Block ciphers encrypt fixed-size blocks of data using symmetric keys, ensuring strong security through complex algorithms like AES, making them ideal for data-at-rest protection. Stream ciphers encrypt data one bit or byte at a time, offering high speed and low latency beneficial for real-time communication and streaming applications. Selecting between block and stream ciphers depends on the specific requirements of performance and security within a cybersecurity framework.
Table of Comparison
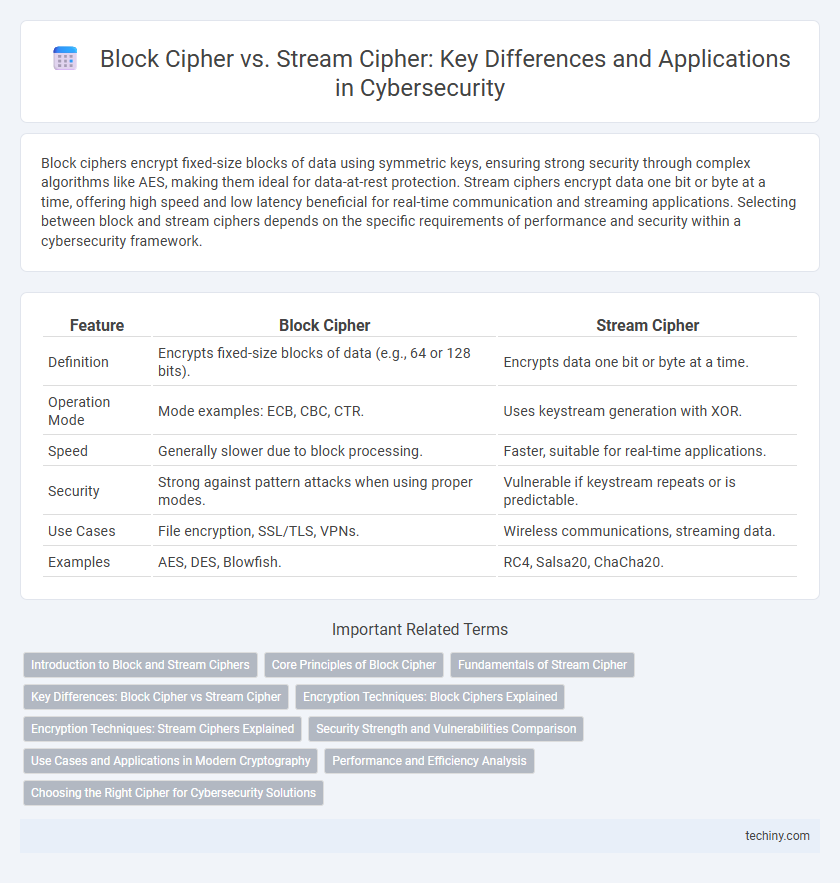
| Feature | Block Cipher | Stream Cipher |
|---|---|---|
| Definition | Encrypts fixed-size blocks of data (e.g., 64 or 128 bits). | Encrypts data one bit or byte at a time. |
| Operation Mode | Mode examples: ECB, CBC, CTR. | Uses keystream generation with XOR. |
| Speed | Generally slower due to block processing. | Faster, suitable for real-time applications. |
| Security | Strong against pattern attacks when using proper modes. | Vulnerable if keystream repeats or is predictable. |
| Use Cases | File encryption, SSL/TLS, VPNs. | Wireless communications, streaming data. |
| Examples | AES, DES, Blowfish. | RC4, Salsa20, ChaCha20. |
Introduction to Block and Stream Ciphers
Block ciphers encrypt fixed-size blocks of plaintext, typically 64 or 128 bits, using a symmetric key and complex algorithms like AES or DES to ensure data confidentiality. Stream ciphers encrypt data one bit or byte at a time, generating a pseudorandom keystream combined with plaintext through XOR operations, exemplified by algorithms such as RC4 and Salsa20. Both ciphers serve cryptographic purposes but differ in performance, security, and use cases, with block ciphers favored for bulk data encryption and stream ciphers suited for real-time communication.
Core Principles of Block Cipher
Block ciphers operate by encrypting fixed-size blocks of plaintext, typically 64 or 128 bits, using symmetric keys and complex substitution-permutation networks to ensure confidentiality. Their core principle involves transforming each plaintext block into ciphertext through multiple rounds of confusion and diffusion, enhancing resistance against cryptanalysis. This approach contrasts with stream ciphers by providing deterministic output blocks and stronger structural security for bulk data encryption.
