Man-in-the-Middle (MITM) attacks involve an attacker secretly intercepting and potentially altering communications between two parties, compromising data integrity and confidentiality. Spoofing, on the other hand, involves impersonating a legitimate entity to deceive systems or users, often as a precursor to more complex attacks like MITM. Understanding the distinctions between MITM and spoofing enhances the development of targeted cybersecurity defenses and intrusion detection strategies.
Table of Comparison
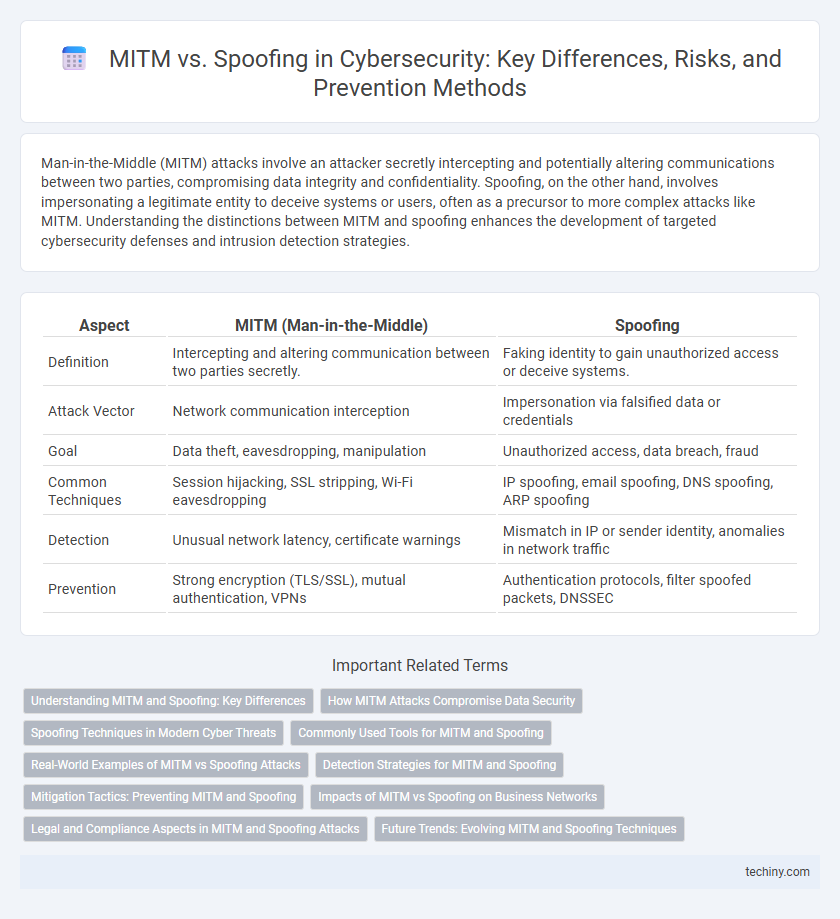
| Aspect | MITM (Man-in-the-Middle) | Spoofing |
|---|---|---|
| Definition | Intercepting and altering communication between two parties secretly. | Faking identity to gain unauthorized access or deceive systems. |
| Attack Vector | Network communication interception | Impersonation via falsified data or credentials |
| Goal | Data theft, eavesdropping, manipulation | Unauthorized access, data breach, fraud |
| Common Techniques | Session hijacking, SSL stripping, Wi-Fi eavesdropping | IP spoofing, email spoofing, DNS spoofing, ARP spoofing |
| Detection | Unusual network latency, certificate warnings | Mismatch in IP or sender identity, anomalies in network traffic |
| Prevention | Strong encryption (TLS/SSL), mutual authentication, VPNs | Authentication protocols, filter spoofed packets, DNSSEC |
Understanding MITM and Spoofing: Key Differences
Man-in-the-Middle (MITM) attacks involve an attacker intercepting and possibly altering communication between two parties without their knowledge, compromising data integrity and confidentiality. Spoofing attacks impersonate another device or user by falsifying data, such as IP addresses or email headers, to gain unauthorized access or deceive the target. Understanding these distinctions is crucial for implementing targeted cybersecurity defenses like encrypted channels to prevent MITM and authentication protocols to mitigate spoofing risks.
