Threat actors possess advanced skills and resources to execute sophisticated cyberattacks, often targeting specific organizations or infrastructures for financial gain or espionage. Script kiddies lack expertise and rely on pre-made tools and scripts to launch opportunistic, low-level attacks without deep knowledge of cybersecurity techniques. Understanding the difference between these attackers is crucial for developing effective defense strategies and prioritizing security investments.
Table of Comparison
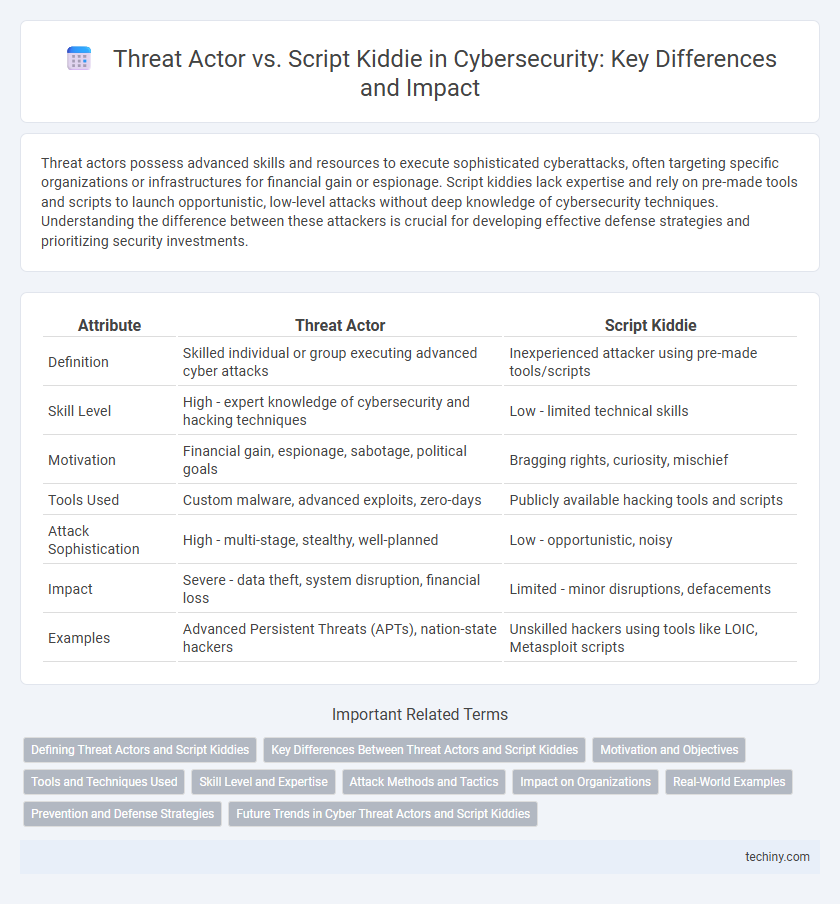
| Attribute | Threat Actor | Script Kiddie |
|---|---|---|
| Definition | Skilled individual or group executing advanced cyber attacks | Inexperienced attacker using pre-made tools/scripts |
| Skill Level | High - expert knowledge of cybersecurity and hacking techniques | Low - limited technical skills |
| Motivation | Financial gain, espionage, sabotage, political goals | Bragging rights, curiosity, mischief |
| Tools Used | Custom malware, advanced exploits, zero-days | Publicly available hacking tools and scripts |
| Attack Sophistication | High - multi-stage, stealthy, well-planned | Low - opportunistic, noisy |
| Impact | Severe - data theft, system disruption, financial loss | Limited - minor disruptions, defacements |
| Examples | Advanced Persistent Threats (APTs), nation-state hackers | Unskilled hackers using tools like LOIC, Metasploit scripts |
Defining Threat Actors and Script Kiddies
Threat actors in cybersecurity are individuals or groups with advanced skills and resources aiming to exploit vulnerabilities for espionage, financial gain, or disruptive purposes. Script kiddies are less skilled attackers who rely on pre-made hacking tools and scripts without deep understanding of the underlying mechanisms. Distinguishing between sophisticated threat actors and script kiddies is crucial for developing targeted defense strategies and prioritizing threat intelligence efforts.
