Social engineering exploits human psychology to manipulate individuals into revealing confidential information, bypassing technical defenses through deception. Technical attacks, by contrast, target system vulnerabilities using malware, hacking tools, or network breaches to gain unauthorized access. Combining awareness training with robust security measures is critical to defending against both human-centered and technology-driven cyber threats.
Table of Comparison
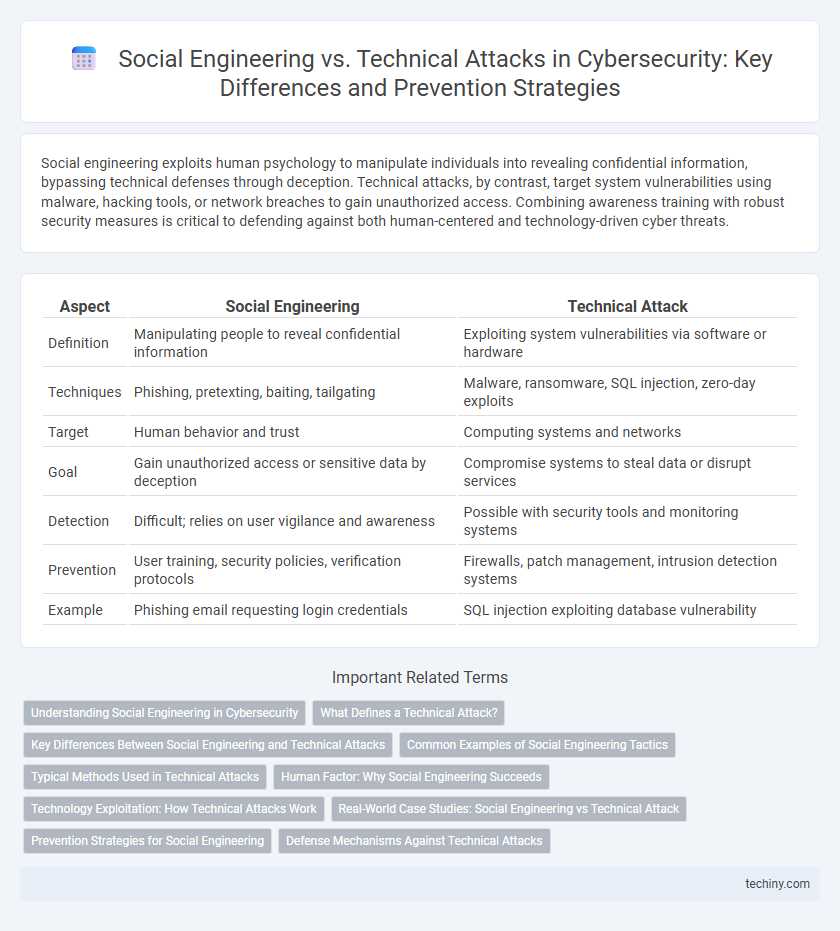
| Aspect | Social Engineering | Technical Attack |
|---|---|---|
| Definition | Manipulating people to reveal confidential information | Exploiting system vulnerabilities via software or hardware |
| Techniques | Phishing, pretexting, baiting, tailgating | Malware, ransomware, SQL injection, zero-day exploits |
| Target | Human behavior and trust | Computing systems and networks |
| Goal | Gain unauthorized access or sensitive data by deception | Compromise systems to steal data or disrupt services |
| Detection | Difficult; relies on user vigilance and awareness | Possible with security tools and monitoring systems |
| Prevention | User training, security policies, verification protocols | Firewalls, patch management, intrusion detection systems |
| Example | Phishing email requesting login credentials | SQL injection exploiting database vulnerability |
Understanding Social Engineering in Cybersecurity
Social engineering in cybersecurity exploits human psychology to manipulate individuals into divulging confidential information or granting unauthorized access, bypassing technical defenses. Techniques such as phishing, pretexting, and baiting exploit trust and curiosity, making it a critical threat that targets the weakest link in security systems--human users. Effective defense requires comprehensive training, awareness programs, and behavioral monitoring to complement technical controls and mitigate social engineering risks.
