Social engineering exploits human psychology to manipulate individuals into revealing confidential information, bypassing technical safeguards through deception and trust-building. Technical hacking, on the other hand, leverages software vulnerabilities, coding exploits, and system weaknesses to gain unauthorized access or control over digital assets. Both approaches pose significant cybersecurity threats, requiring comprehensive defense strategies that combine user awareness training with robust technical protections.
Table of Comparison
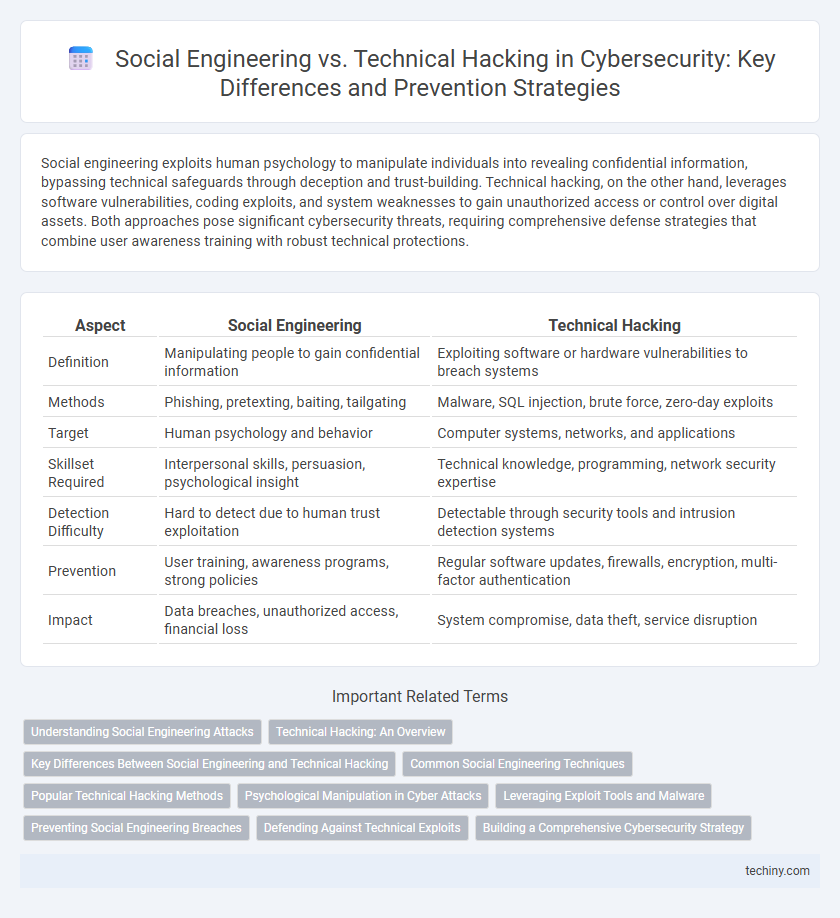
| Aspect | Social Engineering | Technical Hacking |
|---|---|---|
| Definition | Manipulating people to gain confidential information | Exploiting software or hardware vulnerabilities to breach systems |
| Methods | Phishing, pretexting, baiting, tailgating | Malware, SQL injection, brute force, zero-day exploits |
| Target | Human psychology and behavior | Computer systems, networks, and applications |
| Skillset Required | Interpersonal skills, persuasion, psychological insight | Technical knowledge, programming, network security expertise |
| Detection Difficulty | Hard to detect due to human trust exploitation | Detectable through security tools and intrusion detection systems |
| Prevention | User training, awareness programs, strong policies | Regular software updates, firewalls, encryption, multi-factor authentication |
| Impact | Data breaches, unauthorized access, financial loss | System compromise, data theft, service disruption |
Understanding Social Engineering Attacks
Social engineering attacks exploit human psychology to manipulate individuals into divulging confidential information or performing actions that compromise security. Unlike technical hacking, which leverages software vulnerabilities and exploits, social engineering relies on deception, phishing, pretexting, and baiting techniques to gain unauthorized access. Effective cybersecurity strategies must include comprehensive employee training and awareness programs to identify and resist social engineering attempts.
