Smishing exploits SMS messages to deceive users into revealing personal information or clicking malicious links, while vishing uses phone calls to manipulate victims into disclosing sensitive data through social engineering tactics. Both attack vectors rely on impersonation and urgency to bypass user caution, but smishing often incorporates embedded links or attachments, whereas vishing depends on verbal communication and psychological manipulation. Implementing multi-factor authentication and educating users about these threats significantly reduces the risk of falling victim to smishing and vishing attacks.
Table of Comparison
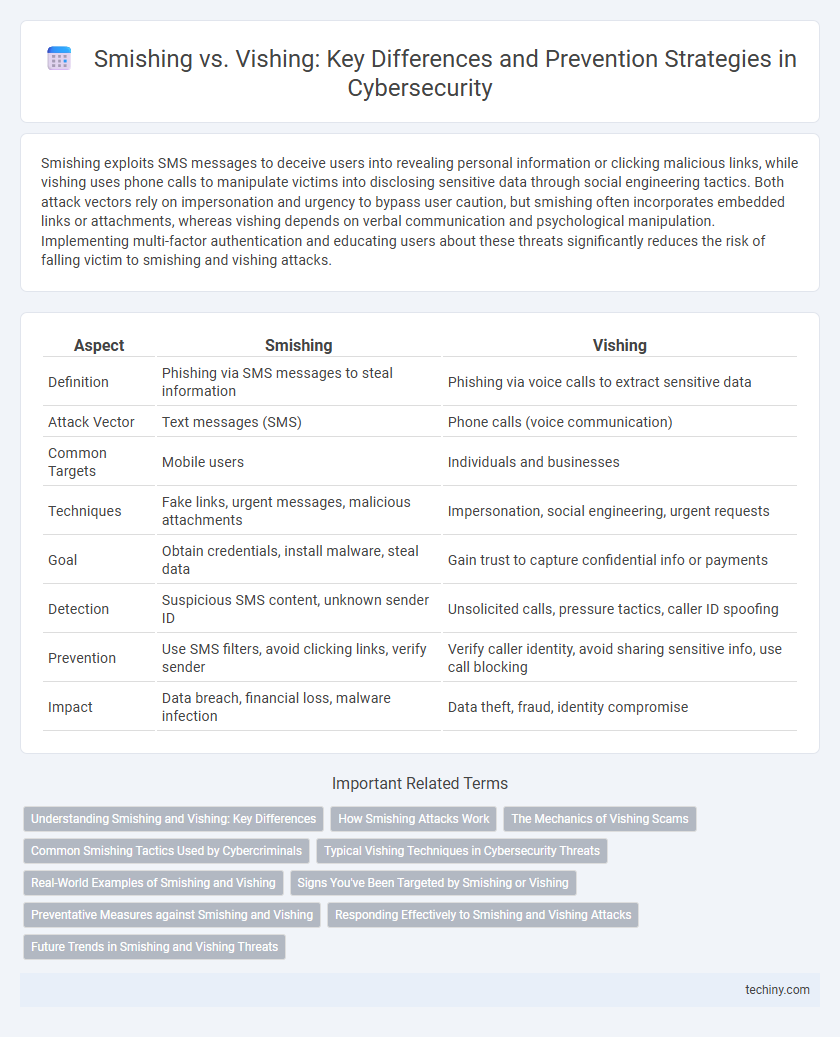
| Aspect | Smishing | Vishing |
|---|---|---|
| Definition | Phishing via SMS messages to steal information | Phishing via voice calls to extract sensitive data |
| Attack Vector | Text messages (SMS) | Phone calls (voice communication) |
| Common Targets | Mobile users | Individuals and businesses |
| Techniques | Fake links, urgent messages, malicious attachments | Impersonation, social engineering, urgent requests |
| Goal | Obtain credentials, install malware, steal data | Gain trust to capture confidential info or payments |
| Detection | Suspicious SMS content, unknown sender ID | Unsolicited calls, pressure tactics, caller ID spoofing |
| Prevention | Use SMS filters, avoid clicking links, verify sender | Verify caller identity, avoid sharing sensitive info, use call blocking |
| Impact | Data breach, financial loss, malware infection | Data theft, fraud, identity compromise |
Understanding Smishing and Vishing: Key Differences
Smishing involves cybercriminals sending deceptive SMS messages to trick users into revealing personal information or clicking malicious links, often exploiting mobile device vulnerabilities. Vishing, on the other hand, uses voice calls or VoIP technology to impersonate trusted entities, manipulating victims through social engineering tactics to disclose sensitive data or authorize fraudulent transactions. Recognizing these tactics helps cybersecurity professionals implement targeted defenses, such as SMS filtering and call authentication systems, to mitigate the risks associated with mobile and voice communication scams.
