Hardening involves configuring systems to minimize vulnerabilities by disabling unnecessary services and enforcing strict security policies, thereby reducing the attack surface. Patching addresses known security flaws by applying updates and fixes to software and firmware, closing exploitable gaps that could be targeted by attackers. Combining hardening and patching offers a comprehensive cybersecurity strategy, ensuring both proactive defense and timely remediation of vulnerabilities.
Table of Comparison
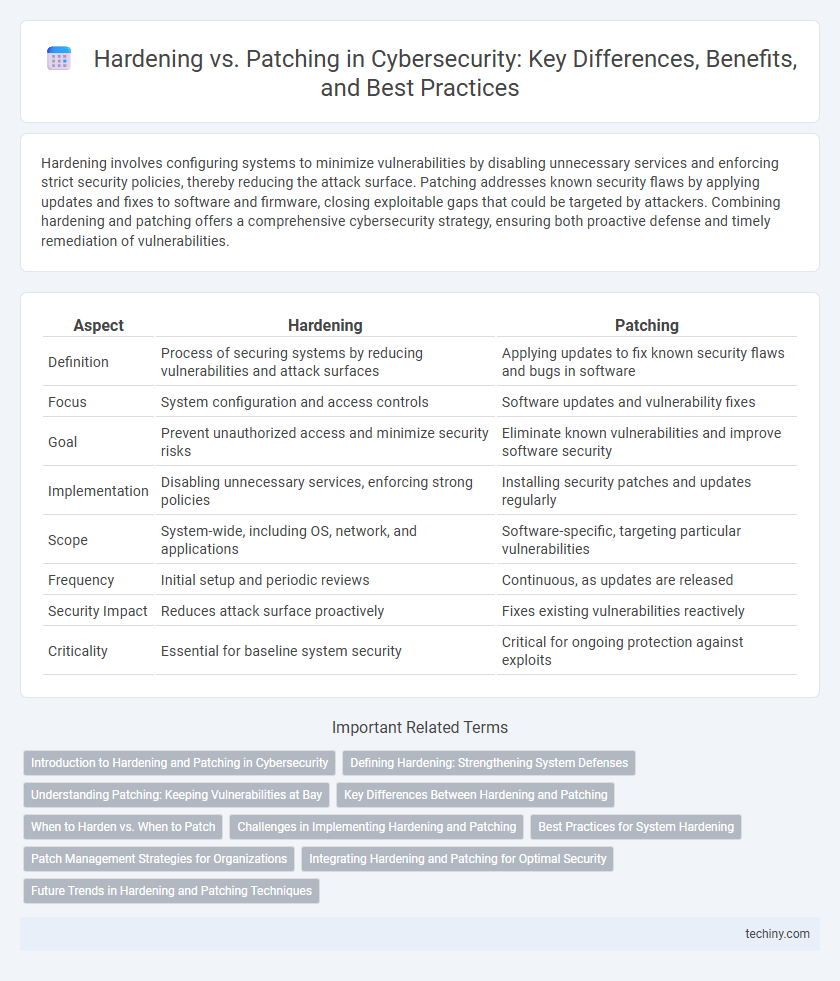
| Aspect | Hardening | Patching |
|---|---|---|
| Definition | Process of securing systems by reducing vulnerabilities and attack surfaces | Applying updates to fix known security flaws and bugs in software |
| Focus | System configuration and access controls | Software updates and vulnerability fixes |
| Goal | Prevent unauthorized access and minimize security risks | Eliminate known vulnerabilities and improve software security |
| Implementation | Disabling unnecessary services, enforcing strong policies | Installing security patches and updates regularly |
| Scope | System-wide, including OS, network, and applications | Software-specific, targeting particular vulnerabilities |
| Frequency | Initial setup and periodic reviews | Continuous, as updates are released |
| Security Impact | Reduces attack surface proactively | Fixes existing vulnerabilities reactively |
| Criticality | Essential for baseline system security | Critical for ongoing protection against exploits |
Introduction to Hardening and Patching in Cybersecurity
Hardening in cybersecurity involves configuring systems and software to minimize vulnerabilities by disabling unnecessary services, applying strict access controls, and enforcing security policies. Patching is the process of applying updates or fixes to software to address known security vulnerabilities and improve system stability. Both hardening and patching are critical components for maintaining robust defense mechanisms against cyber threats.
