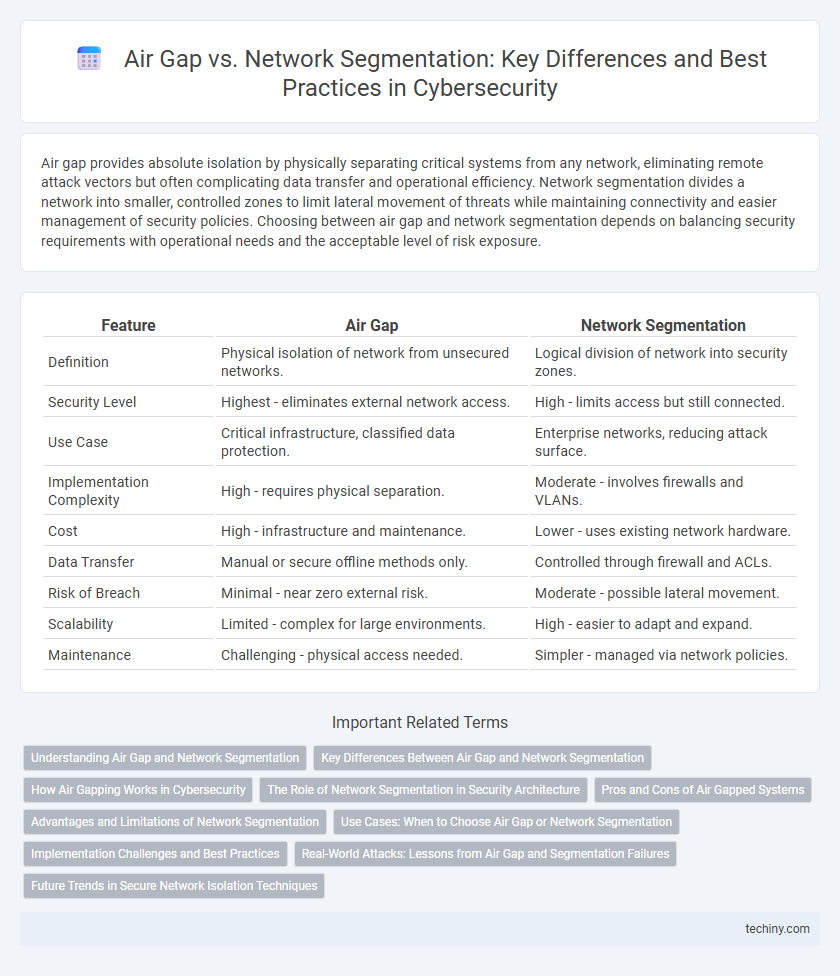
Air gap provides absolute isolation by physically separating critical systems from any network, eliminating remote attack vectors but often complicating data transfer and operational efficiency. Network segmentation divides a network into smaller, controlled zones to limit lateral movement of threats while maintaining connectivity and easier management of security policies. Choosing between air gap and network segmentation depends on balancing security requirements with operational needs and the acceptable level of risk exposure.
Table of Comparison
| Feature | Air Gap | Network Segmentation |
|---|---|---|
| Definition | Physical isolation of network from unsecured networks. | Logical division of network into security zones. |
| Security Level | Highest - eliminates external network access. | High - limits access but still connected. |
| Use Case | Critical infrastructure, classified data protection. | Enterprise networks, reducing attack surface. |
| Implementation Complexity | High - requires physical separation. | Moderate - involves firewalls and VLANs. |
| Cost | High - infrastructure and maintenance. | Lower - uses existing network hardware. |
| Data Transfer | Manual or secure offline methods only. | Controlled through firewall and ACLs. |
| Risk of Breach | Minimal - near zero external risk. | Moderate - possible lateral movement. |
| Scalability | Limited - complex for large environments. | High - easier to adapt and expand. |
| Maintenance | Challenging - physical access needed. | Simpler - managed via network policies. |
Understanding Air Gap and Network Segmentation
Air gap refers to a physical separation between secure and unsecured networks, ensuring complete isolation to prevent unauthorized access or data leakage. Network segmentation involves dividing a network into smaller, controlled segments to limit the spread of cyber threats and contain breaches within isolated zones. Both strategies enhance cybersecurity by reducing attack surfaces but differ in implementation, with air gaps providing maximum isolation and network segmentation offering granular control over traffic flow.
