CVE (Common Vulnerabilities and Exposures) provides a unique identifier for publicly known cybersecurity vulnerabilities, enabling consistent tracking and communication across platforms. CVSS (Common Vulnerability Scoring System) quantifies the severity of these vulnerabilities using a standardized scoring model, aiding organizations in prioritizing remediation efforts. Understanding the distinction between CVE as an identification system and CVSS as a risk assessment tool is crucial for effective vulnerability management.
Table of Comparison
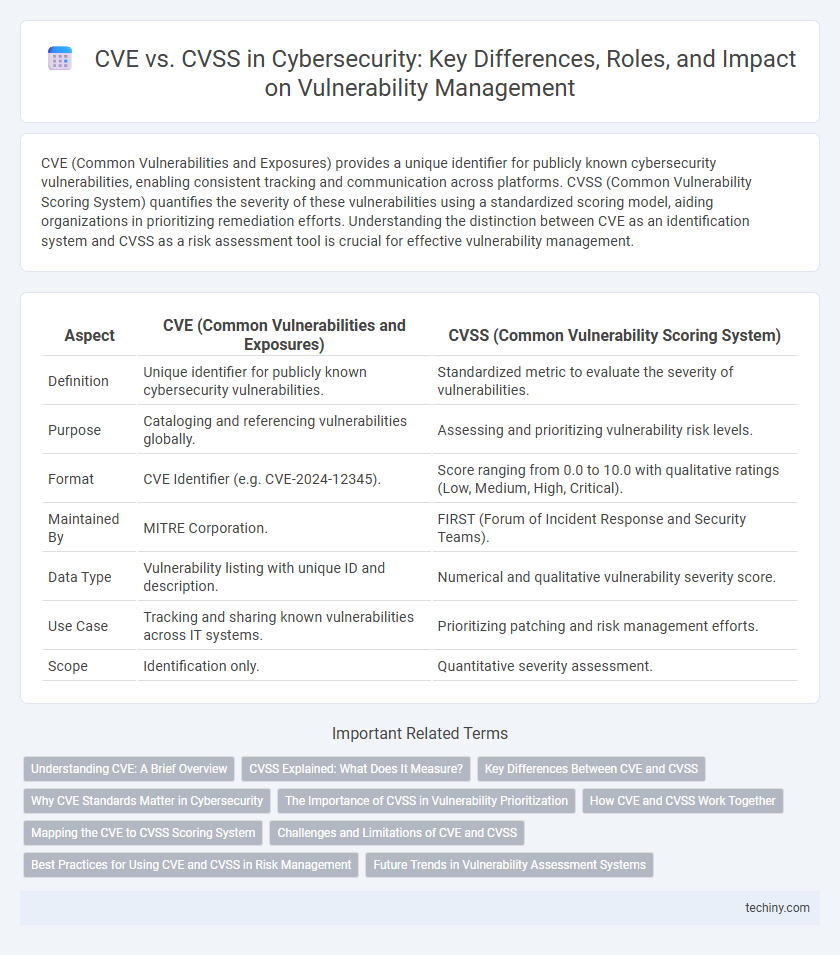
| Aspect | CVE (Common Vulnerabilities and Exposures) | CVSS (Common Vulnerability Scoring System) |
|---|---|---|
| Definition | Unique identifier for publicly known cybersecurity vulnerabilities. | Standardized metric to evaluate the severity of vulnerabilities. |
| Purpose | Cataloging and referencing vulnerabilities globally. | Assessing and prioritizing vulnerability risk levels. |
| Format | CVE Identifier (e.g. CVE-2024-12345). | Score ranging from 0.0 to 10.0 with qualitative ratings (Low, Medium, High, Critical). |
| Maintained By | MITRE Corporation. | FIRST (Forum of Incident Response and Security Teams). |
| Data Type | Vulnerability listing with unique ID and description. | Numerical and qualitative vulnerability severity score. |
| Use Case | Tracking and sharing known vulnerabilities across IT systems. | Prioritizing patching and risk management efforts. |
| Scope | Identification only. | Quantitative severity assessment. |
Understanding CVE: A Brief Overview
CVE (Common Vulnerabilities and Exposures) serves as a standardized identifier assigned to publicly known cybersecurity vulnerabilities, enabling consistent tracking and communication across platforms. Each CVE entry provides a unique code, descriptive details, and references to related information sources, facilitating efficient vulnerability management. Understanding CVE is crucial for cybersecurity professionals to accurately identify and address specific security flaws within software and hardware systems.
CVSS Explained: What Does It Measure?
