Social engineering exploits human psychology to manipulate individuals into revealing confidential information, making it a significant cybersecurity threat. In contrast, physical breach involves unauthorized access to a facility or hardware, directly compromising sensitive data and systems. Both tactics require robust defense strategies combining employee training and physical security controls to prevent potential intrusions.
Table of Comparison
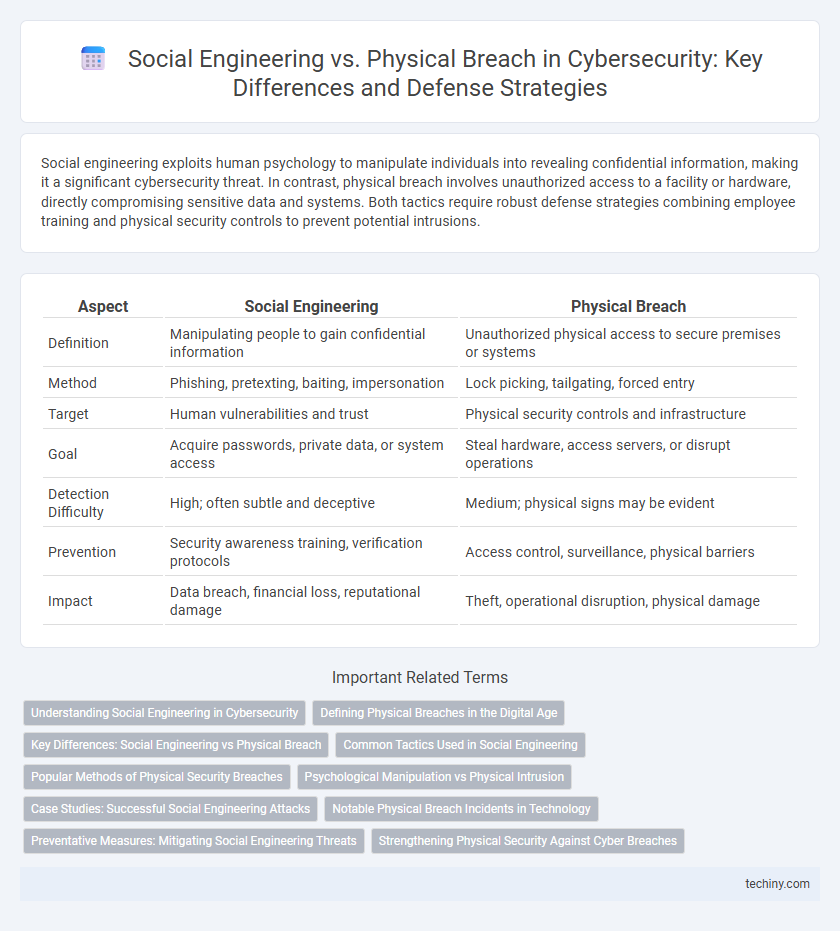
| Aspect | Social Engineering | Physical Breach |
|---|---|---|
| Definition | Manipulating people to gain confidential information | Unauthorized physical access to secure premises or systems |
| Method | Phishing, pretexting, baiting, impersonation | Lock picking, tailgating, forced entry |
| Target | Human vulnerabilities and trust | Physical security controls and infrastructure |
| Goal | Acquire passwords, private data, or system access | Steal hardware, access servers, or disrupt operations |
| Detection Difficulty | High; often subtle and deceptive | Medium; physical signs may be evident |
| Prevention | Security awareness training, verification protocols | Access control, surveillance, physical barriers |
| Impact | Data breach, financial loss, reputational damage | Theft, operational disruption, physical damage |
Understanding Social Engineering in Cybersecurity
Social engineering in cybersecurity exploits human psychology to manipulate individuals into divulging confidential information or granting unauthorized access, often bypassing technical defenses. Unlike physical breaches that rely on force or stealth to infiltrate facilities, social engineering targets human vulnerabilities through tactics such as phishing, pretexting, or baiting. Recognizing and mitigating social engineering threats is crucial in strengthening an organization's overall security posture against both digital and physical attacks.
