Parkerian Hexad gain a more comprehensive understanding of security challenges beyond the traditional CIA Triad, allowing for enhanced risk management and protection strategies.
Table of Comparison
| Aspect | CIA Triad | Parkerian Hexad |
|---|---|---|
| Core Focus | Confidentiality, Integrity, Availability | Confidentiality, Integrity, Availability, Possession, Authenticity, Utility |
| Confidentiality | Prevents unauthorized data access | Same as CIA - protects data privacy |
| Integrity | Ensures data accuracy and trustworthiness | Same as CIA - guarantees data correctness |
| Availability | Ensures data and services are accessible when needed | Same as CIA - guarantees timely access |
| Possession | Not addressed | Controls data ownership and control |
| Authenticity | Not addressed | Verifies data genuineness and origin |
| Utility | Not addressed | Ensures data usefulness and relevance |
| Use Case | General cybersecurity framework | Advanced data protection and forensic analysis |
Introduction to Information Security Models
The CIA Triad, comprising Confidentiality, Integrity, and Availability, forms the foundational framework for information security models by emphasizing data protection and access controls. In contrast, the Parkerian Hexad expands this framework to include Confidentiality, Possession or Control, Integrity, Authenticity, Availability, and Utility, offering a more comprehensive approach to addressing modern cybersecurity challenges. Understanding these models is crucial for designing robust security strategies that safeguard information assets against diverse threats.
Understanding the CIA Triad: Core Concepts
The CIA Triad, comprising Confidentiality, Integrity, and Availability, forms the foundational framework for cybersecurity principles, ensuring that sensitive information is protected from unauthorized access, remains accurate and unaltered, and is accessible to authorized users when needed. Confidentiality restricts data exposure through encryption and access controls, Integrity maintains data accuracy via hashing and auditing mechanisms, and Availability guarantees system uptime through redundancy and disaster recovery plans. Understanding these core concepts enables organizations to build robust security strategies that address risk management and compliance requirements effectively.
The Evolution: From CIA Triad to Parkerian Hexad
The evolution from the CIA Triad to the Parkerian Hexad reflects a shift towards a more comprehensive framework in cybersecurity, expanding beyond confidentiality, integrity, and availability to include authenticity, possession, and utility. This progression addresses modern security challenges by incorporating concepts that tackle data theft, manipulation, and true ownership verification. Organizations adopting the Parkerian Hexad benefit from enhanced risk management and more robust defense strategies tailored to complex cyber threats.
Key Elements of the Parkerian Hexad
The Parkerian Hexad expands on the traditional CIA Triad by including six key elements: Confidentiality, Integrity, Availability, Authenticity, Possession (or Control), and Utility, providing a more comprehensive framework for cybersecurity. Authenticity ensures that data and communications are genuine and from verified sources, while Possession addresses the physical or digital control over information, which the CIA Triad does not explicitly cover. Utility measures the usefulness or value of the information, emphasizing the importance of data being not only secure but also effective for its intended purpose.
Comparative Analysis: CIA Triad vs Parkerian Hexad
The CIA Triad, comprising Confidentiality, Integrity, and Availability, serves as the foundational model for cybersecurity principles, emphasizing protection of information assets against unauthorized access, alteration, and downtime. The Parkerian Hexad expands this framework by including Authenticity, Possession, and Utility, offering a more comprehensive approach to securing information beyond traditional parameters. Comparative analysis reveals that while the CIA Triad focuses on fundamental security objectives, the Parkerian Hexad addresses additional dimensions that enhance the robustness of information security strategies in complex threat landscapes.
Strengths and Limitations of the CIA Triad
The CIA Triad, consisting of Confidentiality, Integrity, and Availability, provides a foundational model for cybersecurity by focusing on protecting sensitive information, ensuring data accuracy, and maintaining system uptime. Its strength lies in its simplicity and universal applicability across various security frameworks, making it a widely adopted standard for risk management. However, the CIA Triad's limitation is its narrow scope, as it does not address additional security attributes such as accountability, authenticity, and utility, which are encompassed by more comprehensive models like the Parkerian Hexad.
Enhanced Perspectives Offered by the Parkerian Hexad
The Parkerian Hexad expands traditional cybersecurity frameworks by incorporating six core attributes: Confidentiality, Integrity, Availability, Authenticity, Privacy, and Utility, offering a more comprehensive approach than the CIA Triad's three principles. This enhanced perspective addresses modern threats by emphasizing data authenticity and utility alongside privacy concerns, thereby improving security policy design and risk management. Organizations adopting the Parkerian Hexad benefit from a multidimensional model that better aligns with complex information environments and emerging cyber threats.
Real-World Applications of Both Models
The CIA Triad, emphasizing Confidentiality, Integrity, and Availability, serves as the foundational framework for most cybersecurity policies, guiding organizations in protecting sensitive data and ensuring system uptime. The Parkerian Hexad expands this model by integrating additional principles such as Possession, Authenticity, and Utility, addressing more nuanced security challenges like data ownership and trust verification in real-world scenarios. Enterprises deploy the CIA Triad for general data protection while leveraging the Parkerian Hexad to enhance defense mechanisms against insider threats, data manipulation, and complex cyber-attacks.
Choosing the Right Model for Your Organization
Selecting the appropriate security framework depends on your organization's risk profile and information asset complexity. The CIA Triad--Confidentiality, Integrity, and Availability--provides a foundational model ideal for most general cybersecurity strategies. In contrast, the Parkerian Hexad expands these principles by including Possession, Authenticity, and Utility, offering a more comprehensive approach for environments requiring nuanced data protection and advanced threat mitigation.
Future Trends in Information Security Frameworks
Emerging information security frameworks are evolving beyond the traditional CIA Triad--confidentiality, integrity, and availability--by integrating the Parkerian Hexad, which adds authenticity, possession, and utility to address modern cyber threats. Future trends emphasize holistic protection mechanisms that incorporate data authenticity and control over information assets to counteract sophisticated cyber attacks and insider threats. Advanced frameworks leveraging AI-driven risk assessments and adaptive security policies are set to redefine resilience in cybersecurity governance.
CIA Triad vs Parkerian Hexad Infographic
 techiny.com
techiny.com