Phishing involves widespread attempts to deceive users into revealing personal information through generic emails or messages, while spear phishing targets specific individuals or organizations with customized and highly convincing content. Spear phishing attacks exploit detailed knowledge about the target to increase success rates, making them more dangerous and harder to detect than traditional phishing. Implementing advanced email filtering and user training can significantly reduce the risk associated with both phishing and spear phishing threats.
Table of Comparison
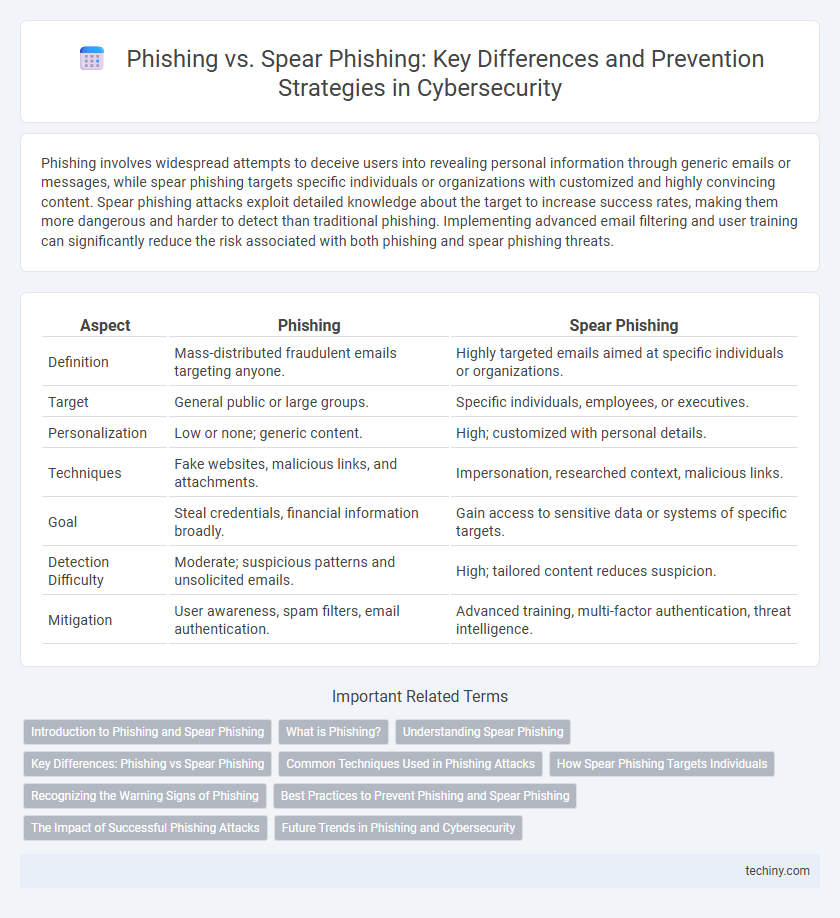
| Aspect | Phishing | Spear Phishing |
|---|---|---|
| Definition | Mass-distributed fraudulent emails targeting anyone. | Highly targeted emails aimed at specific individuals or organizations. |
| Target | General public or large groups. | Specific individuals, employees, or executives. |
| Personalization | Low or none; generic content. | High; customized with personal details. |
| Techniques | Fake websites, malicious links, and attachments. | Impersonation, researched context, malicious links. |
| Goal | Steal credentials, financial information broadly. | Gain access to sensitive data or systems of specific targets. |
| Detection Difficulty | Moderate; suspicious patterns and unsolicited emails. | High; tailored content reduces suspicion. |
| Mitigation | User awareness, spam filters, email authentication. | Advanced training, multi-factor authentication, threat intelligence. |
Introduction to Phishing and Spear Phishing
Phishing is a widespread cyber attack method where attackers use deceptive emails or websites to steal sensitive information such as passwords, credit card numbers, or personal data. Spear phishing is a more targeted form of phishing, where attackers customize their messages to a specific individual or organization to increase the chances of success. Both techniques exploit social engineering tactics but differ in scope and precision of the attack.