CVSS (Common Vulnerability Scoring System) quantifies the severity of cybersecurity vulnerabilities by evaluating metrics like exploitability, impact, and temporal factors. It provides a numerical score ranging from 0 to 10 that helps organizations prioritize risk mitigation based on the potential threat posed by specific vulnerabilities identified by CVE (Common Vulnerabilities and Exposures). CVSS metrics include Base, Temporal, and Environmental groups, each offering distinct insights into vulnerability severity and context-specific risk.
Key Differences Between CVE and CVSS
CVE (Common Vulnerabilities and Exposures) is a unique identifier assigned to specific cybersecurity vulnerabilities, enabling consistent tracking and referencing across platforms. CVSS (Common Vulnerability Scoring System) quantifies the severity of these vulnerabilities by providing a standardized numerical score based on exploitability, impact, and complexity. The key difference lies in CVE serving as an identification system, while CVSS offers a detailed metric to prioritize risk assessment and remediation efforts.
Why CVE Standards Matter in Cybersecurity
CVE (Common Vulnerabilities and Exposures) standards matter in cybersecurity because they provide a universal identification system for known vulnerabilities, enabling consistent tracking and communication across security tools and organizations. Unlike CVSS (Common Vulnerability Scoring System), which quantifies the severity of vulnerabilities, CVE focuses on uniquely cataloging each issue to avoid confusion and duplication. This standardized framework enhances threat intelligence sharing, accelerates vulnerability management, and strengthens coordinated defense strategies against cyber attacks.
The Importance of CVSS in Vulnerability Prioritization
CVSS (Common Vulnerability Scoring System) provides a standardized method to assess the severity of vulnerabilities listed in the CVE (Common Vulnerabilities and Exposures) database, enabling security teams to prioritize remediation efforts effectively. By assigning numerical scores based on exploitability, impact, and temporal metrics, CVSS helps organizations allocate resources to address the most critical threats first. Accurate CVSS scoring enhances vulnerability management strategies, reduces risk exposure, and supports compliance with cybersecurity frameworks.
How CVE and CVSS Work Together
CVE (Common Vulnerabilities and Exposures) provides unique identifiers for publicly known cybersecurity vulnerabilities, enabling standardized tracking and reporting across platforms. CVSS (Common Vulnerability Scoring System) assigns severity scores to these CVE entries, quantifying risk based on factors like exploitability, impact, and environmental metrics. Together, CVE offers precise vulnerability identification while CVSS delivers a consistent framework for prioritizing remediation efforts based on calculated threat levels.
Mapping the CVE to CVSS Scoring System
Mapping the Common Vulnerabilities and Exposures (CVE) to the Common Vulnerability Scoring System (CVSS) facilitates standardized assessment of cybersecurity risks by quantifying the severity of identified vulnerabilities. Each CVE entry is assigned a CVSS score, ranging from 0 to 10, based on factors such as exploitability, impact, and complexity, enabling prioritization of remediation efforts. Accurate CVE to CVSS mapping enhances vulnerability management by providing actionable insights for security analysts and automated tools.
Challenges and Limitations of CVE and CVSS
The Common Vulnerabilities and Exposures (CVE) system often faces challenges in providing timely updates and lacks contextual severity information, limiting its effectiveness in dynamic cybersecurity environments. The Common Vulnerability Scoring System (CVSS) struggles with subjectivity in scoring, resulting in inconsistent vulnerability prioritization and potential misallocation of resources. Both frameworks have limitations in addressing complex threats involving chained exploits and multi-vector vulnerabilities, creating gaps in comprehensive risk assessment.
Best Practices for Using CVE and CVSS in Risk Management
Effectively integrating CVE (Common Vulnerabilities and Exposures) and CVSS (Common Vulnerability Scoring System) in risk management requires prioritizing vulnerabilities based on CVSS scores to allocate resources efficiently and address the most critical threats first. Organizations should continuously update and cross-reference their vulnerability databases with published CVE entries while tailoring CVSS metrics to reflect their specific environmental impact and risk tolerance. Regularly combining CVE identifiers with context-aware CVSS evaluations enhances decision-making accuracy and mitigates potential security breaches more proactively.
Future Trends in Vulnerability Assessment Systems
CVE (Common Vulnerabilities and Exposures) provides a standardized identifier for publicly known cybersecurity vulnerabilities, forming the foundation for vulnerability tracking, while CVSS (Common Vulnerability Scoring System) offers a quantifiable severity score that guides prioritization efforts. Future trends in vulnerability assessment systems emphasize integrating AI-driven analytics with CVE databases to enable real-time detection and dynamic scoring enhancements beyond the static CVSS models. Evolving approaches will leverage machine learning to predict exploitability patterns and contextual risk factors, improving proactive defense mechanisms in cybersecurity frameworks.
CVE vs CVSS Infographic
 techiny.com
techiny.com