Assessing risk versus impact in cybersecurity involves evaluating the probability of a threat exploiting a vulnerability against the potential damage it could cause. Prioritizing threats requires understanding both the likelihood of occurrence and the severity of consequences to allocate resources effectively. Accurate risk assessment enables organizations to implement targeted defenses that minimize critical operational and financial impacts.
Table of Comparison
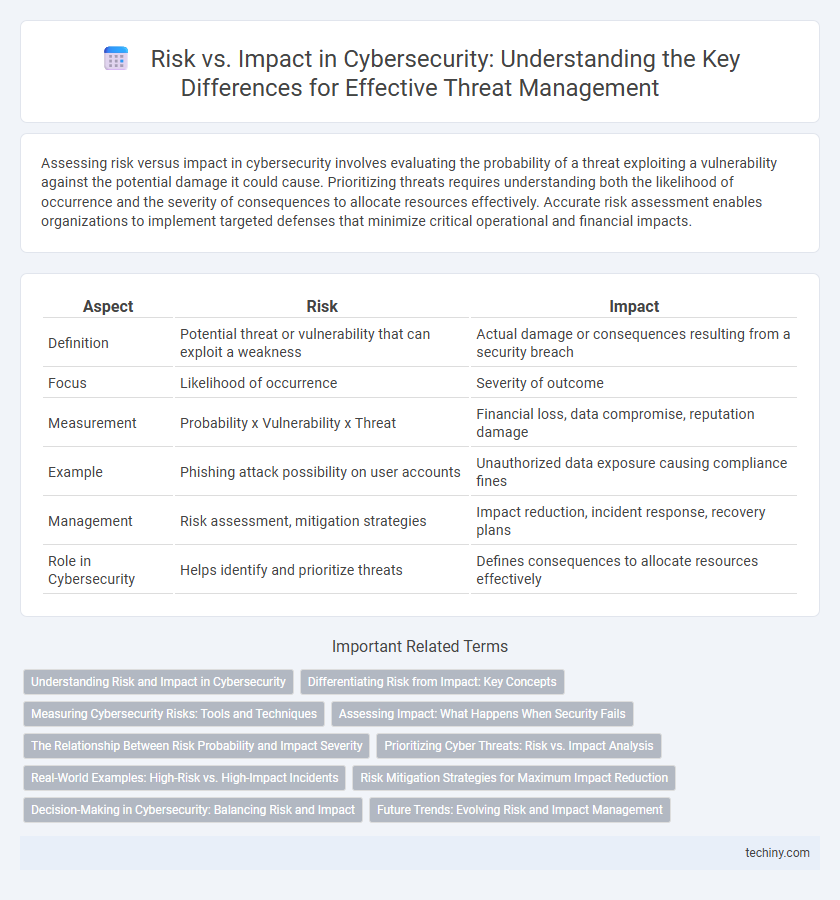
| Aspect | Risk | Impact |
|---|---|---|
| Definition | Potential threat or vulnerability that can exploit a weakness | Actual damage or consequences resulting from a security breach |
| Focus | Likelihood of occurrence | Severity of outcome |
| Measurement | Probability x Vulnerability x Threat | Financial loss, data compromise, reputation damage |
| Example | Phishing attack possibility on user accounts | Unauthorized data exposure causing compliance fines |
| Management | Risk assessment, mitigation strategies | Impact reduction, incident response, recovery plans |
| Role in Cybersecurity | Helps identify and prioritize threats | Defines consequences to allocate resources effectively |
Understanding Risk and Impact in Cybersecurity
Understanding risk in cybersecurity involves identifying potential threats and vulnerabilities that could exploit system weaknesses. Impact measures the consequences of these threats, including data loss, financial damage, or reputational harm. Effective cybersecurity strategies prioritize mitigating high-risk areas to minimize adverse impacts on organizational assets.
