Threat intelligence involves gathering and analyzing data on current and emerging cyber threats to inform proactive defense strategies. Threat hunting actively searches for hidden threats within an organization's network by leveraging threat intelligence insights and advanced detection techniques. Together, these approaches enable a robust cybersecurity posture by combining strategic awareness with tactical identification and response.
Table of Comparison
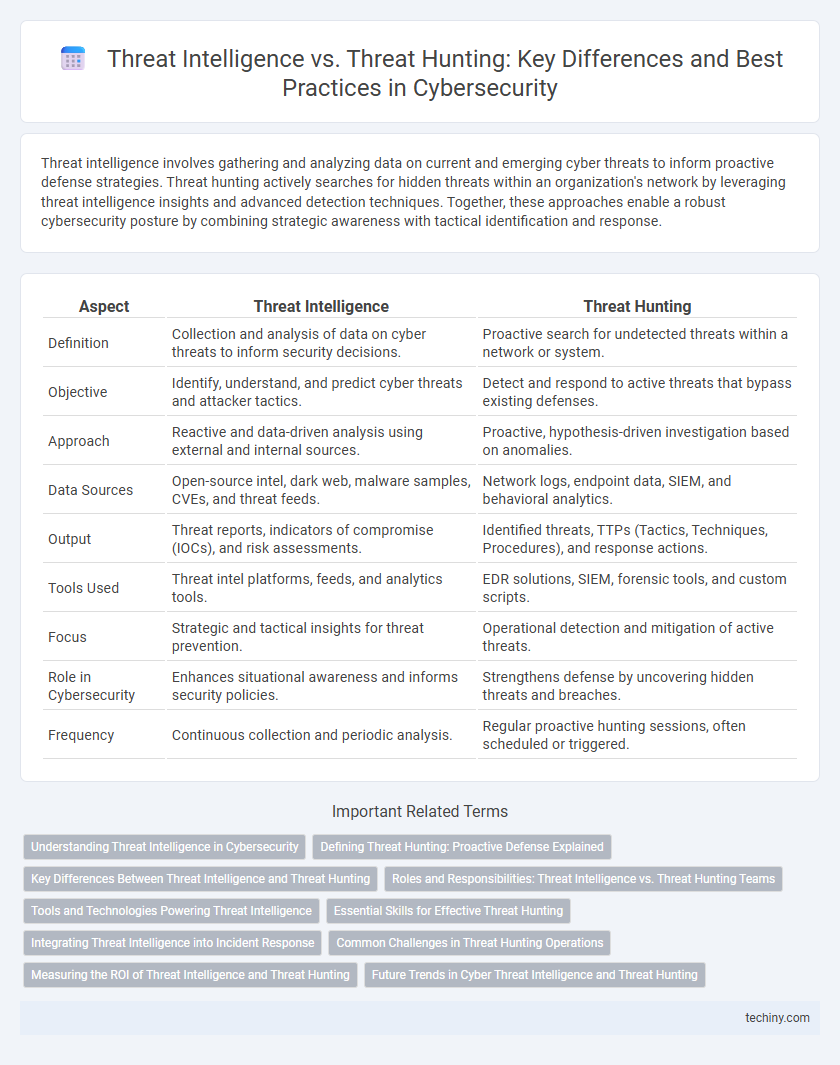
| Aspect | Threat Intelligence | Threat Hunting |
|---|---|---|
| Definition | Collection and analysis of data on cyber threats to inform security decisions. | Proactive search for undetected threats within a network or system. |
| Objective | Identify, understand, and predict cyber threats and attacker tactics. | Detect and respond to active threats that bypass existing defenses. |
| Approach | Reactive and data-driven analysis using external and internal sources. | Proactive, hypothesis-driven investigation based on anomalies. |
| Data Sources | Open-source intel, dark web, malware samples, CVEs, and threat feeds. | Network logs, endpoint data, SIEM, and behavioral analytics. |
| Output | Threat reports, indicators of compromise (IOCs), and risk assessments. | Identified threats, TTPs (Tactics, Techniques, Procedures), and response actions. |
| Tools Used | Threat intel platforms, feeds, and analytics tools. | EDR solutions, SIEM, forensic tools, and custom scripts. |
| Focus | Strategic and tactical insights for threat prevention. | Operational detection and mitigation of active threats. |
| Role in Cybersecurity | Enhances situational awareness and informs security policies. | Strengthens defense by uncovering hidden threats and breaches. |
| Frequency | Continuous collection and periodic analysis. | Regular proactive hunting sessions, often scheduled or triggered. |
Understanding Threat Intelligence in Cybersecurity
Threat Intelligence in cybersecurity involves systematically collecting, analyzing, and interpreting data about emerging cyber threats to anticipate and mitigate potential attacks. It provides actionable insights that enhance an organization's defensive strategies by identifying threat actors, attack vectors, and Indicators of Compromise (IOCs). Understanding threat intelligence enables security teams to proactively prioritize risks, reduce response times, and strengthen overall cyber resilience.
