Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity and generate alerts without directly interfering with traffic flow. Intrusion Prevention Systems (IPS) actively block or prevent malicious traffic by taking immediate action upon detection. Deploying IPS provides real-time threat mitigation, whereas IDS offers detailed monitoring and forensic analysis for security teams.
Table of Comparison
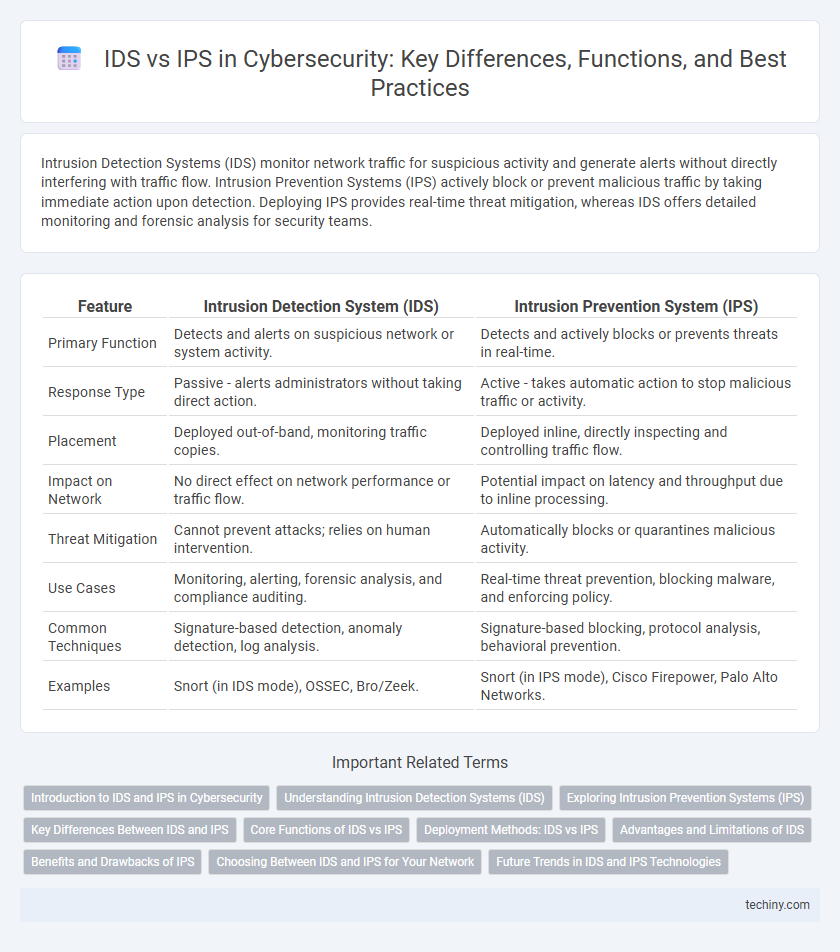
| Feature | Intrusion Detection System (IDS) | Intrusion Prevention System (IPS) |
|---|---|---|
| Primary Function | Detects and alerts on suspicious network or system activity. | Detects and actively blocks or prevents threats in real-time. |
| Response Type | Passive - alerts administrators without taking direct action. | Active - takes automatic action to stop malicious traffic or activity. |
| Placement | Deployed out-of-band, monitoring traffic copies. | Deployed inline, directly inspecting and controlling traffic flow. |
| Impact on Network | No direct effect on network performance or traffic flow. | Potential impact on latency and throughput due to inline processing. |
| Threat Mitigation | Cannot prevent attacks; relies on human intervention. | Automatically blocks or quarantines malicious activity. |
| Use Cases | Monitoring, alerting, forensic analysis, and compliance auditing. | Real-time threat prevention, blocking malware, and enforcing policy. |
| Common Techniques | Signature-based detection, anomaly detection, log analysis. | Signature-based blocking, protocol analysis, behavioral prevention. |
| Examples | Snort (in IDS mode), OSSEC, Bro/Zeek. | Snort (in IPS mode), Cisco Firepower, Palo Alto Networks. |
Introduction to IDS and IPS in Cybersecurity
Intrusion Detection Systems (IDS) monitor network traffic to identify suspicious activities and potential threats, providing alerts for further investigation. Intrusion Prevention Systems (IPS) actively analyze and block malicious traffic in real-time, preventing attacks before they impact the network. Both IDS and IPS play critical roles in cybersecurity by enhancing threat detection and response capabilities within enterprise environments.