Defining Physical Breaches in the Digital Age
Physical breaches in the digital age refer to unauthorized access to secured facilities or devices, enabling direct manipulation or theft of hardware containing sensitive data. These breaches often involve tactics such as tailgating, lock picking, or exploiting lax access controls to circumvent digital defenses. Understanding the interplay between physical security measures and cybersecurity protocols is critical for safeguarding organizational assets against combined threats.
Key Differences: Social Engineering vs Physical Breach
Social engineering exploits human psychology to manipulate individuals into divulging confidential information or granting unauthorized access, whereas physical breaches involve direct unauthorized entry into secured physical locations or systems. Social engineering attacks often use methods such as phishing, pretexting, or baiting, targeting the weakest link: human trust. Physical breaches rely on tactics like lock picking, tailgating, or stealing access cards, emphasizing the importance of robust physical security controls and employee vigilance.
Common Tactics Used in Social Engineering
Social engineering tactics commonly include phishing emails, pretexting, baiting, and tailgating to manipulate individuals into divulging confidential information or granting unauthorized access. Attackers exploit psychological principles like trust, fear, and urgency to bypass technical defenses without physically breaching security perimeters. Unlike physical breaches requiring physical access to facilities, social engineering targets human vulnerabilities leveraging communication channels to infiltrate organizations.
Popular Methods of Physical Security Breaches
Popular methods of physical security breaches include tailgating, where unauthorized individuals follow authorized personnel into secure areas, and lock picking, which bypasses mechanical locks without detection. Other common tactics involve dumpster diving to retrieve sensitive information and exploiting unattended access points such as open doors or windows. These physical intrusion techniques often complement social engineering attacks, emphasizing the need for comprehensive security protocols.
Psychological Manipulation vs Physical Intrusion
Social engineering exploits psychological manipulation to deceive individuals into divulging confidential information or performing actions that compromise security, targeting human vulnerabilities rather than technical defenses. Physical breaches involve unauthorized physical intrusion into secured facilities to steal information, damage assets, or install malicious devices, relying on bypassing physical barriers like locks and surveillance. Understanding the distinction enhances comprehensive cybersecurity strategies by addressing both human factors and physical security mechanisms.
Case Studies: Successful Social Engineering Attacks
Case studies reveal that social engineering attacks often exploit human psychology to bypass sophisticated physical security measures, as seen in the 2011 RSA SecurID breach where attackers manipulated employees through targeted phishing emails. Unlike physical breaches that rely on unauthorized access to facilities, social engineering attacks leverage deception, such as pretexting and spear-phishing, to extract sensitive information remotely. These incidents underscore the critical need for comprehensive employee training and multi-layered security protocols to mitigate risks associated with human vulnerabilities.
Notable Physical Breach Incidents in Technology
Notable physical breach incidents in technology highlight the critical vulnerabilities beyond digital defenses, such as the 2010 Stuxnet malware attack facilitated by USB drives physically introduced into Iranian nuclear facilities. Another significant event is the 2013 Target data breach, where attackers gained entry by stealing credentials through physical access to third-party vendor systems. These cases underscore the necessity of robust physical security protocols alongside cybersecurity measures to prevent unauthorized access and data compromise.
Preventative Measures: Mitigating Social Engineering Threats
Implement multifactor authentication and conduct regular cybersecurity training to empower employees against phishing and pretexting attacks. Employ robust access controls and continuously update security policies to detect and prevent unauthorized social engineering attempts. Utilize simulated social engineering exercises to reinforce awareness and identify vulnerabilities before attackers exploit them.
Strengthening Physical Security Against Cyber Breaches
Strengthening physical security is crucial to preventing cyber breaches, as unauthorized physical access can lead to direct exploitation of hardware and sensitive information. Implementing multi-factor authentication, secure access controls, and surveillance systems reduces the risk of social engineering tactics targeting personnel to gain physical entry. Robust physical barriers combined with employee training create a comprehensive defense against security breaches that exploit both human factors and infrastructure vulnerabilities.
Social Engineering vs Physical Breach Infographic
 techiny.com
techiny.com