Authentication verifies a user's identity by requiring credentials such as passwords or biometrics to ensure secure access. Authorization determines the level of access and permissions granted to an authenticated user within a system or application. Effective cybersecurity relies on both processes to protect sensitive data and prevent unauthorized actions.
Table of Comparison
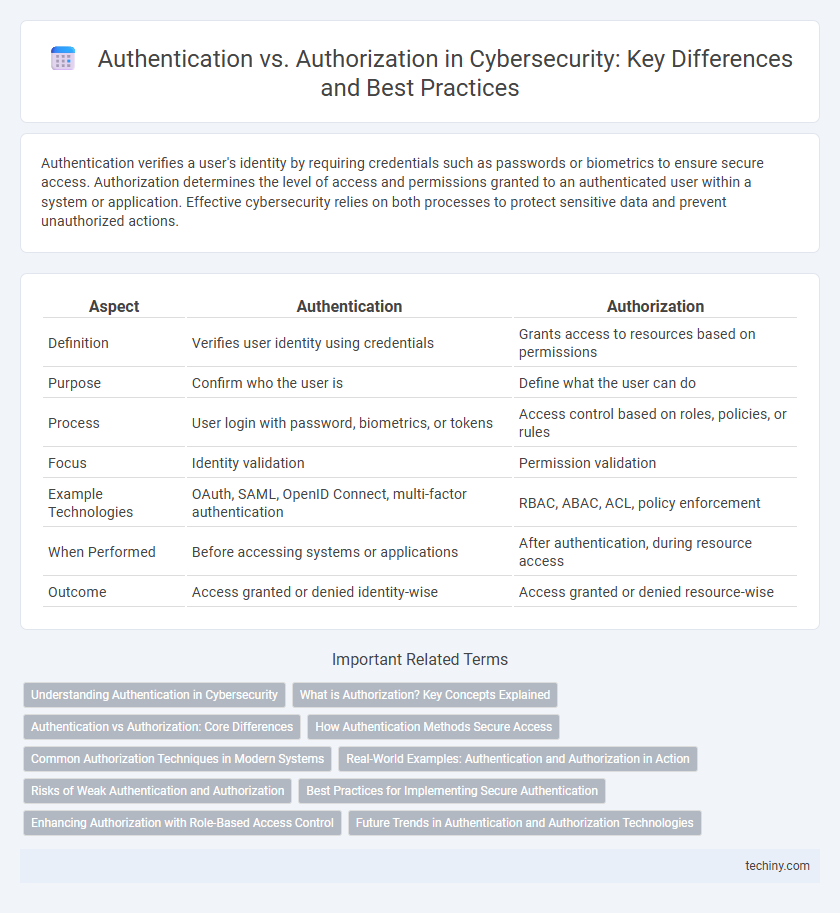
| Aspect | Authentication | Authorization |
|---|---|---|
| Definition | Verifies user identity using credentials | Grants access to resources based on permissions |
| Purpose | Confirm who the user is | Define what the user can do |
| Process | User login with password, biometrics, or tokens | Access control based on roles, policies, or rules |
| Focus | Identity validation | Permission validation |
| Example Technologies | OAuth, SAML, OpenID Connect, multi-factor authentication | RBAC, ABAC, ACL, policy enforcement |
| When Performed | Before accessing systems or applications | After authentication, during resource access |
| Outcome | Access granted or denied identity-wise | Access granted or denied resource-wise |
Understanding Authentication in Cybersecurity
Authentication in cybersecurity involves verifying the identity of a user or system before granting access to resources. This process typically uses credentials such as passwords, biometrics, or multi-factor authentication (MFA) to ensure legitimacy. Effective authentication reduces unauthorized access and protects sensitive data from cyber threats.
What is Authorization? Key Concepts Explained
Authorization is the process of determining a user's access rights and privileges within a system after their identity is verified. It defines what resources, data, or actions a user is permitted to access or perform based on their roles, policies, and permissions. Effective authorization mechanisms prevent unauthorized access and enforce security policies by controlling user activities within applications and networks.
Authentication vs Authorization: Core Differences
Authentication verifies a user's identity by requiring credentials such as passwords, biometrics, or tokens to ensure legitimacy. Authorization determines the access levels and permissions granted to the authenticated user, defining what resources or actions are allowed. The core difference lies in authentication establishing "who you are," while authorization controls "what you can do" within a system.
How Authentication Methods Secure Access
Authentication methods secure access by verifying user identities through techniques such as multi-factor authentication (MFA), biometric verification, and token-based systems. These methods ensure that only legitimate users gain entry by requiring credentials like passwords, fingerprints, or one-time codes, preventing unauthorized access. Robust authentication reduces the risk of security breaches by establishing a trustworthy user validation process before granting system access.
Common Authorization Techniques in Modern Systems
Common authorization techniques in modern systems include role-based access control (RBAC), attribute-based access control (ABAC), and policy-based access control (PBAC). RBAC assigns permissions based on predefined roles, simplifying management for large organizations, while ABAC uses contextual attributes like user location, device type, or time to enforce dynamic access decisions. PBAC combines policies written in formal languages to enable fine-grained, flexible authorization tailored to specific security requirements in cloud and enterprise environments.
Real-World Examples: Authentication and Authorization in Action
Authentication verifies a user's identity by requiring credentials such as passwords, biometrics, or multi-factor authentication before granting access. For example, logging into an online banking app involves authentication through a username and password. Authorization occurs after authentication, determining the user's permissions, such as allowing account holders to view balances but restricting access to administrative features.
Risks of Weak Authentication and Authorization
Weak authentication allows unauthorized access by exploiting stolen credentials, increasing the risk of data breaches and identity theft. Inadequate authorization can lead to privilege escalation, granting users access to sensitive resources beyond their clearance. Both vulnerabilities compromise system integrity and expose organizations to regulatory fines and reputational damage.
Best Practices for Implementing Secure Authentication
Implementing secure authentication requires strong password policies, multi-factor authentication (MFA), and the use of biometric verification to reduce unauthorized access risks. Regularly updating authentication protocols and employing risk-based authentication methods help detect and prevent credential theft. Secure handling of authentication tokens, coupled with encrypted communication channels, ensures robust protection against cyber threats.
Enhancing Authorization with Role-Based Access Control
Enhancing authorization through Role-Based Access Control (RBAC) strengthens cybersecurity by ensuring users can only access resources aligned with their assigned roles. RBAC reduces the risk of unauthorized access by enforcing strict permission policies based on organizational roles and responsibilities. This approach streamlines access management, improves compliance, and minimizes potential attack surfaces within enterprise systems.
Future Trends in Authentication and Authorization Technologies
Future trends in authentication and authorization technologies emphasize biometric-based systems, such as facial recognition and fingerprint scanning, coupled with behavioral analytics to enhance security. Decentralized identity frameworks using blockchain technology promise greater user control and reduced fraud risks in access management. Adaptive authentication methods, leveraging AI to continuously evaluate risk factors, are expected to become standard in protecting critical digital assets.
Authentication vs Authorization Infographic
 techiny.com
techiny.com