Shodan and Censys are powerful cybersecurity search engines that index internet-connected devices and services for vulnerability assessment. Shodan excels at identifying exposed devices such as webcams, routers, and industrial control systems by scanning ports and banners, while Censys provides comprehensive data on certificates, hosts, and services with deep protocol-level inspection for analyzing network security posture. Both tools enhance threat intelligence but differ in scope and data presentation, making them complementary assets in vulnerability management and attack surface monitoring.
Table of Comparison
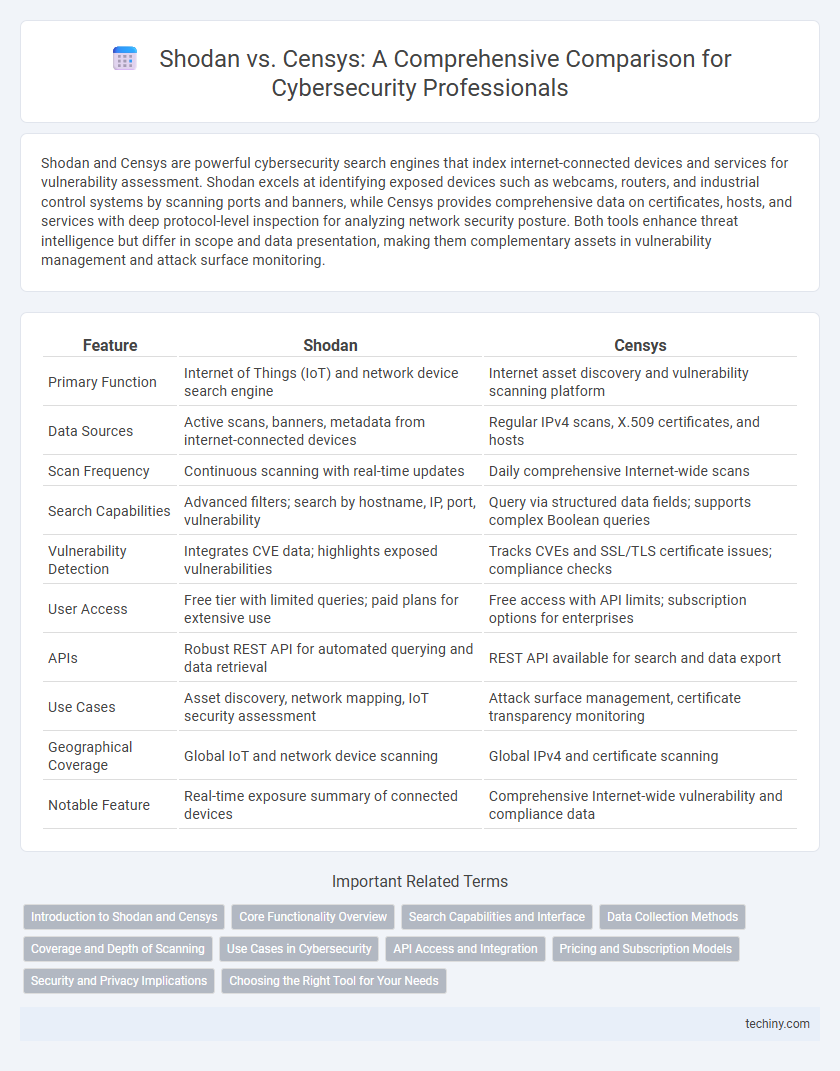
| Feature | Shodan | Censys |
|---|---|---|
| Primary Function | Internet of Things (IoT) and network device search engine | Internet asset discovery and vulnerability scanning platform |
| Data Sources | Active scans, banners, metadata from internet-connected devices | Regular IPv4 scans, X.509 certificates, and hosts |
| Scan Frequency | Continuous scanning with real-time updates | Daily comprehensive Internet-wide scans |
| Search Capabilities | Advanced filters; search by hostname, IP, port, vulnerability | Query via structured data fields; supports complex Boolean queries |
| Vulnerability Detection | Integrates CVE data; highlights exposed vulnerabilities | Tracks CVEs and SSL/TLS certificate issues; compliance checks |
| User Access | Free tier with limited queries; paid plans for extensive use | Free access with API limits; subscription options for enterprises |
| APIs | Robust REST API for automated querying and data retrieval | REST API available for search and data export |
| Use Cases | Asset discovery, network mapping, IoT security assessment | Attack surface management, certificate transparency monitoring |
| Geographical Coverage | Global IoT and network device scanning | Global IPv4 and certificate scanning |
| Notable Feature | Real-time exposure summary of connected devices | Comprehensive Internet-wide vulnerability and compliance data |
Introduction to Shodan and Censys
Shodan is a powerful search engine designed to scan and index internet-connected devices, providing detailed metadata on open ports, services, and vulnerabilities. Censys operates similarly, continuously mapping the global internet landscape to offer comprehensive data on hosts and certificates for security research and threat detection. Both platforms serve as critical tools for cybersecurity professionals to identify and assess exposed assets and potential attack surfaces.