How MITM Attacks Compromise Data Security
MITM attacks compromise data security by intercepting and altering communications between two parties without their knowledge, enabling attackers to steal sensitive information like login credentials, financial data, and personal details. Unlike spoofing, which involves impersonation to trick users or systems, MITM attacks actively manipulate the data stream, making detection more difficult. This ongoing interception undermines encryption protocols and authentication processes, leading to significant breaches in confidentiality and data integrity.
Spoofing Techniques in Modern Cyber Threats
Spoofing techniques in modern cyber threats involve attackers impersonating legitimate entities by falsifying data such as IP addresses, email headers, or website URLs to deceive victims and gain unauthorized access. Common methods include email spoofing, DNS spoofing, and ARP spoofing, each exploiting specific network vulnerabilities to intercept sensitive information or redirect traffic. Advanced spoofing attacks leverage social engineering combined with automated tools to bypass traditional security measures, making detection and prevention increasingly challenging for organizations.
Commonly Used Tools for MITM and Spoofing
Commonly used tools for Man-in-the-Middle (MITM) attacks include Ettercap, Cain & Abel, and Wireshark, which enable attackers to intercept and analyze network traffic in real-time. Spoofing attacks often utilize tools like ARPspoof, Scapy, and Nmap to manipulate network packets and impersonate legitimate devices or users. Both MITM and spoofing tools leverage vulnerabilities in network protocols to compromise data integrity and confidentiality.
Real-World Examples of MITM vs Spoofing Attacks
The 2013 Target data breach exemplifies a Man-in-the-Middle (MITM) attack where hackers intercepted network communications to steal credit card information. In contrast, the 2020 Twitter Bitcoin scam demonstrated spoofing by compromising employee credentials to impersonate high-profile accounts and deceive users into sending cryptocurrency. These real-world incidents highlight how MITM attacks exploit intercepted data streams while spoofing manipulates identity to achieve unauthorized access.
Detection Strategies for MITM and Spoofing
Detecting Man-in-the-Middle (MITM) attacks involves monitoring network traffic for anomalies such as unexpected SSL/TLS certificate changes and ARP spoofing patterns, using tools like intrusion detection systems (IDS) and packet analyzers. Spoofing attack detection relies on techniques like verifying IP and MAC address consistency, employing network access control (NAC) systems, and analyzing DNS request patterns with anomaly-based detection software. Both strategies emphasize real-time traffic analysis and behavioral monitoring to quickly identify and mitigate unauthorized interception or impersonation attempts.
Mitigation Tactics: Preventing MITM and Spoofing
Effective mitigation tactics for preventing Man-in-the-Middle (MITM) attacks and spoofing include implementing strong encryption protocols such as TLS to secure data in transit and employing multi-factor authentication (MFA) to verify user identities. Network segmentation and the use of Intrusion Detection Systems (IDS) help monitor and isolate anomalous traffic patterns associated with spoofing attempts. Regular software updates and strict validation of digital certificates also play a critical role in minimizing vulnerabilities exploited during MITM and spoofing attacks.
Impacts of MITM vs Spoofing on Business Networks
MITM (Man-in-the-Middle) attacks often result in severe data breaches by intercepting and altering communications within business networks, compromising confidentiality and integrity. Spoofing primarily undermines trust by masquerading as legitimate devices or users, leading to unauthorized access and potential spread of malware. Both threats disrupt network availability and can cause significant financial losses, regulatory penalties, and damage to corporate reputation.
Legal and Compliance Aspects in MITM and Spoofing Attacks
Man-in-the-Middle (MITM) and spoofing attacks present significant legal and compliance challenges under regulations such as GDPR, HIPAA, and PCI-DSS, which mandate stringent data protection measures and breach notification protocols. Organizations must implement robust authentication and encryption mechanisms to comply with these standards and avoid hefty penalties linked to unauthorized data interception or identity falsification. Failure to address vulnerabilities related to MITM and spoofing can result in litigation, regulatory fines, and reputational damage, emphasizing the critical need for proactive cybersecurity policies.
Future Trends: Evolving MITM and Spoofing Techniques
Emerging MITM and spoofing techniques increasingly exploit AI-driven automation and advanced encryption bypass methods, elevating the sophistication of cyberattacks. Quantum computing advancements threaten current cryptographic defenses, prompting the development of quantum-resistant protocols to counteract future interception and identity spoofing. Adaptive AI-powered threat detection systems are becoming essential to identify and mitigate these evolving man-in-the-middle and spoofing attacks in real time.
MITM vs Spoofing Infographic
 techiny.com
techiny.com