Balancing privacy and security remains a critical challenge in cybersecurity, where protecting sensitive personal data often conflicts with implementing stringent security measures. Encryption techniques and access controls can safeguard user privacy without compromising system security. Organizations must adopt transparent policies that respect individual privacy rights while maintaining robust defenses against cyber threats.
Table of Comparison
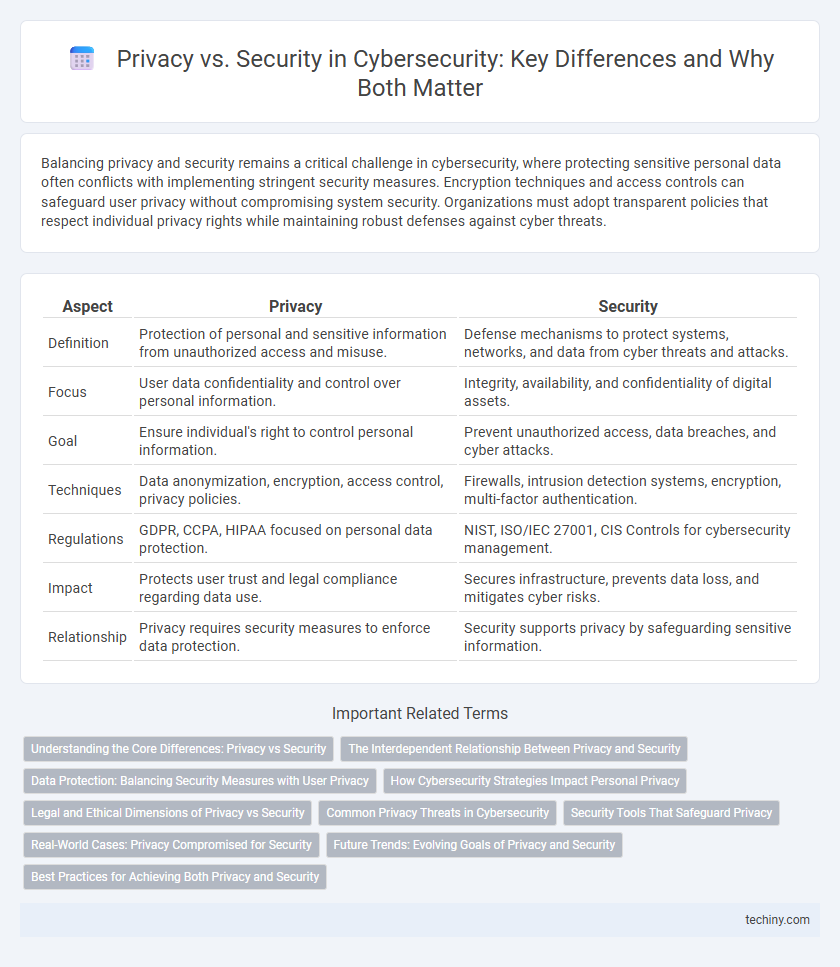
| Aspect | Privacy | Security |
|---|---|---|
| Definition | Protection of personal and sensitive information from unauthorized access and misuse. | Defense mechanisms to protect systems, networks, and data from cyber threats and attacks. |
| Focus | User data confidentiality and control over personal information. | Integrity, availability, and confidentiality of digital assets. |
| Goal | Ensure individual's right to control personal information. | Prevent unauthorized access, data breaches, and cyber attacks. |
| Techniques | Data anonymization, encryption, access control, privacy policies. | Firewalls, intrusion detection systems, encryption, multi-factor authentication. |
| Regulations | GDPR, CCPA, HIPAA focused on personal data protection. | NIST, ISO/IEC 27001, CIS Controls for cybersecurity management. |
| Impact | Protects user trust and legal compliance regarding data use. | Secures infrastructure, prevents data loss, and mitigates cyber risks. |
| Relationship | Privacy requires security measures to enforce data protection. | Security supports privacy by safeguarding sensitive information. |
Understanding the Core Differences: Privacy vs Security
Privacy centers on protecting personal information and controlling data access, while security involves implementing measures to safeguard systems from unauthorized breaches and threats. Understanding the core differences highlights that privacy is about individual rights and data confidentiality, whereas security focuses on technical defenses and risk management. Effective cybersecurity strategies integrate both concepts to ensure comprehensive protection of sensitive information and digital assets.
