A security event is any observable occurrence in a system or network, such as a login attempt or file access, which may or may not indicate a threat. A security incident refers to a confirmed event or series of events that compromise the confidentiality, integrity, or availability of information systems. Distinguishing between security events and incidents enables more effective prioritization and response within cybersecurity operations.
Table of Comparison
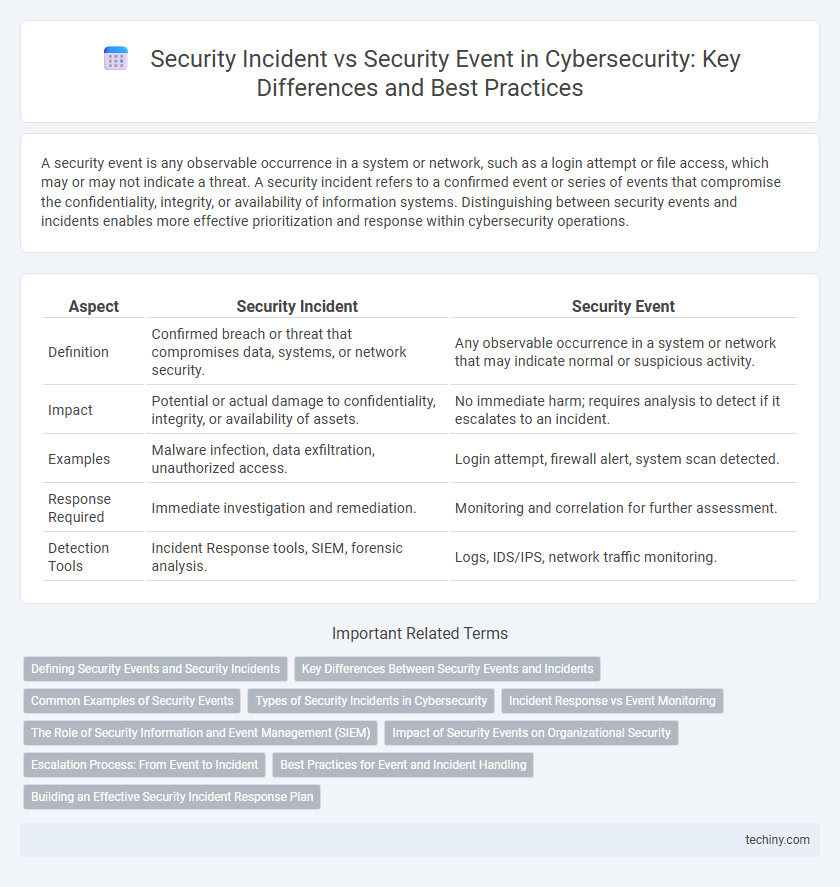
| Aspect | Security Incident | Security Event |
|---|---|---|
| Definition | Confirmed breach or threat that compromises data, systems, or network security. | Any observable occurrence in a system or network that may indicate normal or suspicious activity. |
| Impact | Potential or actual damage to confidentiality, integrity, or availability of assets. | No immediate harm; requires analysis to detect if it escalates to an incident. |
| Examples | Malware infection, data exfiltration, unauthorized access. | Login attempt, firewall alert, system scan detected. |
| Response Required | Immediate investigation and remediation. | Monitoring and correlation for further assessment. |
| Detection Tools | Incident Response tools, SIEM, forensic analysis. | Logs, IDS/IPS, network traffic monitoring. |
Defining Security Events and Security Incidents
A security event refers to any observable occurrence within a network or system that may be relevant to security, such as user logins, network traffic, or system alerts. A security incident is a confirmed or suspected adverse event that poses a threat to the confidentiality, integrity, or availability of information assets, often requiring immediate investigation and response. Understanding the distinction between security events and incidents is crucial for effective cybersecurity monitoring and incident management.
Key Differences Between Security Events and Incidents
Security events are any observable occurrences in a network or system that may affect security, such as login attempts or malware detections, while security incidents specifically refer to events that lead to unauthorized access, data breaches, or disruption of services. Incidents require immediate investigation and response due to their potential to cause harm, whereas events are monitored to detect patterns that may escalate into incidents. Understanding these distinctions improves threat management and prioritizes resource allocation in cybersecurity operations.
Common Examples of Security Events
Common examples of security events include unauthorized login attempts, malware detections, and suspicious network traffic patterns. These events represent potential indicators of compromise that require monitoring but do not necessarily confirm a security breach. Security incidents occur when these events are analyzed and verified as breaches impacting confidentiality, integrity, or availability of information systems.
Types of Security Incidents in Cybersecurity
Security incidents in cybersecurity include data breaches, malware infections, ransomware attacks, insider threats, and denial-of-service (DoS) attacks, each representing unauthorized or malicious activity that compromises the confidentiality, integrity, or availability of information systems. Unlike routine security events, which are normal occurrences like system logins or updates, security incidents require immediate investigation and response to mitigate potential damage. Effective incident response plans categorize these incidents to prioritize actions and implement appropriate containment and recovery strategies.
Incident Response vs Event Monitoring
Security events are individual occurrences that affect an information system's security, often detected through event monitoring tools that continuously analyze network traffic, logs, and system behaviors. Security incidents represent events that have been identified as causing or having the potential to cause harm, requiring incident response teams to investigate, contain, and remediate the threat to minimize damage. Effective cybersecurity relies on integrating event monitoring systems with robust incident response protocols to promptly detect anomalies and coordinate swift actions against breaches.
The Role of Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems play a crucial role in distinguishing between security events and security incidents by aggregating and analyzing data from various sources to identify anomalies. While security events include any observable occurrences in a network or system, security incidents specifically refer to events that indicate a potential or actual breach requiring immediate response. SIEM platforms enable real-time monitoring, correlation, and alerting, helping organizations detect true security incidents from vast volumes of security events, thereby enhancing threat detection and incident response capabilities.
Impact of Security Events on Organizational Security
Security events are occurrences that may indicate a potential threat but do not necessarily harm the organization, whereas security incidents represent confirmed breaches or attacks causing actual damage or disruption. The impact of security events on organizational security lies in their ability to serve as early warning signs, enabling proactive monitoring and rapid response to mitigate risks before turning into full-scale incidents. Effective event management through continuous monitoring and analytics reduces the likelihood of incidents, protecting critical assets and maintaining business continuity.
Escalation Process: From Event to Incident
A security event is any observable occurrence in a network or system that may indicate a potential security issue, while a security incident is a confirmed event that compromises confidentiality, integrity, or availability. The escalation process begins with event detection, followed by analysis to determine whether the event poses a genuine threat, leading to incident classification. Effective escalation protocols ensure timely response and resource allocation, minimizing damage and facilitating recovery.
Best Practices for Event and Incident Handling
Security incidents require immediate identification, containment, and eradication to minimize damage, while security events involve monitoring and analyzing data for potential threats. Best practices for event and incident handling emphasize continuous network monitoring, timely alerting, and clear escalation protocols. Implementing automated detection tools alongside trained response teams ensures rapid resolution and strengthens overall cybersecurity posture.
Building an Effective Security Incident Response Plan
A security event refers to any observable occurrence in a network or system, while a security incident indicates a confirmed threat that compromises confidentiality, integrity, or availability. Building an effective security incident response plan requires clear differentiation between routine security events and actual incidents to prioritize response efforts efficiently. Incorporating automated detection tools and predefined escalation protocols enhances rapid identification and mitigation of impactful security incidents.
security incident vs security event Infographic
 techiny.com
techiny.com