Cyberattack refers to deliberate attempts by hackers to breach an organization's digital defenses, aiming to disrupt networks or steal sensitive data. Cybercrime encompasses a broader range of illegal activities involving computers, including fraud, identity theft, and distribution of malware. Understanding the distinction helps businesses implement targeted security measures and comply with legal frameworks effectively.
Table of Comparison
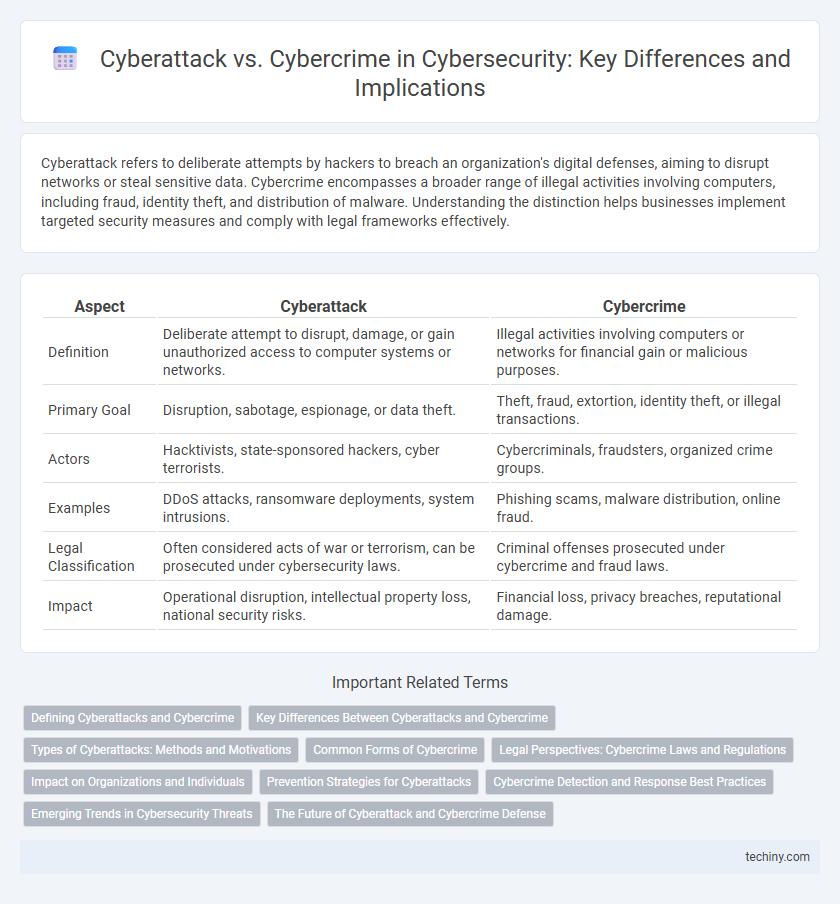
| Aspect | Cyberattack | Cybercrime |
|---|---|---|
| Definition | Deliberate attempt to disrupt, damage, or gain unauthorized access to computer systems or networks. | Illegal activities involving computers or networks for financial gain or malicious purposes. |
| Primary Goal | Disruption, sabotage, espionage, or data theft. | Theft, fraud, extortion, identity theft, or illegal transactions. |
| Actors | Hacktivists, state-sponsored hackers, cyber terrorists. | Cybercriminals, fraudsters, organized crime groups. |
| Examples | DDoS attacks, ransomware deployments, system intrusions. | Phishing scams, malware distribution, online fraud. |
| Legal Classification | Often considered acts of war or terrorism, can be prosecuted under cybersecurity laws. | Criminal offenses prosecuted under cybercrime and fraud laws. |
| Impact | Operational disruption, intellectual property loss, national security risks. | Financial loss, privacy breaches, reputational damage. |
Defining Cyberattacks and Cybercrime
Cyberattacks involve deliberate actions targeting computer systems, networks, or devices to disrupt, damage, or gain unauthorized access, often orchestrated by hackers or state-sponsored groups. Cybercrime encompasses illegal activities conducted via the internet, including identity theft, online fraud, and cyberterrorism, motivated primarily by financial gain or political objectives. Understanding the definitions distinguishes cyberattacks as specific aggressive acts within the broader scope of cybercrime.