The Interdependent Relationship Between Privacy and Security
Privacy and security are fundamentally interdependent, as strong cybersecurity measures protect sensitive personal data from breaches that compromise privacy. Effective security protocols ensure data integrity, confidentiality, and access control, which are essential for maintaining user privacy in digital environments. Organizations must integrate robust encryption, multi-factor authentication, and continuous monitoring to safeguard both privacy and security simultaneously.
Data Protection: Balancing Security Measures with User Privacy
Data protection in cybersecurity requires a delicate balance between implementing robust security measures and preserving user privacy, ensuring sensitive information is shielded from breaches without overstepping personal data boundaries. Encryption, access controls, and anonymization techniques serve as critical tools to protect data integrity while respecting privacy rights. Organizations must adhere to regulations such as GDPR and CCPA to maintain transparency and accountability in data handling practices.
How Cybersecurity Strategies Impact Personal Privacy
Cybersecurity strategies often require balancing robust protection measures with the preservation of personal privacy, as aggressive data monitoring can lead to intrusive surveillance. Encryption and anonymization techniques are critical for safeguarding user data while enabling effective threat detection without compromising confidentiality. Implementing privacy-by-design principles ensures cybersecurity solutions protect sensitive information while minimizing risks of unauthorized access.
Legal and Ethical Dimensions of Privacy vs Security
Balancing privacy and security involves navigating complex legal frameworks such as GDPR and HIPAA, which mandate strict data protection while allowing security measures against cyber threats. Ethical considerations emphasize respecting individual autonomy and consent, even as organizations implement surveillance and monitoring to prevent breaches. Legal precedents and ethical guidelines must align to ensure cybersecurity practices do not infringe on fundamental privacy rights.
Common Privacy Threats in Cybersecurity
Common privacy threats in cybersecurity include data breaches, identity theft, and unauthorized surveillance, which compromise sensitive personal information. Phishing attacks and malware infiltration often exploit weak security protocols to steal private data. Organizations must implement robust encryption, multi-factor authentication, and continuous monitoring to mitigate these pervasive privacy risks.
Security Tools That Safeguard Privacy
Security tools such as encryption software, VPNs, and multi-factor authentication directly safeguard privacy by protecting sensitive data from unauthorized access and cyber threats. Advanced firewalls and intrusion detection systems create barriers that prevent data breaches and preserve user confidentiality. These tools ensure the integrity and confidentiality of personal information while maintaining compliance with privacy regulations like GDPR and CCPA.
Real-World Cases: Privacy Compromised for Security
Numerous real-world cybersecurity incidents highlight instances where privacy was compromised in favor of security, such as the NSA's mass surveillance programs revealed by Edward Snowden, which prioritized national security over individual privacy rights. In corporate environments, companies like Facebook have faced criticism for data collection practices that enhance security and targeted advertising at the expense of user privacy. These cases underscore the ongoing tension between implementing robust security measures and protecting personal privacy in a digital age.
Future Trends: Evolving Goals of Privacy and Security
Future trends in cybersecurity reveal a convergence between privacy and security as organizations adopt zero-trust architectures and advanced encryption methods to protect sensitive data. Emerging technologies like homomorphic encryption and decentralized identity frameworks enhance privacy while enabling robust threat detection and response. The evolving goals emphasize balancing user control over personal information with proactive defense mechanisms against increasingly sophisticated cyber threats.
Best Practices for Achieving Both Privacy and Security
Implementing strong encryption protocols and regular software updates protects both data privacy and system security by preventing unauthorized access and vulnerabilities. Employing multi-factor authentication enhances user verification processes while safeguarding personal information from cyber threats. Conducting continuous risk assessments ensures alignment with compliance standards and identifies gaps to balance privacy concerns with robust security measures.
Privacy vs Security Infographic
 techiny.com
techiny.com