Zero trust security eliminates implicit trust by continuously verifying every user and device attempting to access resources, reducing the risk of insider threats and lateral movement within networks. Perimeter security relies on traditional barriers like firewalls and VPNs to block external threats, but struggles to protect against sophisticated attacks or breaches originating inside the network. Embracing zero trust frameworks enhances cybersecurity resilience by enforcing strict access controls and micro-segmentation beyond the limitations of perimeter defenses.
Table of Comparison
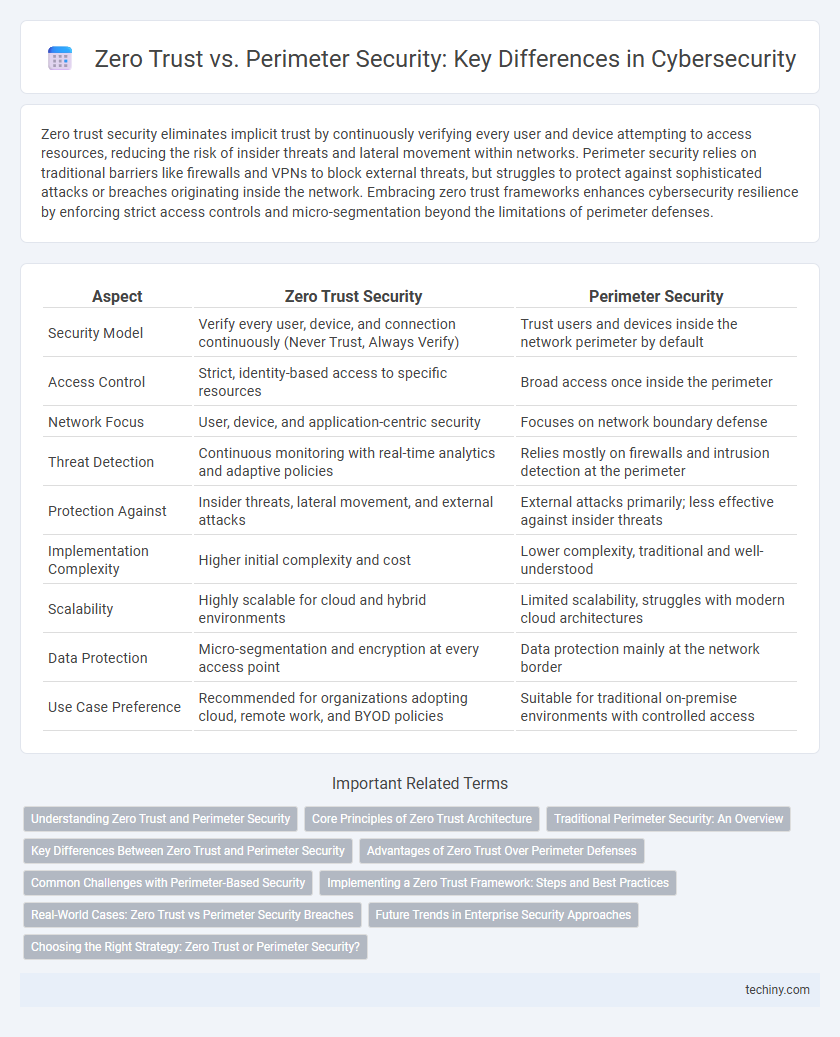
| Aspect | Zero Trust Security | Perimeter Security |
|---|---|---|
| Security Model | Verify every user, device, and connection continuously (Never Trust, Always Verify) | Trust users and devices inside the network perimeter by default |
| Access Control | Strict, identity-based access to specific resources | Broad access once inside the perimeter |
| Network Focus | User, device, and application-centric security | Focuses on network boundary defense |
| Threat Detection | Continuous monitoring with real-time analytics and adaptive policies | Relies mostly on firewalls and intrusion detection at the perimeter |
| Protection Against | Insider threats, lateral movement, and external attacks | External attacks primarily; less effective against insider threats |
| Implementation Complexity | Higher initial complexity and cost | Lower complexity, traditional and well-understood |
| Scalability | Highly scalable for cloud and hybrid environments | Limited scalability, struggles with modern cloud architectures |
| Data Protection | Micro-segmentation and encryption at every access point | Data protection mainly at the network border |
| Use Case Preference | Recommended for organizations adopting cloud, remote work, and BYOD policies | Suitable for traditional on-premise environments with controlled access |
Understanding Zero Trust and Perimeter Security
Zero Trust security operates on the principle of "never trust, always verify," continuously authenticating and authorizing every user and device regardless of network location, while perimeter security relies on a defined network boundary to block unauthorized access. Unlike traditional perimeter security, which assumes internal network trust, Zero Trust limits lateral movement by enforcing strict access controls at all times. This shift enhances protection against modern threats like insider attacks and sophisticated breaches that bypass perimeter defenses.
