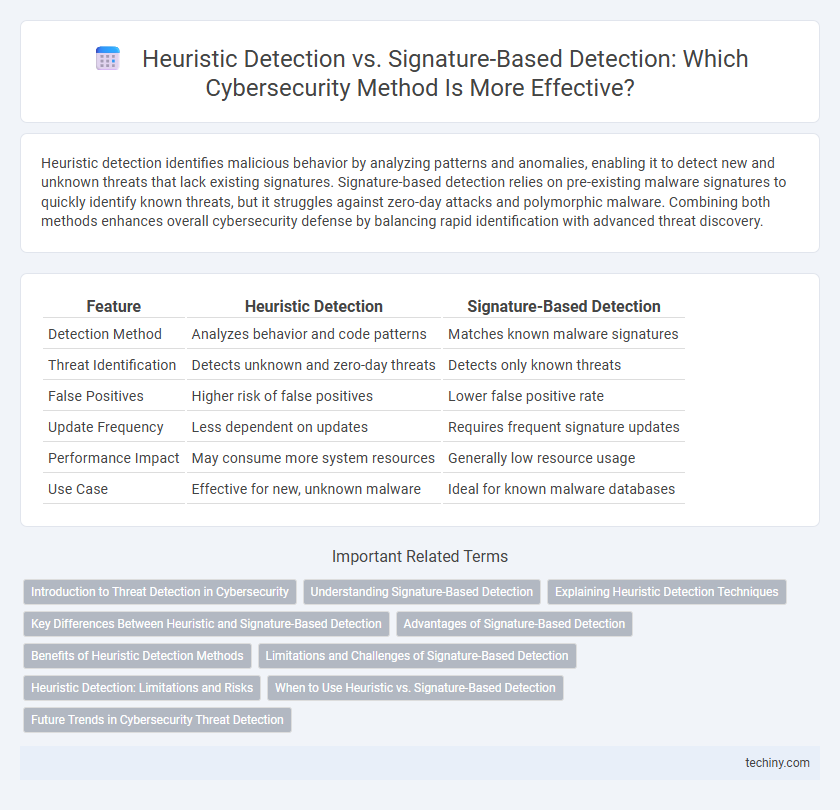
Heuristic detection identifies malicious behavior by analyzing patterns and anomalies, enabling it to detect new and unknown threats that lack existing signatures. Signature-based detection relies on pre-existing malware signatures to quickly identify known threats, but it struggles against zero-day attacks and polymorphic malware. Combining both methods enhances overall cybersecurity defense by balancing rapid identification with advanced threat discovery.
Table of Comparison
| Feature | Heuristic Detection | Signature-Based Detection |
|---|---|---|
| Detection Method | Analyzes behavior and code patterns | Matches known malware signatures |
| Threat Identification | Detects unknown and zero-day threats | Detects only known threats |
| False Positives | Higher risk of false positives | Lower false positive rate |
| Update Frequency | Less dependent on updates | Requires frequent signature updates |
| Performance Impact | May consume more system resources | Generally low resource usage |
| Use Case | Effective for new, unknown malware | Ideal for known malware databases |
Introduction to Threat Detection in Cybersecurity
Heuristic detection identifies new and unknown cyber threats by analyzing patterns and behaviors rather than relying on known malware signatures, enabling proactive defense against zero-day attacks. Signature-based detection matches files or activities against a database of known threat fingerprints, providing fast and accurate identification of established malware. Combining heuristic and signature-based methods enhances cybersecurity by balancing the detection of both emerging and existing threats.
Understanding Signature-Based Detection
Signature-based detection relies on a database of known malware signatures to identify threats by matching code patterns, making it highly effective against previously identified attacks. This method offers fast and accurate detection with low false-positive rates but struggles to identify new, unknown threats or polymorphic malware. Organizations leverage signature-based detection as a foundational cybersecurity tool, continuously updating signature databases to maintain protection against evolving malware variants.
Explaining Heuristic Detection Techniques
Heuristic detection techniques analyze the behavior and characteristics of files or programs to identify potential threats by recognizing suspicious patterns and anomalies rather than relying solely on known malware signatures. This method uses algorithms and rules to evaluate code structure, system activity, and execution behavior, enabling the detection of new, unknown, or modified malware variants. By focusing on dynamic analysis and behavioral indicators, heuristic detection enhances cybersecurity defenses against zero-day attacks and polymorphic malware.
Key Differences Between Heuristic and Signature-Based Detection
Heuristic detection identifies threats by analyzing unusual behavior patterns and potential malware characteristics, whereas signature-based detection relies on known malware signatures stored in databases. Heuristic methods enable the identification of new, unknown threats through dynamic analysis, while signature-based systems are effective only against previously identified malware. The key difference lies in heuristic detection's proactive approach versus the reactive nature of signature-based detection.
Advantages of Signature-Based Detection
Signature-based detection offers rapid identification of known malware by comparing files against a database of recognized threat signatures, ensuring high accuracy with minimal false positives. It excels in resource efficiency, enabling quick scans without significant system impact. This method provides a straightforward mechanism for updating defenses through regular signature database enhancements, maintaining effective protection against established threats.
Benefits of Heuristic Detection Methods
Heuristic detection methods enhance cybersecurity by identifying novel and previously unknown malware through behavior analysis and pattern recognition, rather than relying solely on known virus signatures. This proactive approach enables faster response times to emerging threats and reduces vulnerability to zero-day attacks. Heuristic techniques also improve detection accuracy by evaluating suspicious activities in real-time, minimizing the risk of false negatives compared to signature-based systems.
Limitations and Challenges of Signature-Based Detection
Signature-based detection in cybersecurity faces significant limitations due to its reliance on predefined threat signatures, which cannot identify new or unknown malware variants. This method struggles with zero-day attacks and polymorphic viruses that constantly alter their code to evade detection. Its dependency on regular updates and extensive signature databases often results in delayed response times and decreased efficiency against evolving cyber threats.
Heuristic Detection: Limitations and Risks
Heuristic detection in cybersecurity identifies threats by analyzing behaviors and patterns rather than relying on known signatures, but it often generates false positives due to its predictive nature. Its reliance on algorithms can lead to missed advanced persistent threats (APTs) that mimic legitimate processes, reducing detection accuracy. Furthermore, heuristic methods demand constant updates and tuning to adapt to evolving malware tactics, increasing operational complexity and resource consumption.
When to Use Heuristic vs. Signature-Based Detection
Heuristic detection excels in identifying unknown or evolving malware by analyzing code behavior and suspicious patterns, making it essential for zero-day threats and polymorphic viruses. Signature-based detection is most effective for known threats with established malware signatures, providing faster and more accurate detection with fewer false positives. Organizations should deploy heuristic methods when facing novel or sophisticated attacks while relying on signature-based detection for routine scanning of established malware databases.
Future Trends in Cybersecurity Threat Detection
Heuristic detection leverages behavior analysis and machine learning algorithms to identify unknown and evolving threats, surpassing traditional signature-based detection that relies on known malware patterns. Future trends indicate an increased integration of AI-driven heuristic models with real-time threat intelligence to enhance accuracy and reduce false positives. Emerging technologies such as behavioral analytics, anomaly detection, and adaptive learning systems will play critical roles in proactive cybersecurity threat detection.
Heuristic Detection vs Signature-Based Detection Infographic
 techiny.com
techiny.com