Core Functionality Overview
Shodan specializes in scanning and indexing internet-connected devices by probing IP addresses and ports to identify exposed services and vulnerabilities. Censys provides a comprehensive search engine that aggregates data from internet-wide scans, SSL certificates, and DNS information to deliver detailed asset and exposure analysis. Both platforms enable security professionals to assess network exposure but differ in data sources and update frequency, with Shodan emphasizing real-time device enumeration and Censys focusing on historical and detailed protocol data.
Search Capabilities and Interface
Shodan and Censys provide robust search capabilities tailored for cybersecurity professionals, with Shodan focusing on scanning internet-connected devices and offering filters based on device type, IP, and vulnerabilities. Censys differentiates itself by providing detailed certificates and network data, enabling deeper asset discovery and continuous monitoring through a more data-driven and API-friendly interface. Shodan's user-friendly dashboard supports quick visual insights, while Censys emphasizes raw data access and customization, catering to advanced security researchers seeking granular control.
Data Collection Methods
Shodan collects data primarily through active scanning of internet-connected devices, probing ports and services to identify vulnerabilities in real-time. Censys combines active scanning with passive data collection from various internet sources, including certificates and SSL/TLS handshakes, to build a comprehensive digital footprint. Both platforms use unique data collection methods that enrich cybersecurity analysis, with Shodan focusing on device-level visibility and Censys emphasizing protocol and certificate metadata.
Coverage and Depth of Scanning
Shodan provides extensive global coverage by scanning the entire IPv4 address space regularly, focusing on identifying internet-connected devices and services with detailed banner information. Censys complements this with deeper scan data, offering comprehensive protocol analysis and continuous monitoring of host configurations, enabling precise vulnerability assessment. Together, they balance broad coverage and in-depth scanning to deliver robust cybersecurity intelligence.
Use Cases in Cybersecurity
Shodan excels in real-time asset discovery and vulnerability identification by scanning and indexing internet-connected devices, enabling cybersecurity teams to detect exposed systems and potential attack vectors quickly. Censys offers comprehensive internet-wide data with enhanced contextual metadata, supporting advanced threat intelligence, incident response, and compliance auditing through continuous monitoring of digital assets. Both platforms serve critical roles in cybersecurity by facilitating proactive risk management and improving visibility into the external attack surface.
API Access and Integration
Shodan and Censys offer robust API access for seamless integration into cybersecurity workflows, with Shodan providing a comprehensive API that includes data on connected devices, vulnerabilities, and real-time network monitoring. Censys API excels in detailed asset discovery and security posture assessment through its extensive internet-wide scanning data accessible via RESTful endpoints. Both platforms support automation and orchestration, enhancing threat intelligence and vulnerability management through flexible API integration in security tools and custom applications.
Pricing and Subscription Models
Shodan offers a tiered subscription model starting with a free plan that limits query volume and access to basic features, while paid plans range from $49 to $399 per month, providing enhanced API access and search capabilities. Censys provides a free tier with limited daily queries and indexed hosts, alongside Pro and Enterprise plans that unlock advanced search filters, unlimited queries, and commercial API usage, with pricing available upon request. Both platforms cater to cybersecurity professionals but differ in flexibility and pricing transparency, making Shodan more accessible for individual users and Censys preferable for enterprise-level threat intelligence needs.
Security and Privacy Implications
Shodan and Censys both scan the internet for connected devices, but Shodan's focus on exposed vulnerabilities can increase the risk of cyberattacks by making sensitive information more accessible to malicious actors. Censys provides comprehensive data on host security configurations, helping organizations identify and mitigate risks more proactively. The different data collection and reporting practices impact privacy, with Shodan often revealing device details that could lead to unauthorized access, while Censys emphasizes verified security assessments.
Choosing the Right Tool for Your Needs
Shodan excels in real-time internet device scanning and provides comprehensive data on exposed services, ideal for rapid vulnerability assessments and threat hunting. Censys offers deeper, historically indexed internet-wide scan data with advanced search capabilities, suitable for longitudinal research and detailed asset inventory management. Select Shodan for immediate, actionable intelligence and Censys for in-depth analysis and trend tracking in cybersecurity operations.
Shodan vs Censys Infographic
 techiny.com
techiny.com