MAC filtering limits network access by allowing only devices with specific MAC addresses to connect, providing a basic layer of security but susceptible to MAC spoofing. Network Access Control (NAC) offers a more robust solution by enforcing security policies on devices before granting access, including checking device compliance and user authentication. While MAC filtering is simpler to implement, NAC delivers comprehensive protection against unauthorized access and network threats.
Table of Comparison
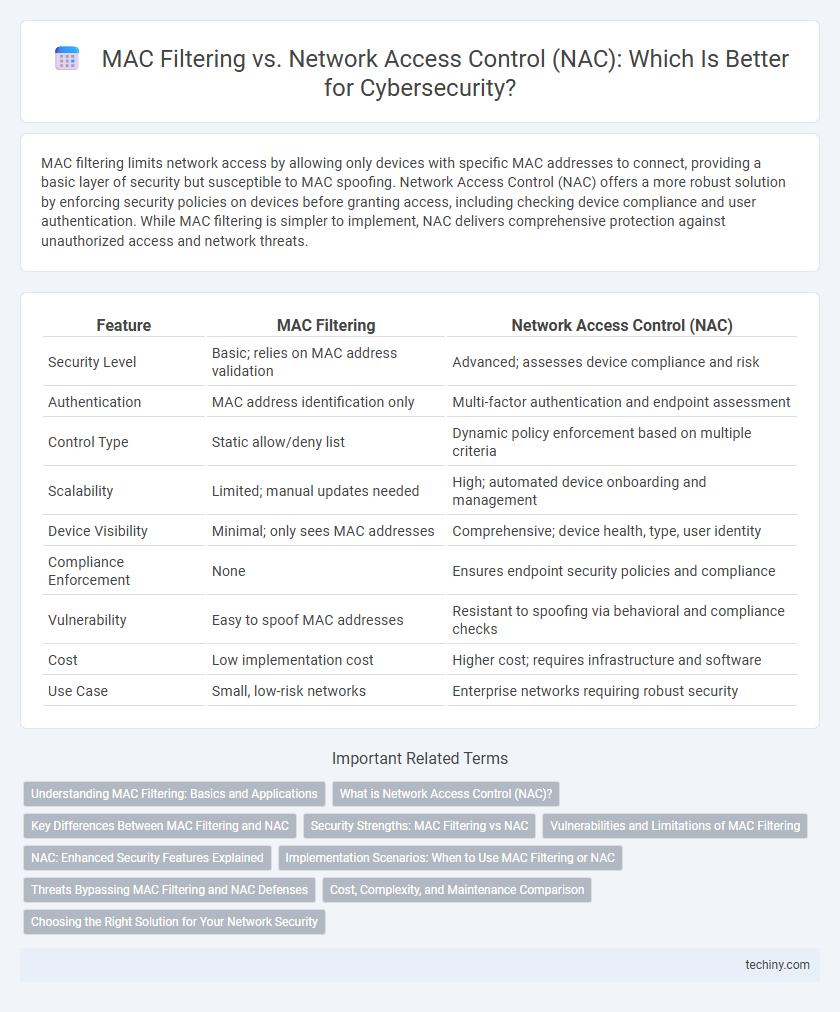
| Feature | MAC Filtering | Network Access Control (NAC) |
|---|---|---|
| Security Level | Basic; relies on MAC address validation | Advanced; assesses device compliance and risk |
| Authentication | MAC address identification only | Multi-factor authentication and endpoint assessment |
| Control Type | Static allow/deny list | Dynamic policy enforcement based on multiple criteria |
| Scalability | Limited; manual updates needed | High; automated device onboarding and management |
| Device Visibility | Minimal; only sees MAC addresses | Comprehensive; device health, type, user identity |
| Compliance Enforcement | None | Ensures endpoint security policies and compliance |
| Vulnerability | Easy to spoof MAC addresses | Resistant to spoofing via behavioral and compliance checks |
| Cost | Low implementation cost | Higher cost; requires infrastructure and software |
| Use Case | Small, low-risk networks | Enterprise networks requiring robust security |
Understanding MAC Filtering: Basics and Applications
MAC filtering is a network security access control method that permits or denies devices based on their unique Media Access Control (MAC) addresses, providing a basic layer of device authentication. It is commonly used in small networks to restrict access to authorized devices but has limitations due to MAC address spoofing vulnerabilities. While effective for simple scenarios, MAC filtering lacks the comprehensive security features of Network Access Control (NAC) systems, which offer dynamic policy enforcement and detailed device posture assessments.
