Malware analysis concentrates on dissecting malicious software to understand its behavior, origin, and potential impact on systems. Forensic analysis involves the collection, preservation, and examination of digital evidence to reconstruct cyber incidents and support legal proceedings. Both disciplines are crucial in cybersecurity, providing complementary insights for threat mitigation and incident response.
Table of Comparison
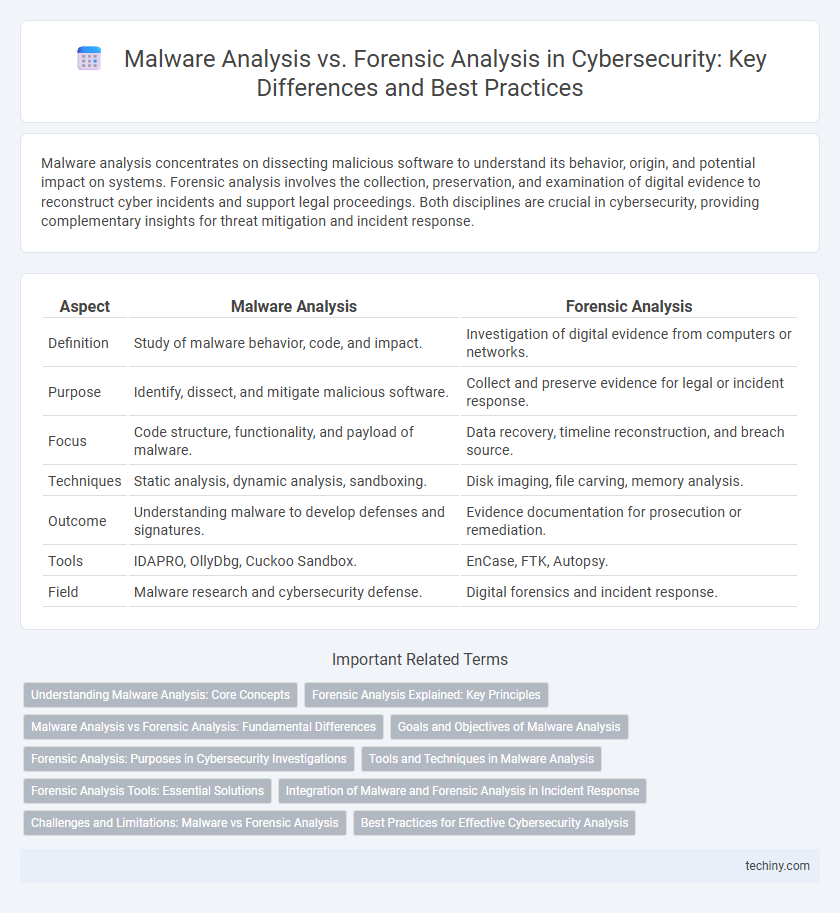
| Aspect | Malware Analysis | Forensic Analysis |
|---|---|---|
| Definition | Study of malware behavior, code, and impact. | Investigation of digital evidence from computers or networks. |
| Purpose | Identify, dissect, and mitigate malicious software. | Collect and preserve evidence for legal or incident response. |
| Focus | Code structure, functionality, and payload of malware. | Data recovery, timeline reconstruction, and breach source. |
| Techniques | Static analysis, dynamic analysis, sandboxing. | Disk imaging, file carving, memory analysis. |
| Outcome | Understanding malware to develop defenses and signatures. | Evidence documentation for prosecution or remediation. |
| Tools | IDAPRO, OllyDbg, Cuckoo Sandbox. | EnCase, FTK, Autopsy. |
| Field | Malware research and cybersecurity defense. | Digital forensics and incident response. |
Understanding Malware Analysis: Core Concepts
Malware analysis involves dissecting malicious software to understand its behavior, origin, and potential impact, using techniques such as static analysis, dynamic analysis, and sandboxing. Core concepts include identifying malware signatures, unpacking obfuscated code, and examining payload execution to detect threats and develop countermeasures. This process is essential for threat intelligence, incident response, and enhancing defensive cybersecurity strategies.