What is Phishing?
Phishing is a cyberattack technique where attackers impersonate legitimate entities to steal sensitive information such as usernames, passwords, and credit card details through deceptive emails or websites. It relies on mass targeting and generic messaging to trick recipients into revealing confidential data or downloading malicious software. Phishing remains one of the most common and effective methods used in cybersecurity breaches and identity theft.
Understanding Spear Phishing
Spear phishing is a highly targeted form of phishing that uses personalized information about its victim to craft convincing and deceptive messages, increasing the likelihood of successful attacks. Unlike general phishing, which casts a wide net with generic emails, spear phishing leverages social engineering tactics to exploit trust and manipulate specific individuals or organizations. Understanding spear phishing involves recognizing its tailored approach, often involving pre-collected data, to deliver malware or steal sensitive credentials discreetly.
Key Differences: Phishing vs Spear Phishing
Phishing attacks cast a wide net using generic emails to trick victims into revealing sensitive information, whereas spear phishing targets specific individuals or organizations with personalized messages crafted from detailed research. Spear phishing often involves social engineering tactics aimed at high-value targets, increasing the likelihood of successful infiltration and data theft. Understanding these differences is crucial for implementing tailored cybersecurity measures and enhancing detection protocols.
Common Techniques Used in Phishing Attacks
Phishing attacks commonly use deceptive emails, fake websites, and social engineering tactics to trick victims into revealing sensitive information such as passwords and credit card numbers. Spear phishing, a more targeted variant, involves personalized messages crafted using specific details about the recipient to increase the likelihood of success. Both techniques often exploit urgency and fear to manipulate users into clicking malicious links or downloading infected attachments.
How Spear Phishing Targets Individuals
Spear phishing targets individuals by using personalized information gathered from social media, email correspondence, or public databases to craft convincing messages that appear legitimate. These attacks exploit specific details such as the victim's name, job title, or interests to increase the likelihood of engagement and reduce suspicion. Unlike generic phishing attempts, spear phishing requires extensive reconnaissance to deceive high-value targets within organizations effectively.
Recognizing the Warning Signs of Phishing
Phishing attempts often display generic greetings, urgent language, and suspicious links or attachments designed to steal sensitive information. Spear phishing targets specific individuals or organizations with personalized messages that appear highly credible by referencing real contacts or recent activities. Recognizing inconsistencies in sender information, unexpected requests for confidential data, and unusual email formats are critical warning signs to prevent falling victim to these cyber threats.
Best Practices to Prevent Phishing and Spear Phishing
Implementing multi-factor authentication and ongoing employee training are essential best practices to prevent both phishing and spear phishing attacks. Utilizing advanced email filtering technologies and regularly updating security protocols significantly reduce the risk of successful intrusions. Continuous monitoring of network traffic and promptly reporting suspicious emails further strengthen organizational defenses against targeted cyber threats.
The Impact of Successful Phishing Attacks
Successful phishing attacks can lead to significant financial losses averaging $4.65 million per incident, data breaches compromising millions of users' sensitive information, and severe reputational damage for organizations. Spear phishing, which targets specific individuals with personalized messages, typically results in higher success rates and deeper infiltration into corporate networks. These attacks often enable unauthorized access to confidential systems, facilitating identity theft, fraud, and long-term espionage.
Future Trends in Phishing and Cybersecurity
Phishing attacks are increasingly leveraging artificial intelligence and machine learning to create highly personalized and convincing spear phishing campaigns, targeting specific individuals or organizations with tailored messages. Future trends indicate the rise of deepfake technology and synthetic media in phishing attempts, making detection more challenging for traditional security systems. Enhanced cybersecurity measures will rely on behavioral analytics, AI-driven threat intelligence, and zero-trust architectures to combat evolving phishing techniques.
Phishing vs Spear Phishing Infographic
 techiny.com
techiny.com