What Defines a Technical Attack?
A technical attack in cybersecurity exploits software vulnerabilities, network weaknesses, or hardware flaws to gain unauthorized access or cause disruption. Common methods include malware deployment, phishing with malicious links, zero-day exploits, and denial-of-service (DoS) attacks targeting system infrastructure. Unlike social engineering, which manipulates human behavior, technical attacks rely on exploiting technical systems and code flaws.
Key Differences Between Social Engineering and Technical Attacks
Social engineering exploits human psychology to manipulate individuals into divulging confidential information, while technical attacks target system vulnerabilities through malware, phishing, or hacking techniques. Social engineering relies on deception and trust exploitation, whereas technical attacks depend on software or hardware weaknesses to gain unauthorized access. Understanding these key differences is crucial for developing comprehensive cybersecurity defenses that address both human error and technological flaws.
Common Examples of Social Engineering Tactics
Phishing emails, pretexting, and baiting remain the most prevalent social engineering tactics used to manipulate individuals into revealing sensitive information or granting unauthorized access. Attackers often impersonate trusted figures, such as IT personnel or executives, to exploit human psychology rather than technical vulnerabilities. Unlike technical attacks that target software or hardware flaws, social engineering leverages deception and trust to bypass security measures.
Typical Methods Used in Technical Attacks
Technical attacks in cybersecurity primarily involve exploiting system vulnerabilities through methods such as malware deployment, phishing emails embedded with malicious links, and brute-force password cracking. Attackers utilize tools like keyloggers, ransomware, and zero-day exploits to gain unauthorized access or disrupt services. Network intrusions often leverage techniques such as SQL injection, cross-site scripting (XSS), and packet sniffing to extract sensitive information or compromise system integrity.
Human Factor: Why Social Engineering Succeeds
Social engineering exploits human psychology by manipulating trust, fear, or urgency to bypass traditional cybersecurity measures. Unlike technical attacks that target software vulnerabilities, social engineering attacks focus on human error, making individuals the weakest link in security defenses. Studies show that over 90% of successful breaches involve some form of social engineering, highlighting the critical need for continuous employee training and awareness programs.
Technology Exploitation: How Technical Attacks Work
Technical attacks leverage vulnerabilities in software, hardware, or network protocols to gain unauthorized access or disrupt systems, often using methods like malware, phishing links with embedded exploits, or brute force password cracking. Exploit kits automate the identification and manipulation of security flaws, enabling attackers to execute payloads that bypass firewalls and antivirus defenses. These attacks rely on up-to-date intelligence about system weaknesses and often target zero-day vulnerabilities to maximize impact before patches are deployed.
Real-World Case Studies: Social Engineering vs Technical Attack
Real-world case studies highlight social engineering attacks exploiting human vulnerability, such as the 2013 Target breach where phishing enabled attackers to access network credentials, leading to a massive data leak of 40 million credit card records. Technical attacks like the WannaCry ransomware outbreak in 2017 exploited software vulnerabilities in Windows systems, causing widespread disruption across 150 countries. Comparing these incidents illustrates how combining employee training with robust patch management significantly reduces cybersecurity risks.
Prevention Strategies for Social Engineering
Effective prevention strategies for social engineering include comprehensive employee training on recognizing phishing emails, suspicious phone calls, and fake websites that impersonate legitimate sources. Implementing strict access controls, multi-factor authentication, and regular security awareness programs reduces the risk of manipulation by attackers exploiting human vulnerabilities. Continuous monitoring and simulated social engineering tests help organizations identify weaknesses and reinforce proactive defense mechanisms against deceitful tactics.
Defense Mechanisms Against Technical Attacks
Defense mechanisms against technical attacks in cybersecurity include robust firewalls, intrusion detection systems (IDS), and regular software patching to mitigate vulnerabilities. Implementing multi-factor authentication (MFA) and advanced encryption protocols further secures network access and sensitive data. Continuous monitoring combined with automated threat intelligence platforms enhances the rapid identification and neutralization of evolving technical threats.
Social Engineering vs Technical Attack Infographic
 techiny.com
techiny.com