What is Network Access Control (NAC)?
Network Access Control (NAC) is a comprehensive cybersecurity solution that enforces security policies on devices attempting to access a network by verifying device compliance, user authentication, and endpoint security posture. Unlike MAC filtering, which solely restricts access based on device MAC addresses, NAC integrates multiple factors such as device health, user identity, and role-based permissions to provide dynamic and granular network access control. NAC solutions enhance network security by continuously monitoring connected devices and automatically isolating or remediating non-compliant endpoints to prevent unauthorized access and potential threats.
Key Differences Between MAC Filtering and NAC
MAC filtering controls network access by allowing or blocking devices based on their physical MAC addresses, offering a simple layer of security primarily effective for small networks. Network Access Control (NAC) provides comprehensive security by evaluating device compliance, user authentication, and enforcing policies before granting network access, suitable for dynamic and larger enterprise environments. Unlike MAC filtering, NAC supports extensive endpoint checks, integration with identity services, and can adapt to various security postures for enhanced network protection.
Security Strengths: MAC Filtering vs NAC
MAC filtering offers basic network access control by allowing only devices with specific MAC addresses to connect, but it is vulnerable to spoofing attacks and lacks comprehensive security features. Network Access Control (NAC) provides robust security by enforcing policies that authenticate, authorize, and assess the health of devices before granting network access, effectively reducing risks from unauthorized or compromised devices. NAC's dynamic and multi-layered approach significantly strengthens network defense compared to the static and easily bypassed nature of MAC filtering.
Vulnerabilities and Limitations of MAC Filtering
MAC filtering in cybersecurity presents significant vulnerabilities, primarily due to its reliance on easily spoofable MAC addresses, which attackers can mimic to gain unauthorized network access. This method lacks robust authentication mechanisms, making it ineffective against sophisticated threats and insider attacks. Network Access Control (NAC) offers superior security by enforcing dynamic policies and comprehensive device authentication, addressing the critical limitations inherent in MAC filtering.
NAC: Enhanced Security Features Explained
Network Access Control (NAC) offers superior security compared to MAC filtering by enforcing comprehensive policies based on device compliance, user authentication, and endpoint health status, rather than relying solely on MAC addresses, which are easily spoofed. NAC integrates with threat intelligence and endpoint detection tools to dynamically assess and restrict network access, providing granular control over devices and users in real-time. Its ability to enforce multi-factor authentication and continuous monitoring significantly reduces unauthorized access risks and enhances overall network security posture.
Implementation Scenarios: When to Use MAC Filtering or NAC
MAC filtering is suitable for small networks or environments requiring basic access control by allowing or blocking devices based on their MAC addresses. Network Access Control (NAC) excels in complex enterprise settings, offering comprehensive security through device compliance checks, user authentication, and dynamic policy enforcement. Organizations managing diverse, large-scale networks benefit from NAC's advanced capabilities, while smaller businesses with limited resources may find MAC filtering sufficient for simple device restriction.
Threats Bypassing MAC Filtering and NAC Defenses
MAC filtering primarily blocks unauthorized devices based on hardware addresses, but attackers can spoof MAC addresses to bypass these controls, rendering it ineffective against sophisticated intrusions. Network Access Control (NAC) enforces device compliance and user authentication, yet advanced threats exploiting zero-day vulnerabilities or insider credentials can circumvent NAC policies. Effective cybersecurity requires integrating multi-layered defenses beyond MAC filtering and NAC to detect and respond to evolving attack techniques.
Cost, Complexity, and Maintenance Comparison
MAC filtering offers a lower-cost solution for basic network access control, requiring minimal setup but providing limited security due to easy MAC address spoofing. Network Access Control (NAC) systems involve higher initial costs and complexity, integrating with directory services and endpoint compliance checks for granular policy enforcement. Maintenance demands for NAC are greater, requiring regular updates and monitoring to adapt to evolving threats, whereas MAC filtering maintenance remains straightforward but less effective against sophisticated breaches.
Choosing the Right Solution for Your Network Security
MAC filtering offers basic control by allowing or denying devices based on their MAC addresses, suitable for small networks with minimal security needs. Network Access Control (NAC) provides a comprehensive solution by evaluating device compliance, user identity, and endpoint security before granting access, making it ideal for enterprise environments requiring granular control and real-time threat mitigation. Selecting the right solution depends on the network size, security requirements, and the need for dynamic policy enforcement to protect sensitive data and prevent unauthorized access.
MAC Filtering vs NAC Infographic
 techiny.com
techiny.com