Symmetric encryption uses a single key for both encryption and decryption, offering faster performance ideal for large data volumes but requiring secure key distribution. Asymmetric encryption employs a pair of keys--public and private--to enhance security, enabling secure key exchange and digital signatures despite slower processing speeds. Combining both methods in hybrid encryption leverages the speed of symmetric algorithms with the security of asymmetric systems, optimizing overall cybersecurity protocols.
Table of Comparison
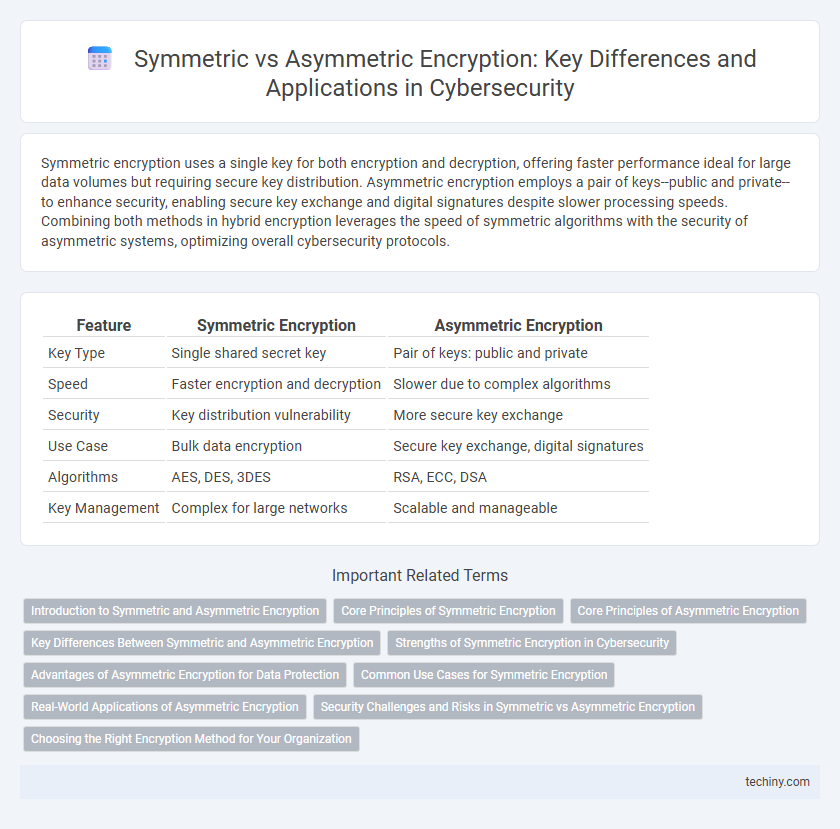
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Type | Single shared secret key | Pair of keys: public and private |
| Speed | Faster encryption and decryption | Slower due to complex algorithms |
| Security | Key distribution vulnerability | More secure key exchange |
| Use Case | Bulk data encryption | Secure key exchange, digital signatures |
| Algorithms | AES, DES, 3DES | RSA, ECC, DSA |
| Key Management | Complex for large networks | Scalable and manageable |
Introduction to Symmetric and Asymmetric Encryption
Symmetric encryption uses a single secret key for both encryption and decryption, enabling faster data processing but requiring secure key distribution. Asymmetric encryption employs a pair of mathematically linked keys--public and private--allowing secure communication without sharing the private key, crucial for digital signatures and key exchange. Understanding the distinctions between symmetric and asymmetric encryption forms the foundation for implementing robust cybersecurity protocols.
Core Principles of Symmetric Encryption
Symmetric encryption relies on a single secret key shared between the sender and receiver to both encrypt and decrypt data, ensuring confidentiality through fast processing speeds and efficient resource usage. The core principle revolves around maintaining this key's secrecy since unauthorized access compromises the entire communication channel. Symmetric algorithms like AES and DES are widely adopted for bulk data encryption due to their simplicity and performance advantages.