Defining Threat Hunting: Proactive Defense Explained
Threat hunting involves proactively searching through networks and systems to identify hidden cyber threats before they cause harm, using advanced analytics and behavioral analysis. Unlike threat intelligence, which relies on external data and known indicators of compromise, threat hunting leverages internal telemetry and hypothesis-driven investigations to uncover novel attacks. This proactive defense approach reduces dwell time and enhances an organization's ability to detect stealthy adversaries.
Key Differences Between Threat Intelligence and Threat Hunting
Threat Intelligence involves collecting and analyzing data on emerging cyber threats to provide actionable insights, while Threat Hunting is a proactive process aimed at detecting hidden threats within an organization's network. Threat Intelligence focuses on external threat data and predictive analysis, whereas Threat Hunting relies on hypothesis-driven investigation and real-time network monitoring. Understanding these key differences enables cybersecurity teams to integrate both approaches for comprehensive threat detection and response.
Roles and Responsibilities: Threat Intelligence vs. Threat Hunting Teams
Threat Intelligence teams specialize in gathering, analyzing, and disseminating data on emerging cyber threats, enabling organizations to anticipate and defend against potential attacks. Threat Hunting teams actively search for hidden threats within the network environment by leveraging advanced analytics, behavioral analysis, and threat intelligence reports to identify and mitigate breaches early. Both roles collaborate closely, with Threat Intelligence providing context and actionable insights while Threat Hunting focuses on proactive threat detection and response.
Tools and Technologies Powering Threat Intelligence
Threat intelligence is powered by advanced tools like Security Information and Event Management (SIEM) systems, Threat Intelligence Platforms (TIPs), and machine learning-driven analytics that aggregate, correlate, and analyze vast datasets to identify emerging cyber threats. These technologies enable real-time threat data sharing, automated indicator of compromise (IOC) extraction, and predictive modeling to enhance situational awareness. In contrast, threat hunting relies more on behavioral analytics platforms and endpoint detection and response (EDR) tools to proactively search for hidden threats within networks.
Essential Skills for Effective Threat Hunting
Effective threat hunting requires strong analytical skills to identify patterns and anomalies within vast datasets, complemented by in-depth knowledge of malware behavior and attack vectors. Proficiency in cybersecurity tools such as SIEM, EDR, and network traffic analysis platforms enhances the ability to proactively detect threats before they manifest. Expertise in scripting and automation accelerates investigation processes, enabling the dynamic adaptation to evolving threat landscapes and reducing response time.
Integrating Threat Intelligence into Incident Response
Integrating threat intelligence into incident response enhances the ability to identify, analyze, and mitigate cyber threats in real-time by providing actionable insights from diverse threat data sources such as malware indicators and attack patterns. Threat hunting leverages this intelligence proactively to detect hidden threats within the network before they execute, improving response speed and accuracy. Effective collaboration between threat intelligence and incident response teams strengthens cybersecurity posture by enabling timely threat detection, contextualized analysis, and informed remediation strategies.
Common Challenges in Threat Hunting Operations
Threat hunting operations face common challenges such as the overwhelming volume of data to analyze, the scarcity of skilled analysts, and the difficulty in validating threats without generating excessive false positives. Organizations often struggle with integrating disparate threat intelligence sources to create comprehensive hunting hypotheses. Effective threat hunting demands continuous tuning of detection models and collaboration between threat intelligence teams to improve accuracy and response times.
Measuring the ROI of Threat Intelligence and Threat Hunting
Measuring the ROI of Threat Intelligence involves evaluating the reduction in risk exposure and incident response times by analyzing data from threat feeds, vulnerability assessments, and attack simulations. Threat Hunting ROI is gauged through metrics such as the number of previously undetected threats uncovered, dwell time reduction, and improvements in detection accuracy, emphasizing proactive mitigation. Combining quantitative indicators like cost savings from prevented breaches and qualitative benefits including enhanced situational awareness provides a comprehensive view of cybersecurity investment returns.
Future Trends in Cyber Threat Intelligence and Threat Hunting
Emerging trends in cyber threat intelligence emphasize the integration of artificial intelligence and machine learning to enhance predictive capabilities and automate anomaly detection. Threat hunting is evolving with real-time behavioral analytics and adaptive algorithms that proactively identify sophisticated, previously unknown threats. Future developments will likely focus on collaborative intelligence sharing platforms and advanced automation to improve response times and resilience against increasingly complex cyber attacks.
Threat Intelligence vs Threat Hunting Infographic
 techiny.com
techiny.com