Watering hole attacks target specific groups by compromising websites they frequently visit to infect users with malware, often remaining undetected for long periods. Drive-by downloads exploit vulnerabilities in a user's browser or plugins to automatically deliver malicious software without any user interaction. Both methods pose significant cybersecurity threats by leveraging trusted sites or user environments to execute stealthy and damaging exploits.
Table of Comparison
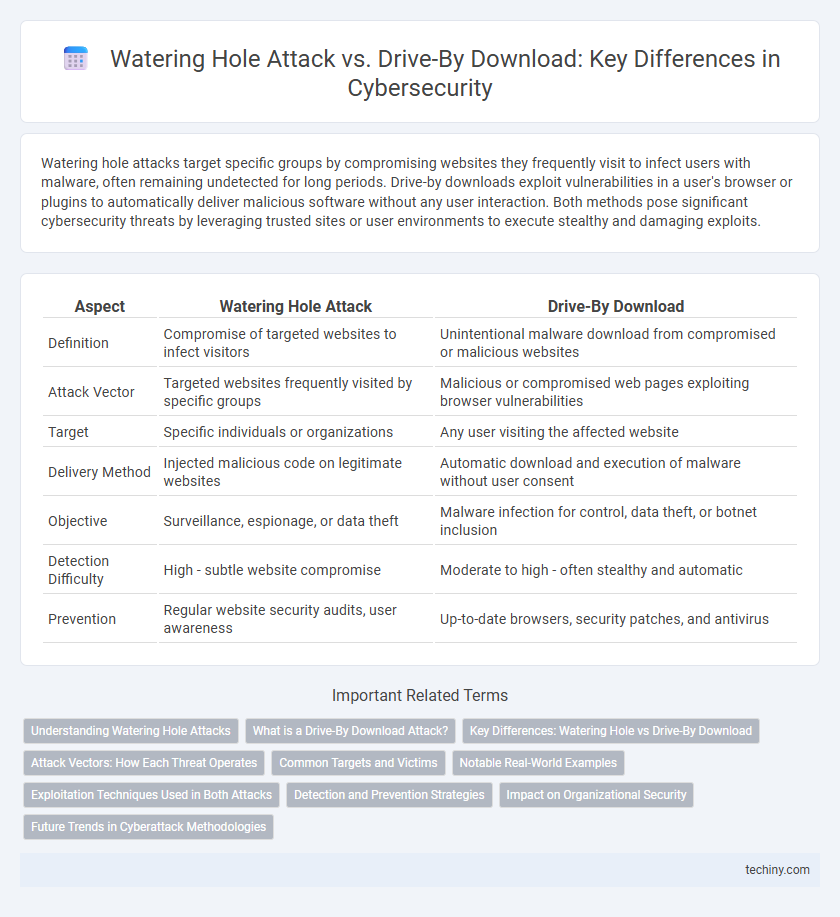
| Aspect | Watering Hole Attack | Drive-By Download |
|---|---|---|
| Definition | Compromise of targeted websites to infect visitors | Unintentional malware download from compromised or malicious websites |
| Attack Vector | Targeted websites frequently visited by specific groups | Malicious or compromised web pages exploiting browser vulnerabilities |
| Target | Specific individuals or organizations | Any user visiting the affected website |
| Delivery Method | Injected malicious code on legitimate websites | Automatic download and execution of malware without user consent |
| Objective | Surveillance, espionage, or data theft | Malware infection for control, data theft, or botnet inclusion |
| Detection Difficulty | High - subtle website compromise | Moderate to high - often stealthy and automatic |
| Prevention | Regular website security audits, user awareness | Up-to-date browsers, security patches, and antivirus |
Understanding Watering Hole Attacks
Watering hole attacks exploit trusted websites frequented by targeted users, implanting malicious code to compromise victims unaware of the threat. Attackers strategically choose these sites based on reconnaissance to maximize the infection rate within specific organizations or industries. Unlike drive-by downloads, which deliver malware through deceptive pop-ups or ads, watering hole attacks rely on infiltrating legitimate sites to silently breach security defenses.
What is a Drive-By Download Attack?