How Smishing Attacks Work
Smishing attacks exploit SMS messaging to deceive victims into providing sensitive information by sending fraudulent texts that appear to come from trusted sources. These messages often contain links to fake websites or prompt recipients to call malicious numbers where attackers impersonate legitimate organizations. By leveraging social engineering techniques, smishers manipulate emotions like urgency or fear to trick users into disclosing passwords, credit card details, or installing malware.
The Mechanics of Vishing Scams
Vishing scams exploit Voice over Internet Protocol (VoIP) technology to impersonate trusted entities, such as banks or government agencies, through fraudulent phone calls. Attackers manipulate caller ID systems to display legitimate numbers, increasing the credibility of their requests for sensitive information like Social Security numbers or account passwords. Victims are pressured to disclose confidential data or perform unauthorized actions, making vishing a highly effective social engineering tactic in cybersecurity breaches.
Common Smishing Tactics Used by Cybercriminals
Cybercriminals commonly use smishing tactics such as sending fraudulent text messages that impersonate trusted institutions to trick victims into revealing personal information or clicking malicious links. These messages often create a sense of urgency, referencing fake security alerts or account issues to prompt immediate action. By exploiting mobile device vulnerabilities and human psychology, smishing attacks bypass traditional email filters and increase the risk of identity theft and financial fraud.
Typical Vishing Techniques in Cybersecurity Threats
Typical vishing techniques in cybersecurity threats involve attackers using phone calls to impersonate trusted entities such as banks, government agencies, or tech support to extract sensitive information like passwords, Social Security numbers, or credit card details. Attackers often employ Caller ID spoofing to make the call appear legitimate and create a sense of urgency or fear to manipulate victims into compliance. These social engineering tactics exploit human psychology rather than technical vulnerabilities, making them highly effective in corporate and personal cybersecurity breaches.
Real-World Examples of Smishing and Vishing
Smishing attacks often involve fraudulent SMS messages that mimic bank alerts or delivery notifications, such as the 2022 case where users received texts claiming suspicious activity on their PayPal accounts to steal login credentials. Vishing scams frequently exploit voice calls, exemplified by the FBI imposter calls targeting elderly victims to extract Social Security numbers under the guise of legal threats. Both attack types leverage social engineering tactics to induce panic and prompt immediate action, increasing the likelihood of sensitive data compromise.
Signs You've Been Targeted by Smishing or Vishing
Unusual requests for personal information via text messages or phone calls often indicate smishing or vishing attempts, respectively. Receiving urgent messages urging immediate action, especially with suspicious links or phone numbers, signals potential phishing attacks. Unexpected communication from trusted organizations that prompts verification of sensitive data without official channels highlights the likelihood of being targeted by smishing or vishing scams.
Preventative Measures against Smishing and Vishing
Preventative measures against smishing include never clicking on links or downloading attachments from unknown SMS senders and enabling SMS filtering features on mobile devices. For vishing, verifying caller identities by contacting organizations directly through official phone numbers and avoiding sharing sensitive information over the phone are crucial. Implementing multi-factor authentication and regular employee cybersecurity training further reduces the risk of falling victim to these social engineering attacks.
Responding Effectively to Smishing and Vishing Attacks
Effective response to smishing attacks involves immediately avoiding clicking on suspicious links or sharing personal information through texts, and verifying the sender's identity using official contact methods. In the case of vishing, confirm the caller's legitimacy by independently contacting the organization they claim to represent and avoid disclosing sensitive data during unsolicited calls. Reporting these attempts to cybersecurity teams or relevant authorities helps limit the impact and prevents further exploitation.
Future Trends in Smishing and Vishing Threats
Emerging trends in smishing and vishing threats reveal increasing use of artificial intelligence and machine learning to create more personalized and convincing attacks. Cybercriminals are leveraging deepfake audio and advanced social engineering techniques to bypass traditional security measures and exploit user trust. Proactive adoption of multi-factor authentication, AI-powered anomaly detection, and continuous user education will be critical to mitigating future risks in these evolving threat landscapes.
Smishing vs Vishing Infographic
 techiny.com
techiny.com