Denylist and allowlist are two fundamental approaches to access control in cybersecurity, each with distinct advantages and applications. A denylist blocks known malicious entities, providing a reactive layer of defense, while an allowlist permits access only to pre-approved, trusted items, offering a proactive and more secure method. Employing allowlists significantly reduces the attack surface by limiting potential threats, whereas denylists require constant updates to remain effective against evolving cyber threats.
Table of Comparison
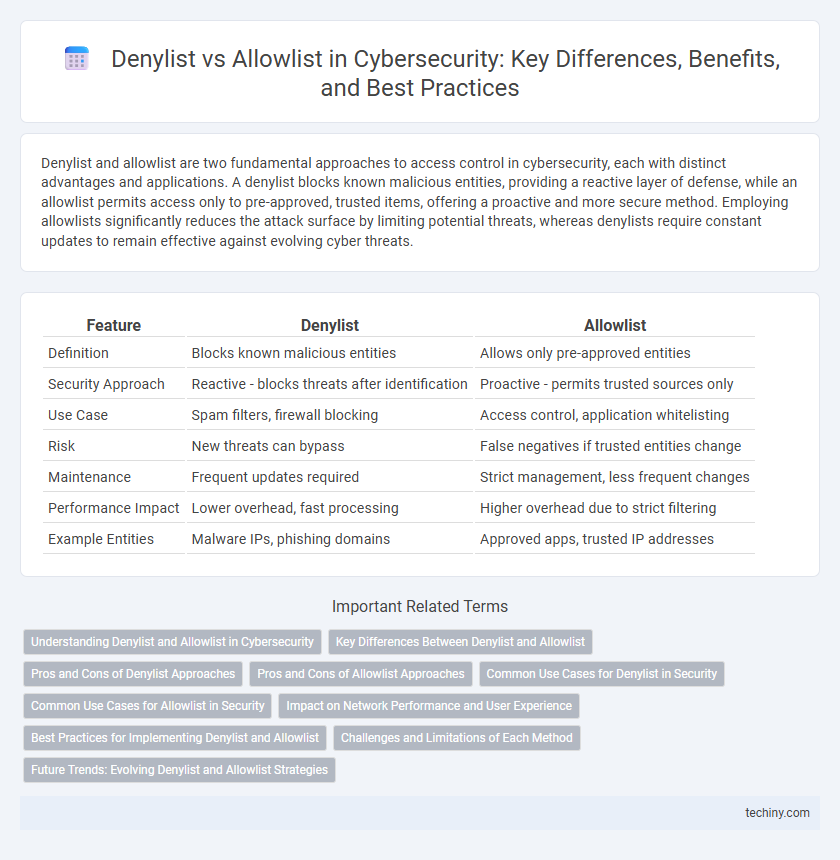
| Feature | Denylist | Allowlist |
|---|---|---|
| Definition | Blocks known malicious entities | Allows only pre-approved entities |
| Security Approach | Reactive - blocks threats after identification | Proactive - permits trusted sources only |
| Use Case | Spam filters, firewall blocking | Access control, application whitelisting |
| Risk | New threats can bypass | False negatives if trusted entities change |
| Maintenance | Frequent updates required | Strict management, less frequent changes |
| Performance Impact | Lower overhead, fast processing | Higher overhead due to strict filtering |
| Example Entities | Malware IPs, phishing domains | Approved apps, trusted IP addresses |
Understanding Denylist and Allowlist in Cybersecurity
Denylist and allowlist are essential tools in cybersecurity for managing access control and network security. A denylist blocks known malicious IP addresses, domains, or applications to prevent unauthorized access, while an allowlist permits only trusted entities, enhancing security by limiting exposure to potential threats. Effective implementation of denylist and allowlist strategies reduces vulnerabilities, mitigates cyber risks, and supports compliance with security policies.
Key Differences Between Denylist and Allowlist
Denylist blocks known malicious entities by default, allowing access only to everything else, while allowlist permits only pre-approved entities, denying all others by default. Denylist is reactive, frequently updated to include new threats, whereas allowlist is proactive, restricting access to a trusted set and minimizing exposure. The key difference lies in their operational approach: denylist filters out known bad actors, whereas allowlist permits only verified good actors, enhancing security through restriction.
Pros and Cons of Denylist Approaches
Denylist approaches in cybersecurity block known malicious entities, providing a straightforward method to prevent access to harmful IPs, domains, or files, which enhances network protection against identified threats. However, this method struggles with zero-day attacks and unknown threats since it relies on previously detected malicious signatures, leading to potential security gaps. The maintenance of denylist databases can be resource-intensive and may result in false negatives, allowing new threats to bypass defenses.
Pros and Cons of Allowlist Approaches
Allowlist approaches enhance cybersecurity by permitting only pre-approved applications or IP addresses, significantly reducing the risk of unauthorized access and malware infections. However, maintaining an allowlist requires continuous updates and careful management to avoid blocking legitimate new software or users, which can hinder productivity. This method is highly effective in controlled environments but may be less practical for dynamic or large-scale networks due to administrative overhead.
Common Use Cases for Denylist in Security
Denylist in cybersecurity is primarily used to block known malicious IP addresses, domains, or files, effectively preventing access to harmful resources. Common use cases include filtering spam emails, blocking malware distribution sites, and restricting unauthorized network traffic to reduce attack surfaces. This proactive security measure helps organizations enforce strict controls against threats while maintaining system integrity.
Common Use Cases for Allowlist in Security
Allowlists are commonly used in cybersecurity to enhance system protection by explicitly permitting only trusted applications, IP addresses, or users to access resources. They are effective in preventing unauthorized software execution, reducing malware risks, and controlling network access in enterprise environments. Allowlist deployment in email security blocks malicious senders, while in endpoint protection, it ensures that only verified programs run, significantly lowering attack surfaces.
Impact on Network Performance and User Experience
Denylist and allowlist approaches significantly influence network performance and user experience by controlling access to resources through different filtering strategies. Denylist blocks known malicious entities but may increase processing load due to continual threat updates, potentially causing latency and inconsistent user access. Allowlist, by permitting only pre-approved entities, enhances security and reduces processing overhead but can restrict legitimate access if not frequently updated, impacting usability and operational efficiency.
Best Practices for Implementing Denylist and Allowlist
Implementing denylist and allowlist strategies in cybersecurity requires precise configuration to minimize false positives and negatives, enhancing network protection. Best practices include regularly updating both lists based on evolving threats and trusted entities, conducting rigorous testing to validate their effectiveness, and integrating with centralized security management tools for real-time monitoring. Employing a layered approach, combining denylist for known threats and allowlist for trusted applications, optimizes system resilience against unauthorized access and malware.
Challenges and Limitations of Each Method
Denylist approaches in cybersecurity face challenges such as incomplete coverage of emerging threats and the risk of false negatives, allowing new or unknown malicious entities to bypass filters. Allowlist methods, while more restrictive and secure by permitting only pre-approved entities, often struggle with scalability and user inconvenience, potentially leading to operational bottlenecks. Both techniques require continuous updates and management to balance security effectiveness against usability and resource constraints.
Future Trends: Evolving Denylist and Allowlist Strategies
Future trends in cybersecurity emphasize the integration of AI-driven denylist and allowlist strategies to enhance dynamic threat detection and prevention. Adaptive machine learning algorithms continuously update these lists by analyzing behavioral patterns and emerging vulnerabilities in real time. Organizations increasingly adopt zero-trust frameworks that leverage contextual denylist and allowlist mechanisms for granular access control and risk mitigation.
Denylist vs Allowlist Infographic
 techiny.com
techiny.com