Key Differences Between Air Gap and Network Segmentation
Air Gap involves completely isolating a system from any network connections, ensuring no direct or indirect communication with external systems, which provides maximum security for critical assets. Network Segmentation divides a network into smaller, controlled segments using firewalls or VLANs, allowing better traffic monitoring and containment of breaches while maintaining connectivity. Key differences lie in Air Gap's total isolation versus Network Segmentation's controlled, granular access to limit spread and manage risks within connected environments.
How Air Gapping Works in Cybersecurity
Air gapping works in cybersecurity by physically isolating a computer or network from unsecured networks, including the internet, to prevent unauthorized access and cyber threats. This isolation ensures sensitive data and critical systems remain disconnected, eliminating the risk of remote hacking, malware, or data exfiltration. Air gapped environments often involve strict manual controls for data transfer, such as using removable media, to maintain security integrity.
The Role of Network Segmentation in Security Architecture
Network segmentation enhances cybersecurity by isolating sensitive systems within distinct network zones, reducing the attack surface and limiting lateral movement of threats. Unlike air gapping, which physically separates networks, segmentation applies virtual barriers through firewalls and access controls to contain breaches. Effective segmentation enforces least privilege access policies and supports threat detection by creating controlled, monitored communication paths.
Pros and Cons of Air Gapped Systems
Air-gapped systems provide a high level of security by physically isolating critical networks from the internet, minimizing exposure to external cyber threats such as malware or ransomware attacks. However, this isolation complicates data transfer and system updates, often requiring manual intervention that can lead to operational inefficiencies and increased maintenance costs. Despite enhanced protection against remote intrusions, air gaps do not eliminate insider threats or vulnerabilities introduced by removable media or human error.
Advantages and Limitations of Network Segmentation
Network segmentation enhances cybersecurity by dividing a network into isolated segments, reducing the attack surface and limiting lateral movement of threats. It allows more granular control, easier monitoring, and improved regulatory compliance, addressing vulnerabilities without complete network isolation. However, network segmentation requires complex configuration and ongoing management to maintain effectiveness, and may not fully prevent sophisticated attacks compared to air-gapped systems.
Use Cases: When to Choose Air Gap or Network Segmentation
Air gap security is best suited for protecting highly sensitive systems where absolute isolation from any network is required, such as in military, nuclear facilities, or critical infrastructure environments. Network segmentation offers a flexible security approach for enterprise IT environments, enabling containment of breaches by dividing the network into smaller, controlled segments based on access levels and functionality. Organizations should choose air gaps when uncompromising physical separation is necessary, while network segmentation is ideal for balancing security with operational efficiency and remote accessibility.
Implementation Challenges and Best Practices
Implementing air gap systems requires rigorous physical isolation, creating challenges in maintenance and real-time data access, especially in dynamic operational environments. Network segmentation demands precise configuration to manage access controls and monitor traffic, reducing the risk of lateral movement without sacrificing performance. Best practices involve combining robust endpoint security with continuous monitoring and strict policy enforcement to balance security with operational flexibility.
Real-World Attacks: Lessons from Air Gap and Segmentation Failures
Real-world cyber attacks highlight critical vulnerabilities in both air gap and network segmentation strategies, where attackers exploit misconfigurations and insider threats to bypass isolation controls. Incidents like the Stuxnet worm demonstrate that even air-gapped systems can be compromised through physical or supply chain attacks, while segmentation failures often result from inadequate enforcement of access controls and lateral movement detection. Effective cybersecurity requires continuous monitoring, rigorous policy enforcement, and layered defenses to mitigate risks inherent in these isolation techniques.
Future Trends in Secure Network Isolation Techniques
Future trends in secure network isolation techniques emphasize enhancing air gap implementations with advanced monitoring and AI-driven anomaly detection to strengthen cyber defense against sophisticated attacks. Network segmentation is evolving through dynamic, software-defined boundaries leveraging zero trust architecture and micro-segmentation to minimize lateral movement and contain breaches more effectively. Emerging technologies, such as quantum-resistant encryption and integrated hardware-based isolation, are set to redefine the future landscape of secure network isolation.
Air Gap vs Network Segmentation Infographic
 techiny.com
techiny.com