Insider threats pose unique challenges because they originate from trusted individuals with legitimate access, making detection and mitigation more complex compared to external threats that rely on exploiting vulnerabilities from outside the organization. External threats often involve hackers using malware, phishing, or network attacks to breach defenses, whereas insider threats can leverage intimate knowledge of internal systems to bypass security measures stealthily. Effective cybersecurity strategies must integrate behavioral monitoring and robust access controls to address insider risks alongside traditional perimeter defenses against external attacks.
Table of Comparison
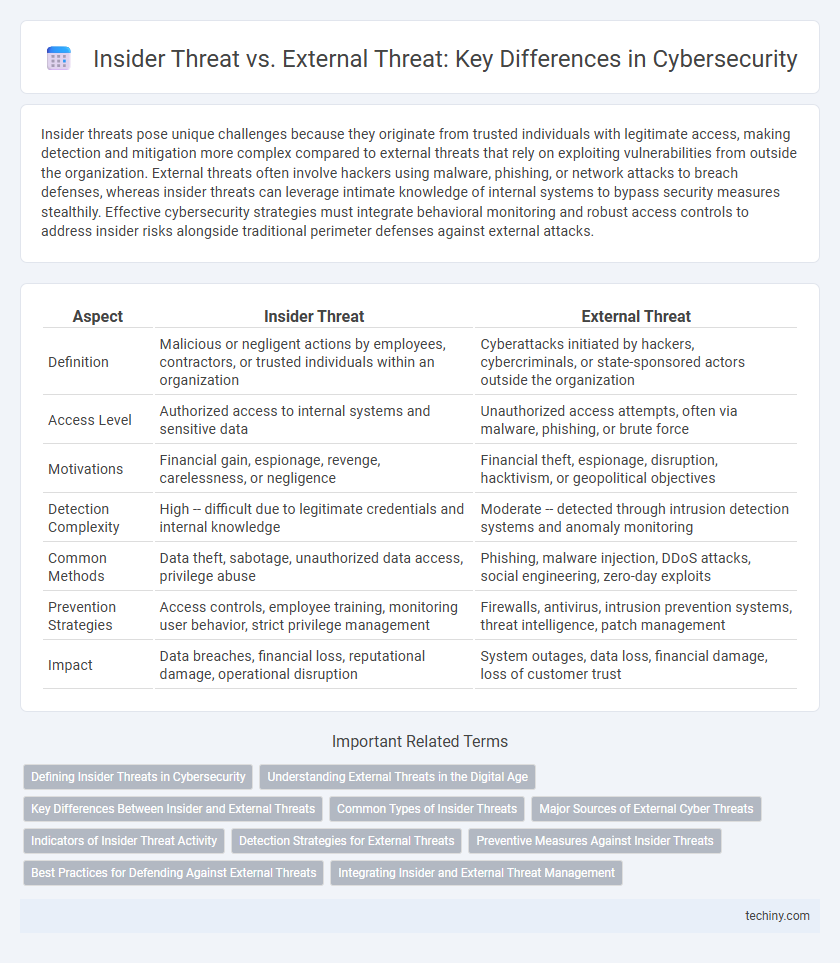
| Aspect | Insider Threat | External Threat |
|---|---|---|
| Definition | Malicious or negligent actions by employees, contractors, or trusted individuals within an organization | Cyberattacks initiated by hackers, cybercriminals, or state-sponsored actors outside the organization |
| Access Level | Authorized access to internal systems and sensitive data | Unauthorized access attempts, often via malware, phishing, or brute force |
| Motivations | Financial gain, espionage, revenge, carelessness, or negligence | Financial theft, espionage, disruption, hacktivism, or geopolitical objectives |
| Detection Complexity | High -- difficult due to legitimate credentials and internal knowledge | Moderate -- detected through intrusion detection systems and anomaly monitoring |
| Common Methods | Data theft, sabotage, unauthorized data access, privilege abuse | Phishing, malware injection, DDoS attacks, social engineering, zero-day exploits |
| Prevention Strategies | Access controls, employee training, monitoring user behavior, strict privilege management | Firewalls, antivirus, intrusion prevention systems, threat intelligence, patch management |
| Impact | Data breaches, financial loss, reputational damage, operational disruption | System outages, data loss, financial damage, loss of customer trust |
Defining Insider Threats in Cybersecurity
Insider threats in cybersecurity involve individuals within an organization who have authorized access and intentionally or unintentionally cause harm by leaking data, sabotaging systems, or facilitating unauthorized access. These threats often evade traditional security measures due to their inherent trust and knowledge of internal processes, making detection more challenging compared to external cyberattacks. Understanding insider threat vectors, including disgruntled employees, negligent insiders, and compromised credentials, is crucial for implementing effective monitoring and mitigation strategies.
