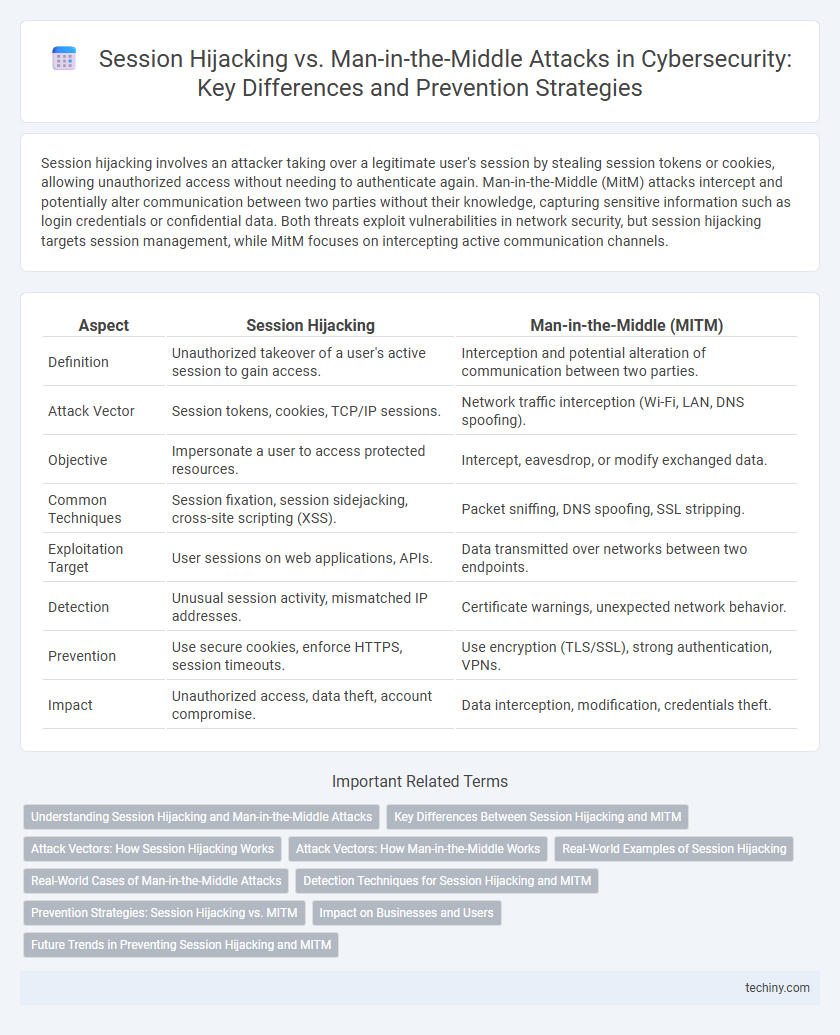
Session hijacking involves an attacker taking over a legitimate user's session by stealing session tokens or cookies, allowing unauthorized access without needing to authenticate again. Man-in-the-Middle (MitM) attacks intercept and potentially alter communication between two parties without their knowledge, capturing sensitive information such as login credentials or confidential data. Both threats exploit vulnerabilities in network security, but session hijacking targets session management, while MitM focuses on intercepting active communication channels.
Table of Comparison
| Aspect | Session Hijacking | Man-in-the-Middle (MITM) |
|---|---|---|
| Definition | Unauthorized takeover of a user's active session to gain access. | Interception and potential alteration of communication between two parties. |
| Attack Vector | Session tokens, cookies, TCP/IP sessions. | Network traffic interception (Wi-Fi, LAN, DNS spoofing). |
| Objective | Impersonate a user to access protected resources. | Intercept, eavesdrop, or modify exchanged data. |
| Common Techniques | Session fixation, session sidejacking, cross-site scripting (XSS). | Packet sniffing, DNS spoofing, SSL stripping. |
| Exploitation Target | User sessions on web applications, APIs. | Data transmitted over networks between two endpoints. |
| Detection | Unusual session activity, mismatched IP addresses. | Certificate warnings, unexpected network behavior. |
| Prevention | Use secure cookies, enforce HTTPS, session timeouts. | Use encryption (TLS/SSL), strong authentication, VPNs. |
| Impact | Unauthorized access, data theft, account compromise. | Data interception, modification, credentials theft. |
Understanding Session Hijacking and Man-in-the-Middle Attacks
Session hijacking involves an attacker taking control of a valid user session to gain unauthorized access, typically by stealing session cookies or tokens. Man-in-the-middle (MITM) attacks intercept and potentially alter communication between two parties without their knowledge, often exploiting unsecured networks or weak encryption. Both attacks compromise data integrity and privacy but differ in their attack vectors and techniques used to exploit session management and network communication vulnerabilities.
