Cyber espionage involves covertly infiltrating computer systems to steal sensitive information, often targeting government or corporate secrets for strategic advantage. Cyber sabotage aims to disrupt, damage, or destroy digital infrastructure, causing operational failures or halting critical services. Understanding these distinctions is crucial for developing tailored cybersecurity defenses against data theft and system disruption.
Table of Comparison
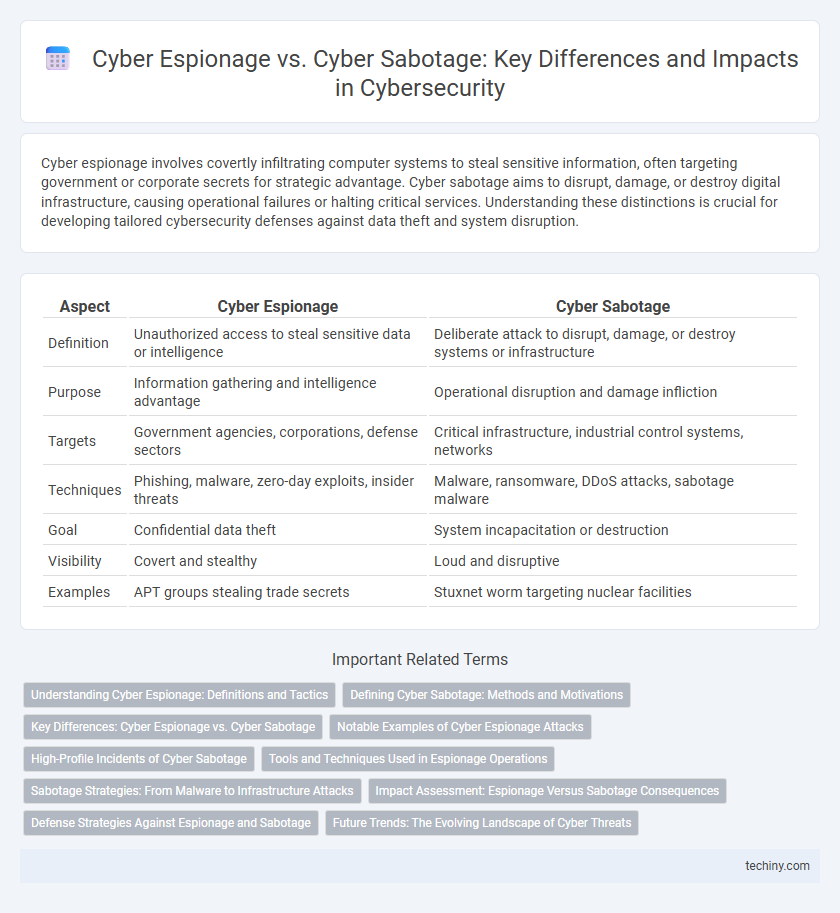
| Aspect | Cyber Espionage | Cyber Sabotage |
|---|---|---|
| Definition | Unauthorized access to steal sensitive data or intelligence | Deliberate attack to disrupt, damage, or destroy systems or infrastructure |
| Purpose | Information gathering and intelligence advantage | Operational disruption and damage infliction |
| Targets | Government agencies, corporations, defense sectors | Critical infrastructure, industrial control systems, networks |
| Techniques | Phishing, malware, zero-day exploits, insider threats | Malware, ransomware, DDoS attacks, sabotage malware |
| Goal | Confidential data theft | System incapacitation or destruction |
| Visibility | Covert and stealthy | Loud and disruptive |
| Examples | APT groups stealing trade secrets | Stuxnet worm targeting nuclear facilities |
Understanding Cyber Espionage: Definitions and Tactics
Cyber espionage involves the clandestine extraction of sensitive information from organizations or governments through sophisticated hacking techniques such as spear-phishing, malware deployment, and zero-day exploits. Key tactics include exploiting vulnerabilities in network infrastructures, employing advanced persistent threats (APTs), and manipulating insider access to maintain long-term infiltration. Understanding these methods is critical for developing robust cybersecurity defenses and mitigating risks associated with economic, political, and military intelligence theft.