Fundamentals of Stream Cipher
Stream ciphers encrypt plaintext one bit or byte at a time using a pseudorandom keystream generated from a secret key, making them suitable for real-time data processing and low-latency applications. The fundamental structure relies on a keystream generator, often implemented with linear feedback shift registers (LFSRs) or nonlinear algorithms, to produce a long, non-repeating sequence that combines with plaintext through bitwise XOR operations. Stream ciphers excel at encrypting streaming data efficiently but require careful key management and synchronization to prevent vulnerabilities such as key reuse and keystream predictability.
Key Differences: Block Cipher vs Stream Cipher
Block ciphers encrypt data in fixed-size blocks, typically 64 or 128 bits, using a symmetric key, ensuring strong security for bulk data encryption. Stream ciphers process data one bit or byte at a time, making them suitable for real-time applications with lower latency requirements. The main key difference lies in their operation mode: block ciphers provide robust security with potential latency, while stream ciphers prioritize speed and efficiency with simpler key management.
Encryption Techniques: Block Ciphers Explained
Block ciphers encrypt data in fixed-size blocks, typically 128 bits, using symmetric key algorithms like AES and DES to transform plaintext into ciphertext through multiple complex rounds of substitution and permutation. These techniques ensure high security by applying key-dependent transformations that provide confusion and diffusion, making block ciphers resistant to cryptanalysis. Block ciphers support various modes of operation such as CBC, ECB, and GCM, enhancing encryption versatility and data integrity in cybersecurity applications.
Encryption Techniques: Stream Ciphers Explained
Stream ciphers encrypt plaintext by processing individual bits or bytes sequentially, generating a pseudorandom keystream combined with the plaintext using XOR operations. This approach enables high-speed encryption suitable for real-time applications such as secure voice communication and streaming data. Compared to block ciphers, stream ciphers offer lower latency and reduced computational overhead but require careful key management to avoid vulnerabilities like key reuse.
Security Strength and Vulnerabilities Comparison
Block ciphers provide robust security by encrypting fixed-size data blocks, making them highly resistant to brute-force attacks and providing strong confidentiality through modes like CBC and GCM. Stream ciphers encrypt data one bit or byte at a time, offering speed and low latency but are more vulnerable to key reuse and initialization vector issues, which can lead to significant security breaches. Evaluating both, block ciphers generally deliver higher security strength in most cryptographic applications, while stream ciphers require careful key management to avoid their inherent vulnerabilities.
Use Cases and Applications in Modern Cryptography
Block ciphers are widely used in data encryption standards such as AES, making them ideal for securing large volumes of data in applications like file encryption, database protection, and VPNs. Stream ciphers excel in real-time communication scenarios such as secure voice calls and streaming media due to their ability to encrypt data on a bit-by-bit basis with low latency. Modern cryptographic systems often combine block and stream ciphers to leverage the strengths of each, optimizing security and performance across diverse digital environments.
Performance and Efficiency Analysis
Block ciphers encrypt data in fixed-size blocks, offering strong security but often requiring more processing power and memory, which can impact performance in resource-constrained environments. Stream ciphers process plaintext one bit or byte at a time, generally providing faster encryption speeds and lower latency, making them ideal for real-time applications and devices with limited computational resources. Performance efficiency in cryptographic systems depends on the specific use case, with stream ciphers excelling in speed-sensitive scenarios while block ciphers suit applications demanding robust security and error propagation control.
Choosing the Right Cipher for Cybersecurity Solutions
Block ciphers encrypt data in fixed-size blocks, making them ideal for securing large amounts of static data with strong integrity guarantees, while stream ciphers encrypt data bit-by-bit or byte-by-byte, offering speed and efficiency for real-time applications like video streaming or network communication. Selecting between block and stream ciphers depends on specific cybersecurity requirements, including data volume, performance constraints, and resistance to known cryptographic attacks such as replay or tampering. Evaluating algorithms like AES for block ciphers and RC4 or ChaCha20 for stream ciphers ensures optimal encryption suited to system architecture and threat models.
Block Cipher vs Stream Cipher Infographic
 techiny.com
techiny.com