A Drive-By Download Attack occurs when a user unknowingly downloads malicious software simply by visiting a compromised or malicious website, without any explicit interaction. This type of attack exploits vulnerabilities in web browsers, plugins, or software to automatically install malware, which can lead to data theft, system control, or espionage. Unlike Watering Hole attacks that target specific groups by compromising frequently visited sites, Drive-By Downloads indiscriminately infect a wide range of visitors through web-based vulnerabilities.
Key Differences: Watering Hole vs Drive-By Download
Watering Hole attacks target specific groups by compromising websites frequented by intended victims, whereas Drive-By Downloads exploit vulnerabilities on any visited site to silently install malware on the user's device. Watering Hole attacks rely on strategic selection and manipulation of trusted websites, while Drive-By Downloads use automated exploitation kits triggered through malicious scripts embedded in commonly accessed web pages. The distinct attack vectors underscore the importance of tailored defense strategies focusing on user behavior analysis and real-time vulnerability patching.
Attack Vectors: How Each Threat Operates
Watering Hole attacks compromise frequently visited websites by targeted groups, infecting them with malware to exploit visitors' vulnerabilities. Drive-By Downloads exploit security flaws in web browsers or plugins to automatically download malicious software without user consent when visiting contaminated sites. Both attack vectors leverage trust in legitimate sites but differ by the method of delivering malware: targeted site compromise versus automatic browser-based infection.
Common Targets and Victims
Watering Hole attacks and Drive-By Downloads both primarily target organizations within specific industries such as finance, healthcare, and government sectors, exploiting trusted websites frequented by employees. Victims typically include employees and individuals who visit compromised sites, unknowingly downloading malware or exposing sensitive information. Both attack methods leverage social engineering and technical vulnerabilities to breach corporate networks and steal data from high-value targets.
Notable Real-World Examples
Notable real-world examples of Watering Hole attacks include the 2013 strike on the Council on Foreign Relations website, where attackers compromised a popular site to target affiliated users with malware. Drive-By Download incidents prominently feature the 2017 Angler Exploit Kit, which silently delivered ransomware by exploiting vulnerabilities in visitors' browsers without user interaction. Both attack types exploit trusted web resources but differ in execution, with Watering Hole focusing on compromising specific sites frequented by targets and Drive-By Downloads relying on automated exploitation of browser flaws.
Exploitation Techniques Used in Both Attacks
Watering hole attacks exploit vulnerabilities in frequently visited websites by compromising legitimate web servers to deliver malware to targeted users. Drive-by downloads leverage malicious or compromised web pages that automatically execute harmfully crafted exploit code without user interaction. Both attack types harness browser and plugin vulnerabilities, but watering hole attacks focus on strategic site infiltration while drive-by downloads rely on stealthy, automated exploitation during routine browsing.
Detection and Prevention Strategies
Watering Hole Attacks exploit trusted websites to infect targeted users, requiring continuous monitoring of web traffic and user behavior analytics for effective detection. Drive-By Downloads rely on unpatched software vulnerabilities to automatically install malware, making timely software updates and robust endpoint protection critical prevention measures. Employing multi-layered security solutions, including web filtering, threat intelligence, and real-time anomaly detection, enhances defense against both attack vectors.
Impact on Organizational Security
Watering hole attacks compromise trusted websites frequented by employees to deliver malware, leading to targeted breaches and long-term infiltration of organizational networks. Drive-by downloads exploit vulnerabilities during routine web browsing, causing the automatic installation of malicious software without user consent, resulting in rapid system compromise and data exfiltration. Both attack vectors disrupt organizational security, but watering hole attacks enable strategic access, while drive-by downloads create widespread immediate threats.
Future Trends in Cyberattack Methodologies
Watering Hole Attacks will increasingly exploit AI-driven profiling to identify high-value targets, adapting compromised sites with personalized malicious content. Drive-By Downloads are expected to leverage advanced evasion techniques, including polymorphic malware and encrypted payloads, to bypass traditional detection mechanisms. Both attack vectors will integrate with deepfake technology, enhancing social engineering effectiveness and complicating threat attribution in future cybersecurity landscapes.
Watering Hole Attack vs Drive-By Download Infographic
 techiny.com
techiny.com