Understanding External Threats in the Digital Age
External threats in cybersecurity primarily originate from hackers, cybercriminals, and nation-state actors exploiting vulnerabilities in network infrastructure, software, and human behavior. These threats often involve phishing attacks, malware, ransomware, and Distributed Denial of Service (DDoS) campaigns designed to disrupt services, steal data, or demand ransom. Understanding external threats requires continuous monitoring of threat intelligence, implementing advanced firewalls, intrusion detection systems, and promoting cybersecurity awareness to mitigate risks in the evolving digital landscape.
Key Differences Between Insider and External Threats
Insider threats originate from within an organization, often involving trusted employees or contractors who misuse access for malicious purposes, while external threats come from outside actors such as hackers or cybercriminals seeking to exploit vulnerabilities. Insider threats typically leverage legitimate credentials, making detection challenging, whereas external threats rely on breaching defenses like firewalls or phishing attacks. Understanding these distinctions is critical for developing targeted cybersecurity strategies and implementing effective access controls and monitoring systems.
Common Types of Insider Threats
Common types of insider threats include malicious insiders who deliberately steal or sabotage data, negligent insiders who unintentionally cause security breaches through careless actions, and compromised insiders whose credentials are exploited by external attackers. These threats often manifest through unauthorized data access, privilege abuse, and insider fraud, posing significant risks to organizational cybersecurity. Understanding these categories is critical for implementing effective insider threat detection and prevention strategies.
Major Sources of External Cyber Threats
Major sources of external cyber threats include state-sponsored hackers, cybercriminal organizations, and hacktivist groups, each leveraging sophisticated malware, phishing campaigns, and ransomware attacks to compromise networks. External threats often exploit vulnerabilities in software and hardware, relying on social engineering and zero-day exploits to infiltrate systems. As external attacks increase in frequency and complexity, organizations must prioritize real-time threat intelligence and robust perimeter defenses to mitigate risks effectively.
Indicators of Insider Threat Activity
Unusual access patterns, such as employees downloading excessive sensitive data or accessing systems outside normal hours, often signal insider threat activity. Frequent use of unauthorized devices, unexplained privilege escalations, and anomalous data transfers to external locations are critical indicators. Behavioral changes, including increased disgruntlement or attempts to bypass security protocols, further heighten suspicion of internal compromise.
Detection Strategies for External Threats
Detection strategies for external threats in cybersecurity heavily rely on advanced intrusion detection systems (IDS) and real-time network monitoring to identify suspicious activities. Techniques such as anomaly detection, signature-based detection, and behavioral analytics enable organizations to swiftly recognize and mitigate external cyberattacks like malware, phishing, and distributed denial-of-service (DDoS) attacks. Leveraging threat intelligence feeds and machine learning algorithms enhances the accuracy of detecting unknown external threats and reduces false positives.
Preventive Measures Against Insider Threats
Implementing strict access controls and continuous monitoring can significantly reduce the risk of insider threats by limiting unauthorized data access and detecting suspicious behavior early. Employee training programs focused on cybersecurity awareness and clear policies on data handling help establish a security-conscious culture that discourages malicious actions. Regular audits and the use of behavior analytics tools further enhance the ability to identify potential insider threats before they cause substantial damage.
Best Practices for Defending Against External Threats
Organizations should implement multi-layered security measures such as firewalls, intrusion detection systems, and regular patch management to defend against external threats. Employee training on phishing, strong password policies, and network segmentation further reduce vulnerability to cyberattacks originating outside the organization. Continuous monitoring and incident response plans are essential to quickly identify and mitigate external intrusions.
Integrating Insider and External Threat Management
Integrating insider and external threat management enhances cybersecurity by providing a holistic defense strategy against multifaceted attacks. Combining behavioral analytics for insider detection with advanced perimeter security strengthens threat identification and response capabilities. Unified threat intelligence platforms enable seamless monitoring, reducing blind spots and accelerating mitigation efforts.
Insider Threat vs External Threat Infographic
 techiny.com
techiny.com