Key Differences Between Session Hijacking and MITM
Session hijacking targets an active user session by stealing or manipulating the session ID to gain unauthorized access, whereas Man-in-the-Middle (MITM) attacks intercept and alter the communication between two parties without their knowledge. Session hijacking exploits vulnerabilities in session management protocols, while MITM attacks exploit weaknesses in communication channels such as unsecured Wi-Fi or lack of encryption. The core difference lies in session hijacking focusing on exploiting authenticated sessions, whereas MITM focuses on intercepting and possibly modifying the data exchanged during transmission.
Attack Vectors: How Session Hijacking Works
Session hijacking exploits active communication sessions by intercepting session tokens or cookies, allowing attackers to impersonate legitimate users and gain unauthorized access. Common attack vectors include packet sniffing on unsecured networks, cross-site scripting (XSS) to steal session credentials, and session fixation where attackers force a user's session ID. These vectors enable attackers to bypass authentication and control a victim's session without triggering immediate suspicion.
Attack Vectors: How Man-in-the-Middle Works
Man-in-the-Middle (MitM) attacks exploit vulnerabilities in network communication channels, intercepting and potentially altering data between two parties without their knowledge. Attack vectors include unsecured Wi-Fi networks, DNS spoofing, and ARP poisoning, which redirect traffic through the attacker's system. These methods enable attackers to eavesdrop, inject malicious content, or steal sensitive information during data transmission.
Real-World Examples of Session Hijacking
Session hijacking incidents like the 2018 British Airways breach exposed how attackers exploited vulnerabilities in session tokens to access user accounts and steal payment data. In 2015, the LinkedIn session hijacking attack showed how cybercriminals manipulated session cookies to bypass authentication and extract personal user information. These real-world examples highlight the critical need for robust session management and encryption protocols to defend against unauthorized access and data theft.
Real-World Cases of Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks have targeted major organizations globally, including the 2013 attack on Target, where hackers intercepted payment information via compromised networks. Unlike session hijacking, which takes over an active session, MitM attacks involve attackers secretly relaying and possibly altering communications between two parties, often through public Wi-Fi exploitation or DNS spoofing. Real-world examples emphasize the need for robust encryption protocols, such as TLS, and vigilant network monitoring to prevent unauthorized data interception and manipulation.
Detection Techniques for Session Hijacking and MITM
Effective detection techniques for session hijacking include monitoring abnormal session activities such as unexpected IP address changes and sudden privilege escalations, along with real-time analysis of session tokens for inconsistencies. Man-in-the-middle (MITM) attacks are commonly detected using network traffic analysis tools that identify unusual packet interceptions, SSL/TLS certificate anomalies, and discrepancies in cryptographic handshake procedures. Both methods benefit from continuous behavioral analytics and anomaly detection systems that flag deviations from established network and session baselines to promptly identify intrusions.
Prevention Strategies: Session Hijacking vs. MITM
Employing strong encryption protocols such as TLS and implementing secure cookie attributes like HttpOnly and Secure effectively mitigate risks associated with session hijacking. Utilizing mutual authentication, VPNs, and robust intrusion detection systems enhances defense against Man-in-the-Middle (MITM) attacks. Regular patching of software vulnerabilities alongside user education on phishing and secure network practices are critical components for preventing both session hijacking and MITM threats.
Impact on Businesses and Users
Session hijacking compromises active user sessions, allowing attackers to impersonate legitimate users and gain unauthorized access to sensitive business data, leading to financial losses and reputational damage. Man-in-the-middle attacks intercept and manipulate communications between parties, risking data theft, transaction fraud, and breach of confidential information crucial for business operations. Both threats undermine trust in online services, necessitating robust encryption and real-time monitoring to protect users and ensure business continuity.
Future Trends in Preventing Session Hijacking and MITM
Future trends in preventing session hijacking and man-in-the-middle (MITM) attacks emphasize the integration of artificial intelligence and machine learning to detect anomalous network activities in real-time. Advanced encryption protocols such as TLS 1.3 and zero-trust architectures are becoming critical in minimizing attack surfaces by ensuring end-to-end encryption and continuous verification of all entities involved in a session. The adoption of biometric authentication and blockchain-based identity management further enhances security by making unauthorized session interception and data manipulation increasingly difficult.
Session Hijacking vs Man-in-the-Middle Infographic
 techiny.com
techiny.com