Key Differences Between Cyberattacks and Cybercrime
Cyberattacks involve deliberate attempts to breach or disable computer systems, often targeting organizations or governments for espionage, sabotage, or disruption, whereas cybercrime broadly encompasses illegal activities conducted using digital technology, including fraud, identity theft, and online scams. Cyberattacks typically focus on compromising system integrity, confidentiality, or availability, while cybercrime emphasizes financial gain or personal data exploitation. The legal consequences and response strategies differ significantly, with cyberattacks often linked to national security concerns, whereas cybercrime is prosecuted under criminal law targeting individual offenders.
Types of Cyberattacks: Methods and Motivations
Cyberattacks encompass various methods such as phishing, ransomware, Distributed Denial of Service (DDoS), and Advanced Persistent Threats (APTs), each designed to exploit vulnerabilities in networks and systems. Motivations behind these attacks range from financial gain and espionage to political activism and sabotage. Cybercrime often involves these cyberattack techniques but emphasizes illegal activities like identity theft, fraud, and data breaches aimed at personal or organizational harm.
Common Forms of Cybercrime
Common forms of cybercrime include phishing, ransomware attacks, identity theft, and financial fraud, all leveraging digital vulnerabilities to exploit victims. Cyberattacks often target networks or systems to cause disruption or data breaches, whereas cybercrime encompasses illegal activities aimed at personal, financial, or organizational gain. Understanding the distinctions between cyberattacks and cybercrime helps in developing targeted cybersecurity measures to mitigate these threats effectively.
Legal Perspectives: Cybercrime Laws and Regulations
Cyberattack refers to deliberate attempts to breach information systems for disruption or espionage, often addressed under cybersecurity laws targeting national security threats. Cybercrime encompasses a broader range of illegal activities, including fraud, identity theft, and data breaches, regulated by comprehensive cybercrime legislation like the Computer Fraud and Abuse Act (CFAA) in the United States and the Budapest Convention on Cybercrime internationally. Legal frameworks emphasize enforcement, jurisdiction, and penalties to deter cyber offenses and protect critical infrastructure and personal data.
Impact on Organizations and Individuals
Cyberattacks often disrupt organizational operations, leading to significant financial losses, data breaches, and compromised infrastructure. Cybercrime targets both individuals and organizations, resulting in identity theft, financial fraud, and erosion of personal privacy. The combined impact undermines trust, damages reputations, and necessitates increased investment in advanced cybersecurity measures.
Prevention Strategies for Cyberattacks
Effective prevention strategies for cyberattacks involve implementing multi-layered security measures such as advanced firewalls, intrusion detection systems, and continuous network monitoring to identify and mitigate threats in real-time. Employee training programs on phishing recognition and best practices in password management significantly reduce vulnerabilities exploited by cybercriminals. Regular software updates and vulnerability assessments ensure that systems remain resilient against evolving cyberattack techniques.
Cybercrime Detection and Response Best Practices
Cybercrime detection hinges on advanced threat intelligence, behavioral analytics, and continuous monitoring to identify malicious activities before damage occurs. Implementing incident response protocols, including regular security audits, employee training, and rapid malware containment, enhances organizational resilience. Leveraging AI-driven tools and real-time data correlation strengthens detection accuracy and accelerates response times in mitigating cyberattacks effectively.
Emerging Trends in Cybersecurity Threats
Emerging trends in cybersecurity threats reveal a significant shift, with cyberattacks increasingly targeting critical infrastructure, leveraging artificial intelligence for sophisticated intrusion techniques, and exploiting vulnerabilities in Internet of Things (IoT) devices. Cybercrime activities now frequently encompass ransomware campaigns, data breaches, and social engineering tactics that compromise sensitive information across industries. These evolving threats demand advanced threat detection solutions, continuous security monitoring, and enhanced incident response strategies to safeguard digital assets effectively.
The Future of Cyberattack and Cybercrime Defense
Emerging technologies like artificial intelligence and machine learning are revolutionizing the future of cyberattack and cybercrime defense by enabling real-time threat detection and automated response systems. Advanced predictive analytics enhance cybersecurity frameworks, allowing organizations to anticipate and mitigate sophisticated cyber threats before they materialize. Collaboration between global cybersecurity agencies and continuous innovation in encryption and access control technologies remain critical to evolving defenses against increasingly complex cyberattacks and cybercrimes.
Cyberattack vs cybercrime Infographic
 techiny.com
techiny.com