Malware is a broad category of malicious software designed to disrupt, damage, or gain unauthorized access to computer systems, while spyware specifically aims to secretly monitor and collect user information without consent. Spyware often operates covertly, tracking activities such as keystrokes, browsing habits, and personal data, which can lead to privacy breaches and identity theft. Effective cybersecurity measures include using updated antivirus programs and firewalls to detect and remove both malware and spyware threats.
Table of Comparison
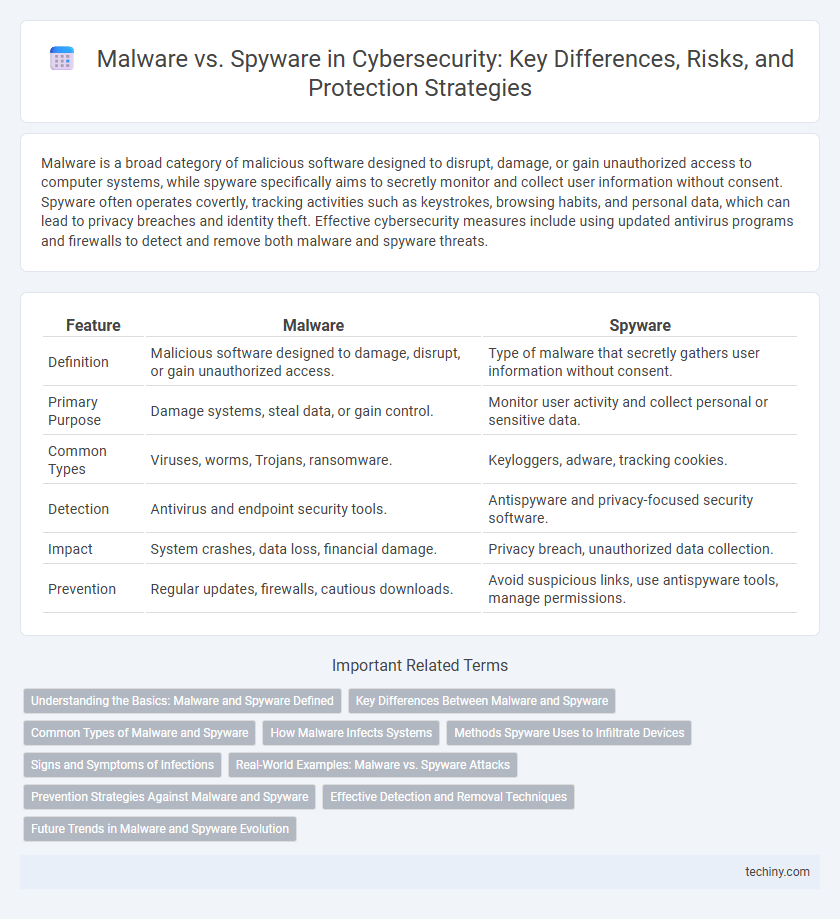
| Feature | Malware | Spyware |
|---|---|---|
| Definition | Malicious software designed to damage, disrupt, or gain unauthorized access. | Type of malware that secretly gathers user information without consent. |
| Primary Purpose | Damage systems, steal data, or gain control. | Monitor user activity and collect personal or sensitive data. |
| Common Types | Viruses, worms, Trojans, ransomware. | Keyloggers, adware, tracking cookies. |
| Detection | Antivirus and endpoint security tools. | Antispyware and privacy-focused security software. |
| Impact | System crashes, data loss, financial damage. | Privacy breach, unauthorized data collection. |
| Prevention | Regular updates, firewalls, cautious downloads. | Avoid suspicious links, use antispyware tools, manage permissions. |
Understanding the Basics: Malware and Spyware Defined
Malware is a broad category of malicious software designed to damage, disrupt, or gain unauthorized access to computer systems, while spyware is a specific type of malware that secretly monitors and collects user information without consent. Malware includes viruses, worms, trojans, ransomware, and spyware, each with distinct purposes and methods of infection. Understanding these definitions helps in identifying threats and implementing appropriate cybersecurity measures to protect sensitive data and system integrity.
