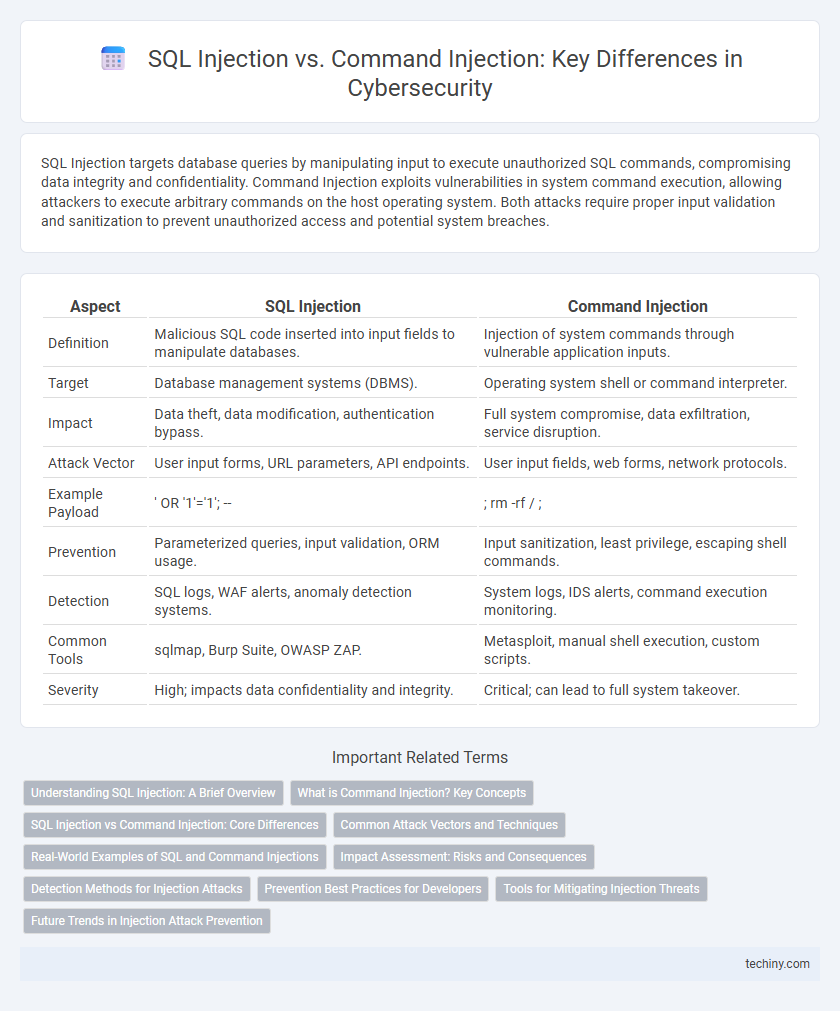
SQL Injection targets database queries by manipulating input to execute unauthorized SQL commands, compromising data integrity and confidentiality. Command Injection exploits vulnerabilities in system command execution, allowing attackers to execute arbitrary commands on the host operating system. Both attacks require proper input validation and sanitization to prevent unauthorized access and potential system breaches.
Table of Comparison
| Aspect | SQL Injection | Command Injection |
|---|---|---|
| Definition | Malicious SQL code inserted into input fields to manipulate databases. | Injection of system commands through vulnerable application inputs. |
| Target | Database management systems (DBMS). | Operating system shell or command interpreter. |
| Impact | Data theft, data modification, authentication bypass. | Full system compromise, data exfiltration, service disruption. |
| Attack Vector | User input forms, URL parameters, API endpoints. | User input fields, web forms, network protocols. |
| Example Payload | ' OR '1'='1'; -- | ; rm -rf / ; |
| Prevention | Parameterized queries, input validation, ORM usage. | Input sanitization, least privilege, escaping shell commands. |
| Detection | SQL logs, WAF alerts, anomaly detection systems. | System logs, IDS alerts, command execution monitoring. |
| Common Tools | sqlmap, Burp Suite, OWASP ZAP. | Metasploit, manual shell execution, custom scripts. |
| Severity | High; impacts data confidentiality and integrity. | Critical; can lead to full system takeover. |
Understanding SQL Injection: A Brief Overview
SQL Injection targets database queries by inserting malicious SQL code to manipulate or access data unauthorizedly, exploiting vulnerabilities in input validation. It primarily affects applications interfacing with relational databases like MySQL, SQL Server, and PostgreSQL, enabling attackers to retrieve, modify, or delete sensitive information. Command Injection, in contrast, exploits insufficient validation of system commands, allowing arbitrary shell commands execution, but SQL Injection focuses specifically on database manipulation through crafted SQL statements.