Forensic Analysis Explained: Key Principles
Forensic analysis in cybersecurity involves the systematic examination of digital evidence to determine the origin, method, and impact of cyber incidents. It relies on principles such as data integrity preservation, chain of custody maintenance, and comprehensive documentation to ensure evidence admissibility in legal proceedings. Techniques include recovering deleted files, analyzing system logs, and tracing attacker activities to support incident response and litigation.
Malware Analysis vs Forensic Analysis: Fundamental Differences
Malware analysis focuses on dissecting malicious software to understand its behavior, origin, and impact, employing static and dynamic techniques to identify signatures and payloads. Forensic analysis involves investigating digital evidence from devices or networks to reconstruct events and determine the scope of a security breach, using methods like memory analysis, disk imaging, and timeline creation. While malware analysis targets the malicious code itself, forensic analysis provides a broader investigation of the compromise and its effects on systems and data.
Goals and Objectives of Malware Analysis
Malware analysis aims to identify, dissect, and understand malicious software to determine its origin, functionality, and impact on targeted systems. The primary objectives include uncovering attack vectors, detecting behavioral patterns for threat mitigation, and developing effective countermeasures such as signatures or patches. Unlike forensic analysis, which focuses on evidence preservation and incident reconstruction, malware analysis concentrates on proactive defense and real-time threat intelligence.
Forensic Analysis: Purposes in Cybersecurity Investigations
Forensic analysis in cybersecurity investigations focuses on identifying, preserving, and reconstructing digital evidence to determine the scope and impact of a security breach. It involves systematic data collection from compromised systems, enabling attribution of attacks and supporting legal proceedings. This process is crucial for understanding attacker methodologies and strengthening future defense mechanisms.
Tools and Techniques in Malware Analysis
Malware analysis employs dynamic and static techniques using tools such as IDA Pro, Ghidra, and Cuckoo Sandbox to dissect malicious code behavior and structure. Analysts utilize sandbox environments to observe malware execution in real-time, enabling behavior-based detection and reverse engineering. Signature-based detection, heuristic analysis, and code emulation are crucial methods for uncovering malware functionalities and developing mitigation strategies.
Forensic Analysis Tools: Essential Solutions
Forensic analysis tools play a critical role in cybersecurity by enabling investigators to recover, examine, and preserve digital evidence from compromised systems. Essential solutions such as EnCase, FTK (Forensic Toolkit), and Autopsy provide comprehensive features for data acquisition, timeline reconstruction, and file integrity verification. These tools facilitate detailed insights into cyber incidents, supporting legal proceedings and enhancing overall threat response strategies.
Integration of Malware and Forensic Analysis in Incident Response
Integrating malware analysis with forensic analysis enhances incident response by providing a comprehensive understanding of cyber threats, enabling rapid identification and containment of malicious activities. Detailed examination of malware behavior combined with forensic evidence uncovers attack vectors, timelines, and affected systems, improving threat mitigation strategies. This holistic approach accelerates root cause analysis and supports robust recovery processes in cybersecurity operations.
Challenges and Limitations: Malware vs Forensic Analysis
Malware analysis faces challenges such as rapidly evolving malware techniques, obfuscation, and encryption that complicate detection and behavior understanding. Forensic analysis is limited by data volatility, incomplete evidence, and potential tampering, which hinder accurate reconstruction of cyber incidents. Both fields require continuous updates on threat intelligence and advanced tools to overcome these evolving obstacles in cybersecurity investigations.
Best Practices for Effective Cybersecurity Analysis
Effective cybersecurity analysis requires a combination of malware analysis and forensic analysis, each focusing on distinct aspects of threat investigation. Malware analysis involves dissecting malicious code to understand its behavior, origin, and potential impact, while forensic analysis centers on collecting and preserving digital evidence for incident response and legal proceedings. Best practices include maintaining detailed logs, using sandbox environments for safe threat evaluation, and integrating automated tools with expert judgment to enhance accuracy and response time.
Malware Analysis vs Forensic Analysis Infographic
 techiny.com
techiny.com