A honeypot is a single isolated system designed to attract and analyze malicious activity, providing insights into attacker behavior and techniques. In contrast, a honeynet consists of a network of interconnected honeypots that simulate a full production environment, increasing the complexity and realism to capture more sophisticated cyber threats. Deploying a honeynet enables more comprehensive threat detection and analysis by observing attacker movements and strategies across multiple systems.
Table of Comparison
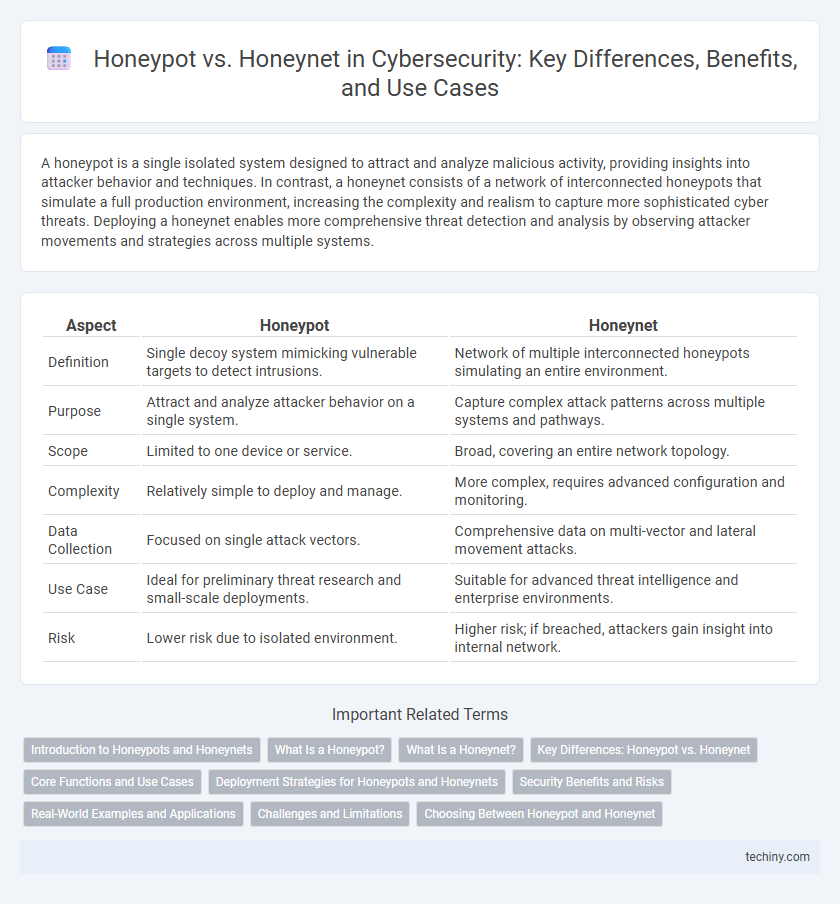
| Aspect | Honeypot | Honeynet |
|---|---|---|
| Definition | Single decoy system mimicking vulnerable targets to detect intrusions. | Network of multiple interconnected honeypots simulating an entire environment. |
| Purpose | Attract and analyze attacker behavior on a single system. | Capture complex attack patterns across multiple systems and pathways. |
| Scope | Limited to one device or service. | Broad, covering an entire network topology. |
| Complexity | Relatively simple to deploy and manage. | More complex, requires advanced configuration and monitoring. |
| Data Collection | Focused on single attack vectors. | Comprehensive data on multi-vector and lateral movement attacks. |
| Use Case | Ideal for preliminary threat research and small-scale deployments. | Suitable for advanced threat intelligence and enterprise environments. |
| Risk | Lower risk due to isolated environment. | Higher risk; if breached, attackers gain insight into internal network. |
Introduction to Honeypots and Honeynets
Honeypots are decoy systems designed to attract and analyze cyber attackers by simulating vulnerable targets, enabling security teams to monitor attack techniques and gather intelligence. Honeynets extend this concept by creating entire networks of interconnected honeypots, providing a more comprehensive environment to study attacker behaviors and malware propagation. Both play crucial roles in proactive cybersecurity strategies by enhancing threat detection and improving defensive measures.
What Is a Honeypot?