What is Command Injection? Key Concepts
Command Injection is a cybersecurity vulnerability where attackers execute arbitrary system commands on a server through unsafe input handling. Key concepts include exploiting insufficient input validation, enabling attackers to manipulate OS-level commands, often bypassing application logic security controls. This type of injection targets the underlying operating system rather than just the database, posing significant risks to system integrity and data confidentiality.
SQL Injection vs Command Injection: Core Differences
SQL Injection targets database queries by manipulating input to execute unauthorized SQL commands, compromising data integrity and confidentiality. Command Injection exploits vulnerabilities to execute arbitrary system commands on the host OS, risking broader system control and data exposure. Both attacks leverage input validation flaws but differ fundamentally in attack vectors and impacted layers of the application stack.
Common Attack Vectors and Techniques
SQL Injection exploits vulnerabilities in web applications by injecting malicious SQL queries through input fields to manipulate database operations, often targeting login forms, search boxes, and URL parameters. Command Injection involves inserting system-level commands into insecure application inputs, exploiting functions that execute shell commands, commonly through web interfaces or server-side scripts. Both attack vectors leverage input validation flaws but differ in targets: SQL Injection attacks database engines, while Command Injection compromises the underlying operating system.
Real-World Examples of SQL and Command Injections
Real-world SQL injection attacks such as the 2017 Equifax breach exploited vulnerable database queries to exfiltrate sensitive personal data from over 140 million users. Command injection incidents, like the 2019 Capital One hack, leveraged insecure system command executions to gain root access and steal millions of credit applications. Both attack types highlight the critical need for input validation and parameterized queries to prevent unauthorized data access and system compromise in enterprise environments.
Impact Assessment: Risks and Consequences
SQL Injection exploits vulnerabilities in database queries, enabling attackers to manipulate or access sensitive data, leading to data breaches, loss of data integrity, and potential exposure of confidential information. Command Injection targets the operating system level, allowing execution of arbitrary commands, which can result in full system compromise, unauthorized access, and disruption of critical services. Both attack types pose severe security risks, with SQL Injection primarily threatening data confidentiality and Command Injection endangering system availability and control.
Detection Methods for Injection Attacks
Effective detection of SQL Injection and Command Injection attacks relies heavily on anomaly-based and signature-based monitoring techniques. Anomaly-based systems analyze unusual patterns in query syntax and command execution flow, while signature-based tools scan input against known malicious payloads such as tautologies or shell commands. Advanced approaches incorporate machine learning models to detect novel injection vectors by assessing deviations from baseline application behavior, enhancing early threat identification in cybersecurity frameworks.
Prevention Best Practices for Developers
To prevent SQL Injection, developers should use parameterized queries and prepared statements, enforce strict input validation, and apply the principle of least privilege for database access. For Command Injection prevention, it's essential to sanitize all user inputs, avoid direct shell command execution with untrusted data, and utilize secure APIs that abstract system-level functions. Regular code reviews and employing automated security testing tools enhance early detection of injection vulnerabilities in both cases.
Tools for Mitigating Injection Threats
WAFs (Web Application Firewalls) and tools like ModSecurity provide essential protection by filtering and monitoring HTTP requests to block SQL Injection and Command Injection attacks. Static Application Security Testing (SAST) tools such as Checkmarx and Veracode analyze source code to detect injection vulnerabilities before deployment. Runtime Application Self-Protection (RASP) solutions offer real-time detection and prevention by monitoring application behavior and blocking suspicious commands during execution.
Future Trends in Injection Attack Prevention
Emerging trends in injection attack prevention emphasize the integration of AI-driven anomaly detection systems to identify and mitigate SQL Injection and Command Injection threats in real-time. Advances in machine learning models enhance the accuracy of threat detection by analyzing complex query patterns and system behaviors, reducing false positives. Future cybersecurity frameworks prioritize automated patch management and adaptive input validation to proactively thwart evolving injection techniques across diverse application environments.
SQL Injection vs Command Injection Infographic
 techiny.com
techiny.com