SQL Injection exploits vulnerabilities in database queries to manipulate or retrieve sensitive data, posing a significant threat to data integrity. Cross-Site Scripting (XSS) targets web applications by injecting malicious scripts into trusted websites, compromising user sessions and data. Both attacks require robust input validation and secure coding practices to effectively prevent unauthorized access and protect sensitive information.
Table of Comparison
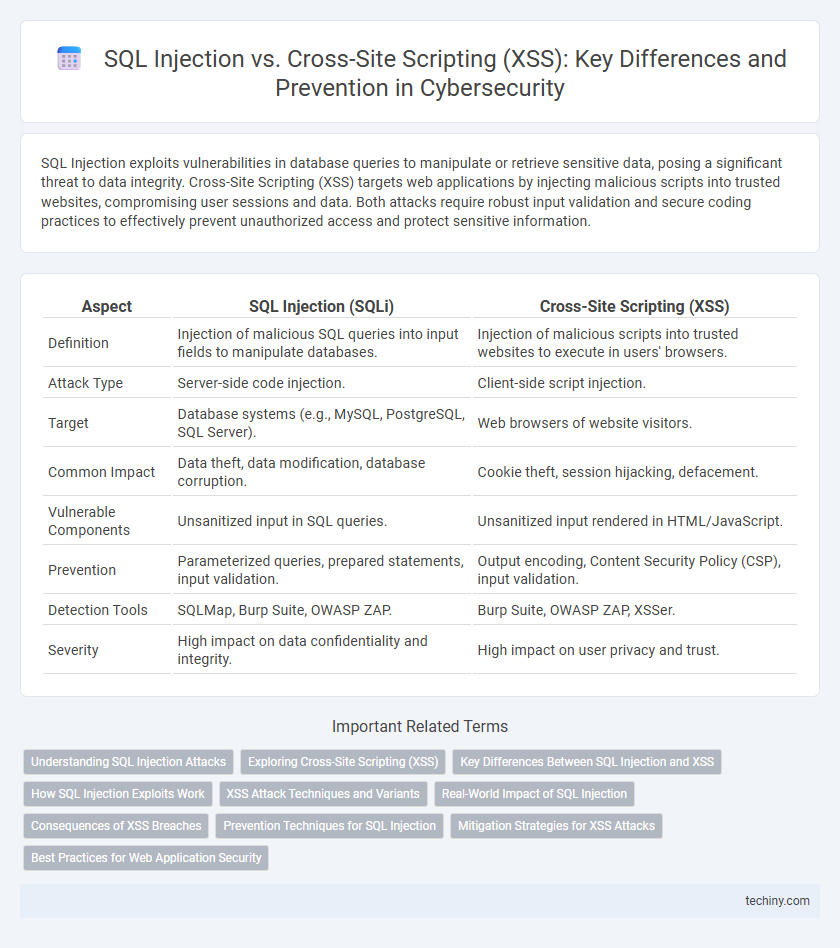
| Aspect | SQL Injection (SQLi) | Cross-Site Scripting (XSS) |
|---|---|---|
| Definition | Injection of malicious SQL queries into input fields to manipulate databases. | Injection of malicious scripts into trusted websites to execute in users' browsers. |
| Attack Type | Server-side code injection. | Client-side script injection. |
| Target | Database systems (e.g., MySQL, PostgreSQL, SQL Server). | Web browsers of website visitors. |
| Common Impact | Data theft, data modification, database corruption. | Cookie theft, session hijacking, defacement. |
| Vulnerable Components | Unsanitized input in SQL queries. | Unsanitized input rendered in HTML/JavaScript. |
| Prevention | Parameterized queries, prepared statements, input validation. | Output encoding, Content Security Policy (CSP), input validation. |
| Detection Tools | SQLMap, Burp Suite, OWASP ZAP. | Burp Suite, OWASP ZAP, XSSer. |
| Severity | High impact on data confidentiality and integrity. | High impact on user privacy and trust. |
Understanding SQL Injection Attacks
SQL Injection attacks exploit vulnerabilities in web applications by injecting malicious SQL queries into input fields, allowing attackers to manipulate databases and access sensitive information. These attacks often result in unauthorized data retrieval, modification, or deletion, posing significant risks to data integrity and confidentiality. Proper input validation, parameterized queries, and prepared statements are essential defenses against SQL Injection threats.