Understanding Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) monitor network traffic to identify suspicious activities and potential security breaches by analyzing data packets and matching them against known attack signatures or behavioral anomalies. IDS tools generate alerts to inform administrators of possible threats but do not take direct action to block or prevent intrusions. Effective deployment of IDS enhances network visibility and supports incident response strategies by providing detailed logs and real-time threat detection.
Exploring Intrusion Prevention Systems (IPS)
Intrusion Prevention Systems (IPS) actively monitor network traffic to detect and block malicious activities in real time, providing immediate threat mitigation. Unlike Intrusion Detection Systems (IDS) that only alert administrators of potential threats, IPS can automatically enforce security policies and prevent intrusions before damage occurs. Key features include deep packet inspection, signature-based detection, and behavior analysis to protect against advanced cyberattacks and ensure network integrity.
Key Differences Between IDS and IPS
Intrusion Detection Systems (IDS) monitor network traffic to identify suspicious activities and generate alerts, while Intrusion Prevention Systems (IPS) actively block or prevent detected threats in real-time. IDS operates passively and relies on system administrators to respond to alerts, whereas IPS takes immediate action by interrupting malicious traffic before it reaches the target. The primary distinction lies in IDS being a detection tool focused on alerting, and IPS serving as both a detection and prevention mechanism to enhance network security.
Core Functions of IDS vs IPS
Intrusion Detection Systems (IDS) primarily monitor network traffic to identify suspicious activities and generate alerts for potential threats, functioning as a passive defense mechanism. Intrusion Prevention Systems (IPS) not only detect threats but also actively block or mitigate malicious traffic in real-time to prevent security breaches. IDS focuses on threat detection and alerting, whereas IPS emphasizes threat prevention and immediate response to attacks.
Deployment Methods: IDS vs IPS
Intrusion Detection Systems (IDS) are typically deployed in a passive monitoring mode, positioned out-of-band to analyze network traffic without interfering with the flow, enabling real-time alerts on suspicious activity. Intrusion Prevention Systems (IPS) are installed in-line directly within the network path, allowing them to actively block or prevent malicious traffic before reaching critical assets. The deployment method of IDS favors detection and alerting, while IPS emphasizes immediate response and threat mitigation.
Advantages and Limitations of IDS
Intrusion Detection Systems (IDS) provide comprehensive network monitoring by analyzing traffic for suspicious activities without interfering with data flow, offering valuable alerts that help identify potential security breaches. IDS advantages include their ability to detect unknown or novel threats through anomaly detection and low false positives due to their passive monitoring nature. Limitations involve the lack of preventive capabilities, as IDS cannot block attacks in real-time and may generate alert fatigue from excessive notifications, requiring skilled personnel for effective incident response.
Benefits and Drawbacks of IPS
Intrusion Prevention Systems (IPS) provide real-time threat blocking by actively monitoring network traffic to detect and prevent malicious activities before they cause harm. Benefits of IPS include automated threat prevention, reduced network downtime, and improved security posture by stopping attacks such as malware, exploits, and denial-of-service in their tracks. Drawbacks involve the potential for false positives that can block legitimate traffic, increased resource consumption affecting network performance, and the complexity of fine-tuning IPS rules to balance security and usability effectively.
Choosing Between IDS and IPS for Your Network
Choosing between an Intrusion Detection System (IDS) and an Intrusion Prevention System (IPS) depends on your network's security priorities and risk tolerance. IDS provides real-time monitoring and alerting for suspicious activities without interrupting network traffic, making it ideal for detailed analysis and incident response. IPS actively blocks threats and mitigates attacks, offering immediate protection but requiring careful tuning to avoid false positives that could disrupt legitimate network operations.
Future Trends in IDS and IPS Technologies
Future trends in IDS and IPS technologies emphasize the integration of artificial intelligence and machine learning to enhance threat detection accuracy and reduce false positives. Behavioral analytics and anomaly detection are becoming more sophisticated, enabling real-time identification of novel cyber threats. Cloud-native IDS and IPS solutions offer scalable, adaptive protection crucial for securing increasingly complex hybrid and multi-cloud environments.
IDS vs IPS Infographic
 techiny.com
techiny.com