Core Principles of Zero Trust Architecture
Zero Trust Architecture centers on the core principle of "never trust, always verify," ensuring continuous authentication and authorization of users and devices regardless of their location. Unlike perimeter security that relies on a fixed boundary to block threats, Zero Trust enforces strict access controls and micro-segmentation to limit lateral movement within the network. This model incorporates least privilege access, multi-factor authentication (MFA), and real-time monitoring to safeguard data and applications from both external and internal threats.
Traditional Perimeter Security: An Overview
Traditional perimeter security relies on established network boundaries, using firewalls and intrusion detection systems to protect internal assets from external threats. This model assumes trusted users inside the network, creating vulnerabilities when insider threats or lateral movement occur. Although effective against external attacks, perimeter security often fails to address complex, modern cyber threats requiring more granular access control.
Key Differences Between Zero Trust and Perimeter Security
Zero Trust security eliminates implicit trust by continuously verifying every user and device, whereas Perimeter Security relies on a defined boundary to filter threats. Zero Trust operates on least-privilege access and micro-segmentation, limiting lateral movement inside a network, while Perimeter Security primarily defends against external attacks. The shift to Zero Trust addresses modern challenges like remote work and cloud environments, making traditional perimeter defenses less effective.
Advantages of Zero Trust Over Perimeter Defenses
Zero Trust architecture minimizes the risk of internal and external threats by verifying every user and device regardless of network location, unlike traditional perimeter security that relies on a single fortified boundary. Continuous monitoring and strict access controls in Zero Trust reduce the attack surface and prevent lateral movement within the network. This approach ensures data protection through micro-segmentation and least-privilege access, enhancing overall cybersecurity resilience.
Common Challenges with Perimeter-Based Security
Perimeter-based security struggles with evolving cyber threats as attackers increasingly bypass traditional firewalls through phishing, malware, or insider attacks. Static defenses often lack visibility into internal network activities, leaving organizations vulnerable to lateral movement and data breaches. This approach also fails to adequately protect remote and cloud environments, reducing overall security effectiveness in modern distributed networks.
Implementing a Zero Trust Framework: Steps and Best Practices
Implementing a Zero Trust framework involves continuous verification of user identities, strict access controls based on the principle of least privilege, and micro-segmentation to limit lateral movement within systems. Key best practices include deploying multi-factor authentication (MFA), leveraging advanced threat detection and response tools, and regularly auditing network activities to identify anomalies. Integrating identity and access management (IAM) solutions with real-time monitoring enhances security posture beyond traditional perimeter defenses.
Real-World Cases: Zero Trust vs Perimeter Security Breaches
Zero Trust architecture limits access based on user identity and device compliance, significantly reducing the risk of lateral movement during breaches, as seen in Microsoft's mitigation of the SolarWinds attack. Perimeter security relies heavily on hardened network borders, which failed during the 2017 Equifax breach when attackers exploited a vulnerability inside the network. Real-world incidents demonstrate Zero Trust's effectiveness in containing breaches by minimizing implicit trust, contrasting sharply with perimeter security's single-layer reliance that often leaves organizations exposed.
Future Trends in Enterprise Security Approaches
Zero Trust architecture prioritizes identity verification and continuous monitoring, rejecting the traditional perimeter-based defenses that assume internal network trustworthiness. Future enterprise security trends emphasize adaptive risk-based authentication, AI-powered threat detection, and micro-segmentation to minimize attack surfaces and improve resilience. Integration of Zero Trust with cloud-native security solutions accelerates secure digital transformation across hybrid and multi-cloud environments.
Choosing the Right Strategy: Zero Trust or Perimeter Security?
Zero Trust security eliminates implicit trust by continuously verifying user identities and device health, reducing risks from insider threats and lateral movement. Perimeter security relies on established network boundaries and firewalls, which can be insufficient against sophisticated cyberattacks targeting remote access or cloud environments. Organizations should evaluate their infrastructure complexity, user mobility, and threat landscape to determine if a Zero Trust model or traditional perimeter security better aligns with their cybersecurity goals.
Zero trust vs perimeter security Infographic
 techiny.com
techiny.com