Core Principles of Asymmetric Encryption
Asymmetric encryption relies on a pair of mathematically linked keys: a public key for encryption and a private key for decryption, ensuring that only the key owner can access the encrypted data. This key pair generation involves complex algorithms such as RSA, ECC, or DSA, which provide enhanced security compared to symmetric methods by eliminating the need to share a secret key. The core principle centers on secure communication and data authenticity, enabling functionalities like digital signatures and key exchange without direct key sharing.
Key Differences Between Symmetric and Asymmetric Encryption
Symmetric encryption uses a single key for both encryption and decryption, making it faster and suitable for large data volumes, whereas asymmetric encryption relies on a pair of public and private keys to secure data exchange. Symmetric algorithms like AES are computationally efficient but require secure key distribution, while asymmetric algorithms such as RSA enable secure communication without sharing secret keys beforehand. The core difference lies in symmetric encryption's reliance on a shared secret key versus asymmetric encryption's use of mathematically linked key pairs for enhanced security in key exchange.
Strengths of Symmetric Encryption in Cybersecurity
Symmetric encryption offers high-speed data processing and efficiency, making it ideal for encrypting large volumes of information in cybersecurity applications. Its use of a single shared key simplifies key management in controlled environments, providing strong protection against unauthorized access. The algorithm's lower computational overhead enhances performance without compromising confidentiality, especially in real-time communication systems.
Advantages of Asymmetric Encryption for Data Protection
Asymmetric encryption enhances data protection by using a pair of keys--public and private--which eliminates the need to share secret keys and reduces the risk of interception. Its capability to provide digital signatures ensures authentication and non-repudiation, critical for secure communication and data integrity. This encryption method supports secure key exchange over untrusted channels, making it ideal for encrypting sensitive information in networks and online transactions.
Common Use Cases for Symmetric Encryption
Symmetric encryption is primarily used for bulk data encryption due to its high-speed processing capabilities, making it ideal for securing large volumes of information such as database files, disk drives, and network traffic. Common use cases include encrypting data at rest within enterprise storage systems and encrypting data in transit in Virtual Private Networks (VPNs) to ensure confidentiality and integrity. Additionally, symmetric encryption algorithms like AES are widely implemented in securing communication channels such as TLS for web browsers and SSL for email transmissions.
Real-World Applications of Asymmetric Encryption
Asymmetric encryption powers secure online communications by enabling encrypted key exchanges in protocols like SSL/TLS, safeguarding web browsing and e-commerce transactions. It underpins digital signature technologies that verify document authenticity and integrity in legal and financial sectors. Email security solutions often leverage asymmetric encryption to facilitate secure message transmission through standards such as PGP and S/MIME.
Security Challenges and Risks in Symmetric vs Asymmetric Encryption
Symmetric encryption faces security challenges due to key distribution and management risks, as sharing a single secret key increases vulnerability to interception and unauthorized access. Asymmetric encryption mitigates these risks by using a pair of public and private keys, but it incurs higher computational costs and potential risks related to key length and algorithm strength. Both methods require robust implementation and key protection strategies to prevent cryptographic attacks such as man-in-the-middle, brute force, and cryptanalysis.
Choosing the Right Encryption Method for Your Organization
Choosing the right encryption method depends on organizational needs, as symmetric encryption offers faster processing suitable for large data volumes and real-time applications, while asymmetric encryption provides enhanced security through key pair mechanisms ideal for secure communication and digital signatures. Organizations handling sensitive transactions or requiring secure key exchanges often benefit from asymmetric encryption, whereas symmetric encryption remains effective for internal data protection and bulk data encryption. Evaluating factors like data sensitivity, performance requirements, and key management capabilities ensures the optimal balance between security and efficiency in your cybersecurity strategy.
Symmetric Encryption vs Asymmetric Encryption Infographic
 techiny.com
techiny.com