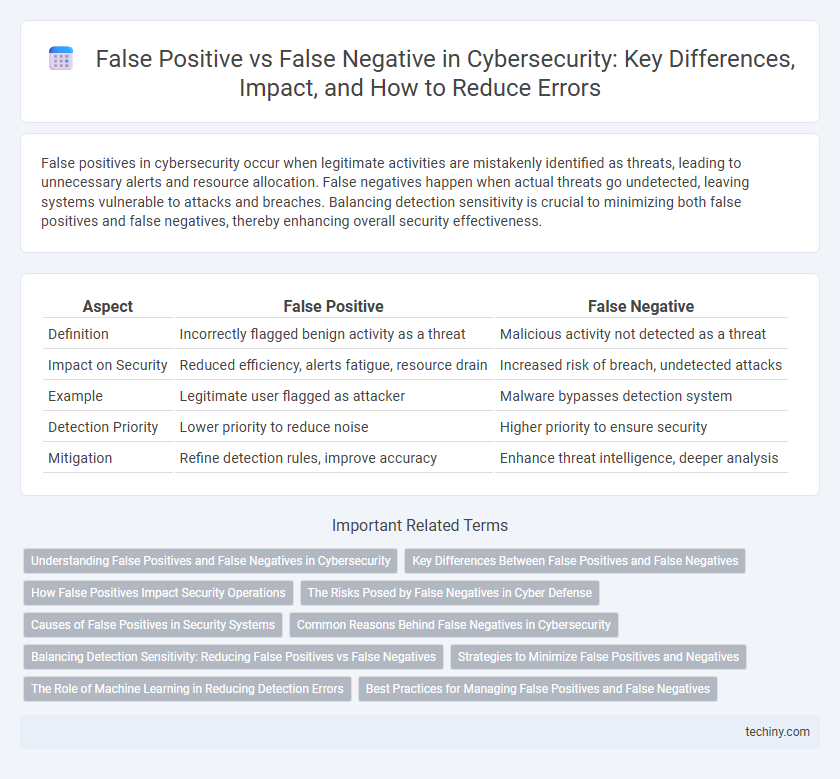
False positives in cybersecurity occur when legitimate activities are mistakenly identified as threats, leading to unnecessary alerts and resource allocation. False negatives happen when actual threats go undetected, leaving systems vulnerable to attacks and breaches. Balancing detection sensitivity is crucial to minimizing both false positives and false negatives, thereby enhancing overall security effectiveness.
Table of Comparison
| Aspect | False Positive | False Negative |
|---|---|---|
| Definition | Incorrectly flagged benign activity as a threat | Malicious activity not detected as a threat |
| Impact on Security | Reduced efficiency, alerts fatigue, resource drain | Increased risk of breach, undetected attacks |
| Example | Legitimate user flagged as attacker | Malware bypasses detection system |
| Detection Priority | Lower priority to reduce noise | Higher priority to ensure security |
| Mitigation | Refine detection rules, improve accuracy | Enhance threat intelligence, deeper analysis |
Understanding False Positives and False Negatives in Cybersecurity
False positives in cybersecurity occur when legitimate activity is mistakenly identified as a threat, leading to unnecessary alerts that can overwhelm security teams and reduce overall efficiency. False negatives happen when actual cyber threats go undetected, allowing malicious actions to compromise systems and data integrity. Balancing detection sensitivity to minimize false positives while ensuring true threats are identified is critical for effective cybersecurity incident response and risk management.
Key Differences Between False Positives and False Negatives
False positives in cybersecurity occur when benign activities are incorrectly flagged as threats, leading to unnecessary alerts and resource expenditure. False negatives happen when actual malicious activities evade detection, posing significant risks by allowing breaches to go unnoticed. The key difference lies in impact: false positives reduce efficiency by increasing alert fatigue, while false negatives compromise security by missing genuine threats.
How False Positives Impact Security Operations
False positives in cybersecurity trigger unnecessary alerts that consume valuable security resources and analyst time, reducing overall operational efficiency. Excessive false positives can lead to alert fatigue, causing genuine threats to be overlooked or ignored. This misallocation of attention undermines incident response capabilities and delays critical threat mitigation efforts.
The Risks Posed by False Negatives in Cyber Defense
False negatives in cyber defense allow malicious activities to go undetected, significantly increasing the risk of data breaches and advanced persistent threats. These undetected threats can lead to severe financial losses, compromised sensitive information, and damage to an organization's reputation. Effective detection systems must minimize false negatives to ensure timely identification and mitigation of cyber attacks.
Causes of False Positives in Security Systems
False positives in cybersecurity often result from overly sensitive detection algorithms that flag benign activities as threats due to heuristic or signature-based rule limitations. Incomplete or outdated threat intelligence can misclassify legitimate network behavior, while poorly tuned intrusion detection systems (IDS) fail to distinguish between normal anomalies and genuine attacks. Environmental noise and ambiguous data patterns further contribute to the occurrence of false positives, impacting threat response efficiency.
Common Reasons Behind False Negatives in Cybersecurity
False negatives in cybersecurity often occur due to outdated threat intelligence, which limits detection capabilities against emerging malware and attack vectors. Insufficient tuning of security systems and overly aggressive filtering algorithms can cause genuine threats to be overlooked as benign. Complex attack patterns and advanced evasion techniques employed by cybercriminals further contribute to the challenge of minimizing false negatives in intrusion detection systems.
Balancing Detection Sensitivity: Reducing False Positives vs False Negatives
Balancing detection sensitivity in cybersecurity involves minimizing false positives, which generate unnecessary alerts and resource drain, while also reducing false negatives that allow threats to go undetected, compromising security. Effective tuning of intrusion detection systems and employing machine learning algorithms enhances threat identification accuracy by optimizing the threshold between sensitivity and specificity. Organizations must continuously analyze detection patterns to adjust parameters dynamically, ensuring optimal protection without overwhelming security teams with benign alerts.
Strategies to Minimize False Positives and Negatives
Implementing advanced machine learning algorithms enhances threat detection accuracy, reducing both false positives and false negatives in cybersecurity systems. Continuous tuning of detection thresholds based on real-time threat intelligence and comprehensive user behavior analysis minimizes erroneous alerts while maintaining high sensitivity for genuine threats. Integrating multi-layered verification processes, such as combining signature-based detection with anomaly detection, further refines the balance between false positive and false negative rates.
The Role of Machine Learning in Reducing Detection Errors
Machine learning algorithms enhance cybersecurity by minimizing false positives and false negatives through advanced pattern recognition and anomaly detection techniques. These models analyze vast datasets to differentiate between legitimate activities and threats, improving accuracy and reducing unnecessary alerts. Continuous training on diverse cyber threat data allows machine learning systems to adapt and optimize detection performance, thereby strengthening overall security posture.
Best Practices for Managing False Positives and False Negatives
Effective management of false positives and false negatives in cybersecurity involves regularly tuning detection algorithms to balance sensitivity and specificity, reducing alert fatigue while maintaining threat detection accuracy. Implementing adaptive machine learning models and context-aware filtering helps refine alerts based on behavioral patterns and organizational risk profiles. Continuous monitoring, combined with human analyst validation, ensures timely identification of genuine threats and minimizes the impact of inaccurate classifications on security operations.
False Positive vs False Negative Infographic
 techiny.com
techiny.com