Key Differences Between Threat Actors and Script Kiddies
Threat actors are skilled individuals or groups with advanced knowledge and resources who execute sophisticated cyberattacks for motives like espionage, financial gain, or disruption, while script kiddies lack deep technical expertise and rely on pre-made tools and scripts to launch opportunistic or random attacks. Threat actors often plan targeted campaigns using zero-day exploits and custom malware, whereas script kiddies typically exploit publicly known vulnerabilities without understanding the underlying mechanisms. The impact of threat actors is usually strategic and long-lasting, contrasting with the relatively low-sophistication and short-lived threats posed by script kiddies.
Motivation and Objectives
Threat actors typically possess advanced skills and clear objectives such as financial gain, espionage, or disrupting critical infrastructure, driven by ideological, political, or economic motivations. Script kiddies lack deep technical expertise and primarily seek notoriety or entertainment by exploiting existing tools and vulnerabilities without specific strategic goals. The disparity in motivation and objectives impacts the complexity and potential damage of their cyberattacks, with threat actors posing a more sophisticated and sustained risk compared to opportunistic script kiddies.
Tools and Techniques Used
Threat actors employ advanced tools such as custom malware, zero-day exploits, and sophisticated phishing frameworks to execute targeted attacks, often leveraging extensive knowledge of network vulnerabilities and cryptographic weaknesses. Script kiddies rely primarily on readily available automated scripts, pre-packaged hacking tools, and publicly shared exploits without deep understanding, typically conducting opportunistic or disruptive attacks. The disparity in tool sophistication directly impacts the complexity and scale of their cyber intrusions, with threat actors capable of stealthier and more persistent threats compared to the rudimentary tactics used by script kiddies.
Skill Level and Expertise
Threat actors possess advanced technical skills and deep expertise in cybersecurity, enabling them to develop sophisticated malware and execute complex attacks. Script kiddies have limited knowledge and rely heavily on pre-written code or tools created by others, demonstrating low skill levels and minimal understanding of underlying vulnerabilities. The stark contrast in proficiency defines the potential impact and threat severity posed by each group.
Attack Methods and Tactics
Threat actors employ sophisticated attack methods such as advanced persistent threats (APTs), zero-day exploits, and multi-stage intrusion techniques, often utilizing custom malware and social engineering to maintain stealth and persistence. Script kiddies rely on readily available tools and pre-written scripts to execute common attacks like denial-of-service (DoS), basic phishing, and automated vulnerability scanning, lacking deep technical expertise or strategic planning. The contrast in tactics reflects the advanced, targeted approach of threat actors versus the opportunistic, automated methods favored by script kiddies.
Impact on Organizations
Threat actors pose significant risks to organizations by executing sophisticated cyberattacks that compromise sensitive data, disrupt operations, and inflict financial losses. Script kiddies, while less skilled, can still cause considerable damage through the use of readily available hacking tools, exploiting known vulnerabilities. Organizations need robust cybersecurity defenses to mitigate threats from both highly skilled adversaries and opportunistic attackers wielding automated tools.
Real-World Examples
Threat actors like APT28 exemplify sophisticated cyber espionage by leveraging advanced malware to target government networks globally, while script kiddies typically execute pre-made scripts with limited technical skills, often causing indiscriminate website defacements or simple DDoS attacks. Notorious incidents such as the Sony Pictures hack by APT28 showcase strategic, state-sponsored operations, contrasting with the chaotic vandalism perpetrated by script kiddies during the 2011 LulzSec campaign. Real-world impacts illustrate the vast disparity in threat actor capabilities, highlighting the importance of tailored cybersecurity defenses against both advanced persistent threats and opportunistic script kiddie attacks.
Prevention and Defense Strategies
Threat actors employ sophisticated tactics such as advanced persistent threats (APTs), requiring organizations to implement multi-layered defense strategies including network segmentation, behavioral analytics, and threat intelligence integration. Script kiddies rely on pre-built tools and exploits, making basic cybersecurity hygiene like regular patching, robust firewalls, and user education effective preventive measures. Prioritizing continuous monitoring and incident response capabilities mitigates risks posed by both advanced threat actors and opportunistic script kiddies.
Future Trends in Cyber Threat Actors and Script Kiddies
Future trends in cyber threat actors indicate increasing sophistication driven by advancements in artificial intelligence and machine learning, enabling targeted attacks and enhanced evasion techniques. Script kiddies are expected to persist but will increasingly exploit accessible automated tools and malware-as-a-service platforms, lowering the entry barrier for launching attacks. The cybersecurity landscape must prepare for a wider spectrum of threat capabilities, merging professional threat actors' complexity with the growing volume of opportunistic script kiddie attacks.
threat actor vs script kiddie Infographic
 techiny.com
techiny.com