Exploring Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a common web security vulnerability that allows attackers to inject malicious scripts into trusted websites, targeting users' browsers to steal sensitive data such as cookies, session tokens, or manipulate webpage content. Unlike SQL Injection, which exploits backend databases by injecting malicious SQL queries, XSS exploits the client side by injecting executable scripts into web pages viewed by other users. Effective mitigation strategies for XSS include input validation, output encoding, and implementing Content Security Policy (CSP) to prevent unauthorized script execution.
Key Differences Between SQL Injection and XSS
SQL Injection targets database vulnerabilities by injecting malicious SQL queries to manipulate or access sensitive data, whereas Cross-Site Scripting (XSS) exploits web application vulnerabilities to execute malicious scripts in users' browsers, compromising client-side security. SQL Injection impacts server-side databases directly, often resulting in data breaches or loss, while XSS primarily affects user experience and session integrity through script injection. Understanding these distinct attack vectors helps implement targeted defenses such as parameterized queries for SQL Injection and input validation or Content Security Policy (CSP) for XSS prevention.
How SQL Injection Exploits Work
SQL Injection exploits target vulnerabilities in web application input fields by injecting malicious SQL code to manipulate databases, enabling attackers to retrieve, alter, or delete sensitive data. These attacks exploit improperly sanitized user inputs, allowing unauthorized access to backend databases through crafted queries. Effective prevention hinges on using parameterized queries, input validation, and robust error handling to block malicious code execution.
XSS Attack Techniques and Variants
Cross-Site Scripting (XSS) attacks exploit vulnerabilities by injecting malicious scripts into trusted websites, targeting client-side scripts to hijack user sessions, steal cookies, or deface web content. Common XSS variants include Stored XSS, where payloads are permanently stored on the target server; Reflected XSS, which involves immediate reflection of malicious input in server responses; and DOM-based XSS, exploiting client-side scripts by manipulating the Document Object Model. Advanced techniques involve bypassing input validation through encoding, obfuscation, or leveraging vulnerabilities in modern web frameworks and Content Security Policies (CSP).
Real-World Impact of SQL Injection
SQL Injection attacks exploit vulnerabilities in web applications by inserting malicious SQL code, leading to unauthorized access, data breaches, and potential manipulation of sensitive databases. Real-world incidents, such as the 2019 Capital One breach, demonstrate how SQL Injection can expose millions of customer records, causing severe financial and reputational damage. Unlike Cross-Site Scripting (XSS), which targets users by injecting malicious scripts into web pages, SQL Injection directly compromises the backend database, resulting in deeper data control and system disruption.
Consequences of XSS Breaches
Cross-Site Scripting (XSS) breaches often lead to session hijacking, enabling attackers to impersonate legitimate users and access sensitive information. Victims may suffer from identity theft, credential theft, and unauthorized transactions due to malicious scripts executing within their browsers. Unlike SQL Injection, which targets databases, XSS exploits vulnerabilities in web applications to compromise user trust and data integrity.
Prevention Techniques for SQL Injection
Implementing prepared statements and parameterized queries is crucial for preventing SQL Injection attacks, as these techniques ensure user inputs are treated as data rather than executable code. Employing robust input validation and sanitization further reduces the risk by filtering out malicious inputs before they reach the database. Regular use of web application firewalls (WAFs) and keeping database management systems updated also fortifies defenses against SQL Injection vulnerabilities.
Mitigation Strategies for XSS Attacks
Effective mitigation strategies for Cross-Site Scripting (XSS) attacks include input validation, output encoding, and the implementation of Content Security Policy (CSP). Input validation ensures that malicious scripts are sanitized before processing, while output encoding prevents the execution of injected scripts in web browsers. Enforcing CSP restricts the sources from which web content can be loaded, significantly reducing the risk of XSS exploitation.
Best Practices for Web Application Security
SQL Injection and Cross-Site Scripting (XSS) pose significant threats to web application security by exploiting input validation flaws. Implementing parameterized queries, rigorous input sanitization, and Content Security Policy (CSP) effectively mitigate these vulnerabilities. Regular security audits and employing frameworks with built-in protections ensure robust defense against injection and scripting attacks.
SQL Injection vs Cross-Site Scripting (XSS) Infographic
 techiny.com
techiny.com