Key Differences Between Malware and Spyware
Malware encompasses a broad range of malicious software designed to harm or exploit any programmable device, system, or network, including viruses, worms, ransomware, and spyware. Spyware is a specific type of malware aimed at stealthily monitoring user activities, capturing sensitive information such as login credentials, browsing habits, and personal data without explicit consent. While malware's primary goal can vary from destruction to data theft, spyware specifically serves as a covert surveillance tool, often enabling unauthorized data transmission to third parties.
Common Types of Malware and Spyware
Common types of malware include viruses, worms, trojans, ransomware, and rootkits, each designed to disrupt systems, steal data, or demand ransom. Spyware, a subset of malware, primarily consists of keyloggers, adware, and tracking cookies that covertly collect user information and monitor activities. Understanding these distinctions is critical for implementing effective cybersecurity measures against data breaches and unauthorized access.
How Malware Infects Systems
Malware infects systems through various attack vectors such as phishing emails, malicious downloads, and exploit kits targeting software vulnerabilities. Once executed, it can replicate, steal sensitive data, or damage system files, compromising security and performance. Spyware, a subtype of malware, specifically focuses on covertly monitoring user activities to capture confidential information without consent.
Methods Spyware Uses to Infiltrate Devices
Spyware infiltrates devices primarily through deceptive methods such as phishing emails, malicious software downloads, and exploit kits that take advantage of software vulnerabilities. It often hides within seemingly legitimate applications or browser extensions, enabling it to silently monitor user activities and capture sensitive information. This stealthy infiltration contrasts with broader malware tactics, focusing narrowly on surveillance and data extraction rather than system disruption.
Signs and Symptoms of Infections
Malware infection signs include sudden system slowdowns, frequent crashes, and unauthorized access to files or accounts. Spyware symptoms often involve unexpected pop-up ads, changes in browser settings, and decreased device performance due to data being secretly transmitted. Both malware and spyware can cause unusual network activity and increased CPU usage, indicating a compromised system.
Real-World Examples: Malware vs. Spyware Attacks
Real-world examples highlight Malware like the WannaCry ransomware that crippled global systems by encrypting data and demanding ransom payments, whereas Spyware such as the Pegasus software covertly infiltrated smartphones to extract sensitive information without user consent. Malware attacks often cause immediate and visible damage, disrupting operations in sectors including healthcare and finance. Spyware threats primarily focus on stealthy data theft, enabling state-sponsored espionage and corporate surveillance.
Prevention Strategies Against Malware and Spyware
Effective prevention strategies against malware and spyware include regularly updating antivirus software to detect and remove emerging threats, implementing strong firewall protections to monitor and control network traffic, and educating users about phishing scams and suspicious downloads. Employing advanced endpoint security solutions and conducting frequent system scans help identify and quarantine malicious software before it compromises sensitive data. Regular software patching and restricting user permissions minimize vulnerabilities that malware and spyware often exploit.
Effective Detection and Removal Techniques
Malware detection relies heavily on signature-based and behavior-based analysis to identify and quarantine harmful code, while spyware detection focuses on monitoring unauthorized data transmission and access patterns. Effective removal techniques for malware involve using advanced antivirus tools and system restoration, whereas spyware often requires specialized antispyware programs that target stealthy data collection processes. Employing comprehensive endpoint protection platforms integrating real-time threat intelligence enhances the success rate in both malware and spyware mitigation.
Future Trends in Malware and Spyware Evolution
Future trends in malware and spyware evolution reveal increasing sophistication with the integration of artificial intelligence, enabling adaptive evasion techniques that bypass traditional detection systems. Emerging threats leverage machine learning algorithms to create polymorphic code and stealthy spying mechanisms, complicating cybersecurity defense frameworks. Advancements in quantum computing also pose potential risks for encryption vulnerabilities, accelerating the need for quantum-resistant security solutions against evolving malware and spyware attacks.
Malware vs Spyware Infographic
 techiny.com
techiny.com