Differentiating Risk from Impact: Key Concepts
Risk in cybersecurity refers to the probability of a threat exploiting a vulnerability, potentially causing harm, while impact measures the extent of damage or adverse effects resulting from a security breach. Understanding the differentiation between risk and impact is crucial for effective resource allocation and mitigation strategies. Risk assesses the likelihood and exposure, whereas impact evaluates the consequences on data integrity, confidentiality, and business operations.
Measuring Cybersecurity Risks: Tools and Techniques
Measuring cybersecurity risks involves employing advanced tools such as risk assessment frameworks, vulnerability scanners, and threat intelligence platforms to quantify potential threats and their impact on organizational assets. Techniques like quantitative risk analysis and qualitative risk matrices help prioritize vulnerabilities based on likelihood and severity, enabling targeted mitigation strategies. Integrating continuous monitoring systems enhances real-time risk evaluation, ensuring adaptive defenses against evolving cyber threats.
Assessing Impact: What Happens When Security Fails
Assessing impact in cybersecurity involves quantifying the potential damage caused by security failures, including data breaches, financial losses, and reputational harm. Risk analysis prioritizes threats by estimating the consequences of unauthorized access or system downtime on operations and compliance. Effective impact assessment guides resource allocation for preventive measures and incident response planning.
The Relationship Between Risk Probability and Impact Severity
Risk probability measures the likelihood of a cybersecurity threat exploiting a vulnerability, while impact severity quantifies the potential damage caused by such an event. Understanding the relationship between these two factors is crucial for prioritizing security measures and allocating resources effectively. Organizations must analyze both the frequency and magnitude of risks to develop comprehensive risk management strategies that minimize operational disruptions and data breaches.
Prioritizing Cyber Threats: Risk vs. Impact Analysis
Prioritizing cyber threats requires evaluating risk by combining the likelihood of an attack with its potential impact on critical assets. Organizations should allocate resources based on threats that pose the highest risk score, factoring in both the probability of occurrence and the severity of consequences such as data breaches, financial loss, or reputational damage. Effective risk vs. impact analysis enables cybersecurity teams to focus defenses on vulnerabilities that could cause the most significant operational disruption or regulatory penalties.
Real-World Examples: High-Risk vs. High-Impact Incidents
High-risk cybersecurity incidents, such as frequent phishing attacks, pose persistent threats by exploiting vulnerabilities with a moderate impact on single organizations but high potential for widespread damage. In contrast, high-impact incidents like the 2017 Equifax breach resulted in the exposure of sensitive data for over 147 million people, demonstrating severe consequences despite lower attack frequency. Real-world analysis shows that balancing the probability of occurrence with the scale of impact is essential for effective risk management and resource allocation.
Risk Mitigation Strategies for Maximum Impact Reduction
Effective risk mitigation strategies in cybersecurity prioritize identifying vulnerabilities and implementing layered defenses such as firewalls, encryption, and intrusion detection systems to reduce potential impacts. Regular risk assessments combined with real-time monitoring enable organizations to anticipate threats and minimize damage from cyber incidents. Integrating employee training and incident response plans further solidifies the overall defense posture, maximizing impact reduction during attacks.
Decision-Making in Cybersecurity: Balancing Risk and Impact
Effective decision-making in cybersecurity requires balancing the likelihood of threats (risk) with their potential consequences (impact) to prioritize resource allocation. Quantifying both risk probabilities and impact severity enables organizations to implement targeted controls that mitigate high-impact risks efficiently. This approach enhances resilience by focusing on vulnerabilities that could cause significant operational, financial, or reputational damage.
Future Trends: Evolving Risk and Impact Management
Emerging cybersecurity threats increasingly require adaptive risk assessment models that incorporate AI-driven analytics to predict and mitigate potential impacts. Enterprises are shifting towards dynamic frameworks that evaluate both immediate and long-term consequences of breaches, emphasizing resilience and rapid recovery. Future trends highlight the integration of threat intelligence platforms with risk management systems to create proactive safeguards against progressively sophisticated cyberattacks.
Risk vs Impact Infographic
 techiny.com
techiny.com