A firewall serves as a security barrier that monitors and controls incoming and outgoing network traffic based on predetermined security rules, protecting internal networks from unauthorized access and cyber threats. A proxy server acts as an intermediary between a user's device and the internet, filtering requests, enhancing privacy, and caching content to improve performance. While firewalls primarily control access and block malicious traffic, proxy servers focus on privacy, content filtering, and anonymity during web requests.
Table of Comparison
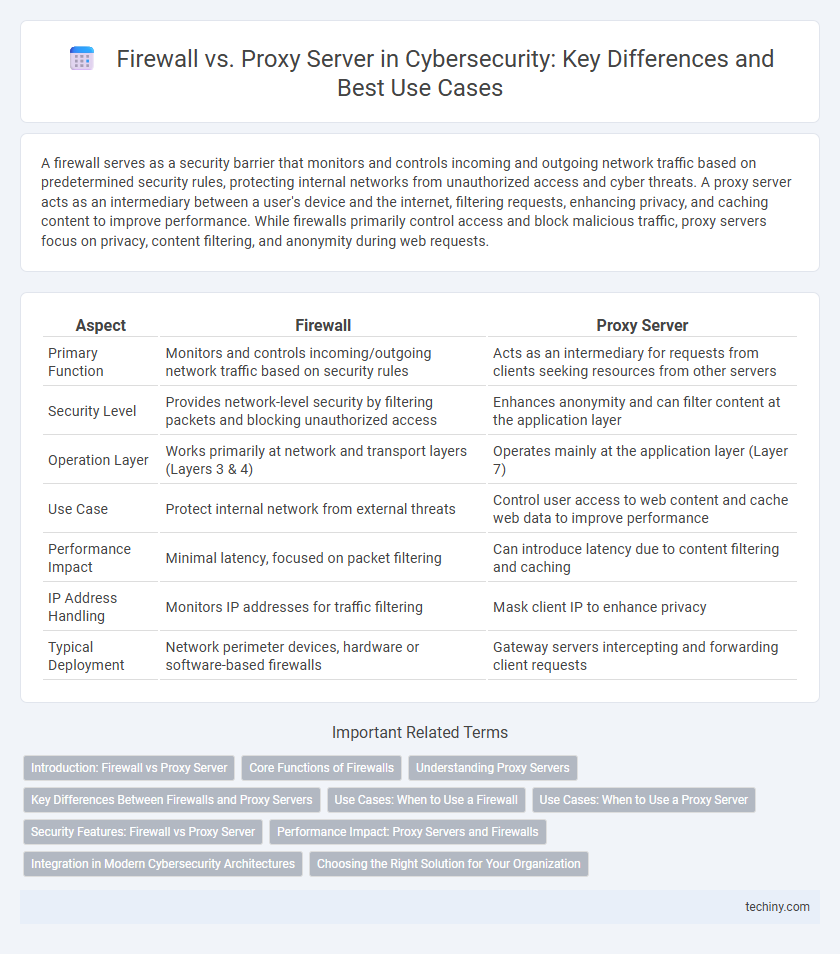
| Aspect | Firewall | Proxy Server |
|---|---|---|
| Primary Function | Monitors and controls incoming/outgoing network traffic based on security rules | Acts as an intermediary for requests from clients seeking resources from other servers |
| Security Level | Provides network-level security by filtering packets and blocking unauthorized access | Enhances anonymity and can filter content at the application layer |
| Operation Layer | Works primarily at network and transport layers (Layers 3 & 4) | Operates mainly at the application layer (Layer 7) |
| Use Case | Protect internal network from external threats | Control user access to web content and cache web data to improve performance |
| Performance Impact | Minimal latency, focused on packet filtering | Can introduce latency due to content filtering and caching |
| IP Address Handling | Monitors IP addresses for traffic filtering | Mask client IP to enhance privacy |
| Typical Deployment | Network perimeter devices, hardware or software-based firewalls | Gateway servers intercepting and forwarding client requests |
Introduction: Firewall vs Proxy Server
Firewalls and proxy servers serve distinct roles in network security by controlling access and managing data traffic. Firewalls primarily filter incoming and outgoing packets based on predefined security rules to block unauthorized access, while proxy servers act as intermediaries that mask user IP addresses and cache content to enhance security and performance. Understanding the functional differences between firewall technology and proxy services is essential for designing comprehensive cybersecurity strategies.