Defining Hardening: Strengthening System Defenses
Hardening involves configuring systems to reduce vulnerabilities by disabling unnecessary services, enforcing strong authentication, and applying strict access controls. This proactive approach establishes a resilient security baseline that limits attack surfaces before threats exploit weaknesses. Effective hardening complements patching by reinforcing defenses beyond software updates, ensuring comprehensive protection against evolving cyber threats.
Understanding Patching: Keeping Vulnerabilities at Bay
Patching involves regularly updating software to fix security vulnerabilities, preventing exploitation by cyber attackers. Timely deployment of patches is critical for maintaining system integrity and protecting sensitive data from breaches. Automated patch management tools enhance efficiency, ensuring prompt correction of known security flaws in complex IT environments.
Key Differences Between Hardening and Patching
Hardening involves proactively configuring systems and networks to reduce vulnerabilities by disabling unnecessary services, applying strict access controls, and enforcing security policies, whereas patching focuses on reactive measures, applying software updates to fix known security flaws and bugs. Hardening establishes a secure baseline environment by minimizing attack surfaces, while patching addresses specific weaknesses as they are discovered to prevent exploitation. Both practices are essential in cybersecurity, but hardening provides foundational security, and patching ensures ongoing protection against emerging threats.
When to Harden vs. When to Patch
Hardening is most effective during the initial deployment phase of a system, where minimizing attack surfaces and configuring secure settings proactively reduce vulnerabilities. Patching becomes critical after discovering specific vulnerabilities or security flaws, requiring targeted updates to fix known issues and prevent exploitation. Organizations should prioritize hardening to establish a secure baseline and apply patches continuously as threats evolve and new vulnerabilities are identified.
Challenges in Implementing Hardening and Patching
Implementing hardening and patching in cybersecurity faces challenges such as compatibility issues with existing systems, the complexity of continuously updating configurations, and resource constraints for thorough vulnerability assessments. Organizations struggle with balancing operational continuity while applying patches or hardening measures without causing service disruptions. Effective deployment requires skilled personnel and automation tools to manage the volume and frequency of security updates efficiently.
Best Practices for System Hardening
System hardening involves proactively reducing vulnerabilities by configuring systems securely, disabling unnecessary services, and enforcing strict access controls to minimize attack surfaces. Best practices include applying the principle of least privilege, regularly updating security policies, and conducting thorough system audits to ensure compliance with hardening standards. This approach complements patching by preventing exploitation of unknown or unpatched vulnerabilities through robust system configurations.
Patch Management Strategies for Organizations
Effective patch management strategies prioritize timely identification and deployment of security updates to close vulnerabilities before exploitation. Organizations implement automated patching systems combined with rigorous testing protocols to ensure compatibility and minimize downtime. Integrating patch management with hardening practices, such as reducing attack surfaces and enforcing strict access controls, enhances overall cybersecurity resilience.
Integrating Hardening and Patching for Optimal Security
Integrating hardening and patching creates a robust cybersecurity strategy by minimizing vulnerabilities and strengthening system defenses simultaneously. Hardening reduces potential attack surfaces through secure configurations while patching addresses known software flaws, ensuring comprehensive protection. Combining these practices enhances resilience against exploits and reduces the risk of cyber threats effectively.
Future Trends in Hardening and Patching Techniques
Future trends in cybersecurity emphasize the integration of AI-driven hardening techniques with adaptive patch management systems, enabling real-time vulnerability detection and automated defense mechanisms. Machine learning algorithms will increasingly analyze behavioral data to predict and neutralize threats before patches are deployed, reducing window periods of exposure. Cloud-native security solutions and zero-trust architectures are set to redefine hardening strategies, ensuring continuous protection in dynamic, distributed environments.
Hardening vs Patching Infographic
 techiny.com
techiny.com