Defining Cyber Sabotage: Methods and Motivations
Cyber sabotage involves deliberate attacks targeting information systems to disrupt, damage, or destroy digital infrastructure, often using methods such as malware injection, Distributed Denial of Service (DDoS) attacks, and ransomware deployment. Motivations behind cyber sabotage typically include political agendas, competitive advantage, and ideological objectives aimed at incapacitating critical infrastructure or undermining organizational operations. Unlike cyber espionage, which seeks covert data extraction, cyber sabotage prioritizes operational disruption and physical or digital asset destruction.
Key Differences: Cyber Espionage vs. Cyber Sabotage
Cyber espionage involves covertly gathering sensitive information from governments or organizations to gain strategic advantages, while cyber sabotage aims to disrupt, damage, or destroy critical systems and infrastructure. Espionage targets data theft and intelligence collection, whereas sabotage focuses on operational interference and causing physical or digital harm. Key differences lie in their objectives: espionage prioritizes secrecy and information acquisition, whereas sabotage emphasizes disruption and destruction.
Notable Examples of Cyber Espionage Attacks
Notable examples of cyber espionage attacks include the 2010 Operation Aurora, where Chinese hackers targeted Google and other major corporations to steal intellectual property and sensitive data. The 2014 Sony Pictures breach, attributed to North Korean hackers, demonstrated the use of cyber espionage to access confidential communications and corporate secrets. Another significant case is the 2015 Office of Personnel Management (OPM) hack, which exposed personal information of over 21 million U.S. government employees, showcasing the extensive reach of cyber espionage in compromising national security.
High-Profile Incidents of Cyber Sabotage
High-profile incidents of cyber sabotage include the 2010 Stuxnet attack, which targeted Iran's nuclear facilities and disrupted centrifuge operations, demonstrating sophisticated malware designed to cause physical damage. The 2017 NotPetya malware outbreak caused widespread disruption to Ukraine's infrastructure, affecting major corporations and costing billions in damages worldwide. These events highlight the rise of state-sponsored cyber sabotage aimed at critical infrastructure to achieve strategic geopolitical objectives.
Tools and Techniques Used in Espionage Operations
Cyber espionage employs advanced malware, phishing schemes, and zero-day exploits to infiltrate target networks and extract sensitive data stealthily. Attackers use spear-phishing emails, remote access Trojans (RATs), and keyloggers for persistent surveillance and information gathering. Techniques such as encrypted communication channels and obfuscation methods help evade detection during prolonged espionage campaigns.
Sabotage Strategies: From Malware to Infrastructure Attacks
Cyber sabotage strategies encompass a wide range of tactics from deploying sophisticated malware like worms and trojans to launching direct assaults on critical infrastructure components such as power grids, communication networks, and industrial control systems. Attackers exploit vulnerabilities in software, hardware, and human factors to disrupt operations, cause physical damage, or create widespread outages, often targeting SCADA systems and trusted supply chains to maximize impact. Understanding the evolving threat landscape of cyber sabotage is crucial for implementing robust defensive measures, including real-time monitoring, threat intelligence integration, and system redundancy.
Impact Assessment: Espionage Versus Sabotage Consequences
Cyber espionage primarily results in the covert theft of sensitive information, leading to long-term strategic disadvantages such as compromised intellectual property and weakened national security. In contrast, cyber sabotage causes immediate operational disruptions, damaging critical infrastructure, halting industrial processes, and inflicting financial losses. While espionage undermines competitive advantage over time, sabotage directly impacts system availability and safety, often necessitating urgent incident response and recovery efforts.
Defense Strategies Against Espionage and Sabotage
Effective defense strategies against cyber espionage and sabotage include deploying advanced threat detection systems that utilize artificial intelligence and machine learning to identify anomalous behaviors in real-time. Implementing comprehensive access controls and multi-factor authentication limits unauthorized access to sensitive data and critical infrastructure. Continuous employee training on cybersecurity best practices and incident response protocols strengthens organizational resilience against covert infiltration and disruptive cyber attacks.
Future Trends: The Evolving Landscape of Cyber Threats
Future trends in cyber threats indicate an escalation in the sophistication of cyber espionage, with state actors investing in advanced AI-driven surveillance tools to stealthily extract sensitive information. Cyber sabotage is also evolving, leveraging emerging technologies like quantum computing and autonomous malware to disrupt critical infrastructure faster and with greater precision. The convergence of these tactics poses a complex security challenge, necessitating enhanced AI-powered defense mechanisms and international cooperation to mitigate the growing risks.
Cyber Espionage vs Cyber Sabotage Infographic
 techiny.com
techiny.com