A honeypot is a cybersecurity mechanism designed to lure attackers by simulating vulnerable systems, capturing their techniques and tactics for analysis. It serves as a decoy to detect, deflect, or study unauthorized access attempts without risking actual production assets. By isolating malicious activity, honeypots help improve threat intelligence and strengthen an organization's defensive posture.
What Is a Honeynet?
A honeynet is an advanced cybersecurity tool consisting of multiple interconnected honeypots designed to simulate an entire network environment, attracting and analyzing cyber attackers in real-time. It provides comprehensive insights into attack strategies, malware behavior, and intrusion methods by capturing data across various network nodes, enabling proactive defense mechanisms. Unlike a single honeypot, a honeynet offers a broader scope for threat intelligence and enhances detection capabilities across complex network infrastructures.
Key Differences: Honeypot vs. Honeynet
A honeypot is a singular decoy system designed to attract and analyze cyber attackers, while a honeynet consists of multiple interconnected honeypots that simulate an entire network environment for more comprehensive threat detection. Honeynets provide richer insights by capturing attacker behaviors across various network segments, whereas honeypots typically gather limited data from isolated targets. The complexity of deployment and maintenance is higher for honeynets, but they offer enhanced visibility into coordinated, multi-vector attacks compared to standalone honeypots.
Core Functions and Use Cases
Honeypots serve as decoy systems designed to attract and analyze potential cyber threats by simulating vulnerabilities, primarily used for detecting and researching individual attack vectors. Honeynets expand this concept into a network of interconnected honeypots, providing a comprehensive environment to monitor complex attack behaviors and lateral movements within a simulated infrastructure. Core functions of honeypots emphasize isolated threat intelligence collection, while honeynets focus on detailed attack pattern analysis and improving intrusion detection systems across enterprise networks.
Deployment Strategies for Honeypots and Honeynets
Honeypots are typically deployed as isolated systems emulating vulnerable targets to detect and analyze attacker tactics, often integrated within existing network segments for targeted threat intelligence gathering. Honeynets consist of multiple interconnected honeypots that simulate entire network environments, requiring strategic placement across network layers to capture complex multi-stage attack behaviors and lateral movement patterns. Effective deployment strategies for honeypots and honeynets emphasize minimizing detection risk by attackers, leveraging virtualization for scalability, and ensuring comprehensive logging for forensic analysis.
Security Benefits and Risks
Honeypots simulate isolated systems to attract and analyze cyber threats, enhancing intrusion detection and threat intelligence by capturing attacker behavior in a controlled environment. Honeynets extend this concept by deploying interconnected honeypots, providing deeper insights into complex attack vectors and lateral movement within networks but increasing exposure to potential exploitation if not properly managed. The security benefits include early threat identification and improved defense strategies, while risks involve resource consumption, false positives, and possible attacker leverage if the honeypot or honeynet is compromised.
Real-World Examples and Applications
Honeypots like the Cowrie SSH honeypot effectively detect brute-force attacks by simulating vulnerable systems, while honeynets such as the Honeynet Project deploy entire network environments to capture sophisticated multi-stage cyberattacks, providing deeper threat intelligence. Enterprises use honeypots to monitor specific attack vectors and gather malware samples, whereas honeynets enable comprehensive analysis of attacker behavior across multiple systems and protocols in real time. Real-world applications include financial institutions leveraging honeypots to detect credential theft attempts, contrasted with governmental agencies employing honeynets to study advanced persistent threats (APTs) targeting critical infrastructure.
Challenges and Limitations
Honeypots face challenges such as limited scope, often attracting only low-level attacks, which restricts their ability to capture comprehensive threat intelligence. Honeynets, while more expansive by deploying multiple interconnected honeypots, encounter scalability and maintenance complexities that demand significant resources and expertise to manage effectively. Both technologies risk exposing production environments if not properly isolated, posing potential security and operational limitations.
Choosing Between Honeypot and Honeynet
Choosing between a honeypot and a honeynet depends on the scope and complexity of the cybersecurity strategy. A honeypot serves as a single decoy system designed to attract and analyze attacker behavior, providing focused insight into specific threats. In contrast, a honeynet comprises multiple interconnected honeypots, offering a broader, more detailed network environment to monitor sophisticated attacks and gather extensive threat intelligence.
Honeypot vs Honeynet Infographic
 techiny.com
techiny.com