Technical Hacking: An Overview
Technical hacking involves exploiting software vulnerabilities, system misconfigurations, and network weaknesses to gain unauthorized access to computer systems. Techniques such as malware deployment, phishing kits, packet sniffing, and brute-force attacks target operating systems, databases, firewalls, and encryption protocols to compromise security. Cybersecurity professionals deploy advanced monitoring tools, intrusion detection systems, and regular patch management to defend against these persistent technical threats.
Key Differences Between Social Engineering and Technical Hacking
Social engineering exploits human psychology to manipulate individuals into divulging confidential information, while technical hacking targets system vulnerabilities through software, hardware, or network weaknesses. Social engineering attacks often involve phishing, pretexting, or baiting techniques to gain trust and extract sensitive data, whereas technical hacking employs methods like malware deployment, password cracking, and exploiting zero-day vulnerabilities. The key difference lies in the attack vector: social engineering attacks the human element, and technical hacking attacks technological defenses.
Common Social Engineering Techniques
Phishing remains the most prevalent social engineering technique, exploiting human trust through deceptive emails and fake websites to steal sensitive information. Pretexting involves attackers creating fabricated scenarios to manipulate victims into revealing confidential data or granting unauthorized access. Baiting leverages enticing offers or free downloads to trick users into installing malware or disclosing private information unknowingly.
Popular Technical Hacking Methods
Popular technical hacking methods in cybersecurity include phishing, malware deployment, and exploitation of software vulnerabilities. Techniques such as SQL injection, ransomware attacks, and brute-force password cracking remain prevalent threats targeting system infrastructure. Understanding these methods is crucial for establishing robust defense mechanisms against unauthorized access and data breaches.
Psychological Manipulation in Cyber Attacks
Social engineering exploits psychological manipulation to trick individuals into divulging confidential information or performing actions that compromise cybersecurity. Attackers leverage tactics such as phishing, pretexting, and baiting to bypass technological defenses by targeting human vulnerabilities. Understanding the cognitive biases and emotional triggers behind social engineering is crucial for developing effective defense strategies against cyber attacks.
Leveraging Exploit Tools and Malware
Social engineering exploits human psychology to manipulate individuals into divulging sensitive information, often bypassing traditional cybersecurity defenses. Technical hacking relies on advanced exploit tools and malware to infiltrate systems, enabling attackers to gain unauthorized access or disrupt operations. Combining social engineering tactics with malware deployment significantly increases the success rate of cyber attacks by targeting both human and technical vulnerabilities.
Preventing Social Engineering Breaches
Preventing social engineering breaches requires comprehensive employee training to recognize phishing attempts, suspicious links, and pretexting tactics. Implementing strict access controls combined with multi-factor authentication significantly reduces the risk of unauthorized data access triggered by manipulated insiders. Regular simulated phishing tests and robust incident response plans enhance organizational resilience against social engineering attacks.
Defending Against Technical Exploits
Defending against technical exploits requires implementing advanced intrusion detection systems, regular patch management, and robust endpoint security measures. Employing network segmentation and multi-factor authentication significantly reduces the attack surface and limits unauthorized access. Continuous monitoring and timely response protocols are essential to mitigate the impact of exploits in complex IT environments.
Building a Comprehensive Cybersecurity Strategy
A comprehensive cybersecurity strategy integrates both social engineering defenses and technical hacking countermeasures to mitigate risks effectively. Emphasizing employee training and awareness reduces vulnerabilities from phishing, impersonation, and human error, while deploying advanced firewalls, intrusion detection systems, and encryption tackles technical exploits. Combining behavioral analytics with continuous system monitoring creates a resilient defense architecture against evolving cyber threats.
Social Engineering vs Technical Hacking Infographic
 techiny.com
techiny.com