Core Functions of Firewalls
Firewalls serve as critical security barriers that monitor and control incoming and outgoing network traffic based on predetermined security rules. Their core functions include packet filtering, stateful inspection, and proxy service to prevent unauthorized access and cyber threats. Firewalls also enforce network segmentation and provide intrusion detection capabilities to enhance overall cybersecurity defenses.
Understanding Proxy Servers
Proxy servers act as intermediaries between users and the internet, masking IP addresses to enhance online privacy and security. They filter web traffic by intercepting requests and forwarding them on behalf of users, enabling content control and malware protection. Unlike firewalls, proxy servers manage data flow at the application level, providing granular control over web access and caching to improve performance.
Key Differences Between Firewalls and Proxy Servers
Firewalls primarily function as security barriers that monitor and control incoming and outgoing network traffic based on predetermined security rules, protecting networks from unauthorized access and threats. Proxy servers act as intermediaries that handle user requests for resources, providing privacy, caching, and content filtering by masking IP addresses and managing web traffic. Firewalls operate at the network and transport layers to enforce security policies, while proxy servers work at the application layer to facilitate specific web-based services and anonymity.
Use Cases: When to Use a Firewall
A firewall is essential for protecting internal networks from unauthorized access and cyber threats by filtering incoming and outgoing traffic based on predetermined security rules. It is ideal for securing corporate environments, blocking malicious IP addresses, and preventing data breaches in real-time. Use a firewall when establishing perimeter defense, enforcing network segmentation, or controlling access to sensitive resources is critical for cybersecurity.
Use Cases: When to Use a Proxy Server
Proxy servers are ideal for enhancing user privacy and controlling web access in corporate environments by filtering and caching requests to improve network efficiency. They are commonly used to bypass geo-restrictions and monitor employee internet usage without directly exposing internal IP addresses. In cybersecurity, proxy servers help prevent direct attacks on a client device by acting as an intermediary between users and the internet.
Security Features: Firewall vs Proxy Server
Firewalls provide robust network security by controlling incoming and outgoing traffic based on predefined rules, effectively blocking unauthorized access and preventing cyber threats such as malware and intrusion attempts. Proxy servers enhance privacy and security by masking user IP addresses, filtering web content, and monitoring outbound requests to restrict access to malicious or inappropriate sites. While firewalls operate at the network and transport layers to guard against external attacks, proxy servers function at the application layer, offering detailed traffic inspection and user anonymity.
Performance Impact: Proxy Servers and Firewalls
Firewalls primarily filter network traffic based on predefined security rules, resulting in minimal latency and efficient throughput for most standard operations. Proxy servers, by intercepting and inspecting client requests to enforce content filtering, caching, or anonymization, introduce higher processing overhead that can impact response times. Performance impact varies depending on the complexity of filtering policies and network load, with firewalls generally offering faster packet-level inspection compared to the higher application-layer processing demands of proxy servers.
Integration in Modern Cybersecurity Architectures
Firewall and proxy servers serve complementary roles in modern cybersecurity architectures, enhancing network security through integrated deployment. Firewalls filter incoming and outgoing traffic based on predefined security rules, preventing unauthorized access, while proxy servers act as intermediaries that anonymize user requests and cache content to improve performance and security. Combining these technologies within Unified Threat Management (UTM) systems and next-generation firewalls (NGFW) offers organizations comprehensive protection by enforcing granular access controls and inspecting encrypted traffic.
Choosing the Right Solution for Your Organization
Selecting the right cybersecurity solution between a firewall and a proxy server depends on your organization's specific needs for network security and traffic management. Firewalls provide robust perimeter defense by filtering incoming and outgoing traffic based on predetermined security rules, effectively blocking unauthorized access and malware threats. Proxy servers enhance privacy and control by intercepting user requests, enabling content filtering, logging, and anonymity, making them ideal for managing internal user behavior and external web access.
Firewall vs Proxy Server Infographic
 techiny.com
techiny.com