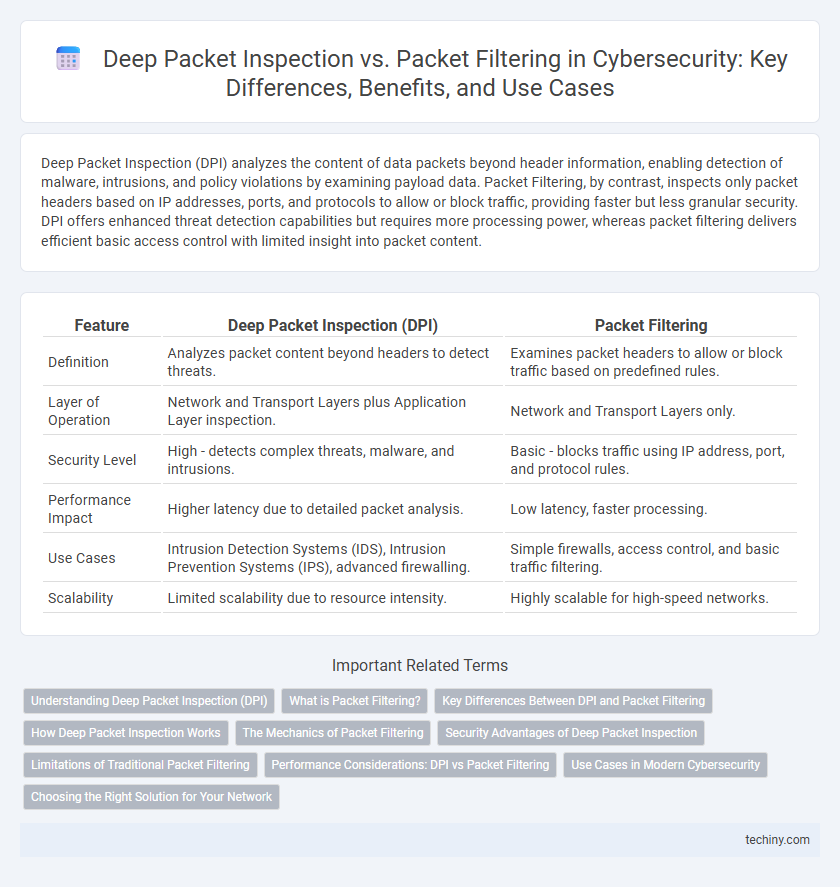
Deep Packet Inspection (DPI) analyzes the content of data packets beyond header information, enabling detection of malware, intrusions, and policy violations by examining payload data. Packet Filtering, by contrast, inspects only packet headers based on IP addresses, ports, and protocols to allow or block traffic, providing faster but less granular security. DPI offers enhanced threat detection capabilities but requires more processing power, whereas packet filtering delivers efficient basic access control with limited insight into packet content.
Table of Comparison
| Feature | Deep Packet Inspection (DPI) | Packet Filtering |
|---|---|---|
| Definition | Analyzes packet content beyond headers to detect threats. | Examines packet headers to allow or block traffic based on predefined rules. |
| Layer of Operation | Network and Transport Layers plus Application Layer inspection. | Network and Transport Layers only. |
| Security Level | High - detects complex threats, malware, and intrusions. | Basic - blocks traffic using IP address, port, and protocol rules. |
| Performance Impact | Higher latency due to detailed packet analysis. | Low latency, faster processing. |
| Use Cases | Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), advanced firewalling. | Simple firewalls, access control, and basic traffic filtering. |
| Scalability | Limited scalability due to resource intensity. | Highly scalable for high-speed networks. |
Understanding Deep Packet Inspection (DPI)
Deep Packet Inspection (DPI) analyzes the data part and header of network packets to detect malicious content, enabling advanced threat detection beyond basic Packet Filtering, which only inspects packet headers. DPI examines protocol compliance, application-specific data, and payload signatures, allowing identification of sophisticated attacks like malware, intrusions, and data exfiltration. Its ability to perform granular traffic analysis enhances security policies, improves threat prevention, and supports compliance with cybersecurity standards.
What is Packet Filtering?
Packet filtering is a fundamental network security technique that examines the header information of data packets to allow or block them based on predefined rules such as IP addresses, ports, and protocols. It operates at the network layer, offering basic protection by controlling traffic flow but lacks the ability to analyze the packet's payload or detect sophisticated threats. Unlike deep packet inspection, packet filtering provides faster processing but with limited security insights, making it suitable for simple access control and initial traffic screening.
Key Differences Between DPI and Packet Filtering
Deep Packet Inspection (DPI) analyzes the full content of data packets, enabling detection of malicious payloads and advanced threats, unlike Packet Filtering which only examines header information such as IP addresses and ports. DPI offers granular control by inspecting application-level data, making it effective against sophisticated cyber attacks, whereas Packet Filtering provides basic network access control with faster processing speeds. The contrast lies in DPI's comprehensive threat detection capabilities versus Packet Filtering's simpler, less resource-intensive approach.
How Deep Packet Inspection Works
Deep Packet Inspection (DPI) works by examining the data part and the header of a packet as it passes through an inspection point, enabling detailed analysis beyond simple packet filtering which only inspects headers. DPI uses sophisticated algorithms to detect malicious content, enforce security policies, and identify application-level threats by inspecting payload data in real time. This method allows for precise identification and blocking of cyber threats such as malware, intrusions, and unauthorized access attempts within network traffic.
The Mechanics of Packet Filtering
Packet filtering operates by examining the header information of each data packet, such as source and destination IP addresses, port numbers, and protocol types, to enforce security policies at the network layer. This process uses predefined rules to either allow or block packets, making it a fast and resource-efficient method for controlling network traffic. Compared to Deep Packet Inspection, which analyzes the packet payload for content-based threats, packet filtering offers a more basic but essential level of security by filtering packets based on header attributes alone.
Security Advantages of Deep Packet Inspection
Deep Packet Inspection (DPI) provides enhanced security by analyzing data at the application layer, enabling detection of sophisticated threats such as malware, intrusions, and data exfiltration attempts that packet filtering cannot identify. Unlike traditional packet filtering, which inspects only header information, DPI examines the payload of packets, allowing for granular control and prevention of advanced cyber attacks. This comprehensive inspection capability helps organizations enforce security policies more effectively, reducing risk and improving incident response accuracy.
Limitations of Traditional Packet Filtering
Traditional packet filtering inspects only the header information of packets, lacking the ability to analyze payload content, which limits its effectiveness against sophisticated cyber threats such as malware and ransomware. It cannot detect or block attacks embedded within legitimate traffic, making it vulnerable to evasion techniques like fragmentation or spoofing. Deep Packet Inspection overcomes these limitations by examining both header and payload data, enabling more granular and accurate threat detection.
Performance Considerations: DPI vs Packet Filtering
Deep Packet Inspection (DPI) involves analyzing the entire packet content, resulting in higher processing overhead and potentially increased latency compared to Packet Filtering, which only examines header information for faster throughput. DPI's comprehensive inspection demands more CPU and memory resources, impacting network performance especially in high-traffic environments. Packet Filtering provides superior performance efficiency by enabling quick decision-making with minimal resource usage, making it suitable for scenarios where speed is critical.
Use Cases in Modern Cybersecurity
Deep Packet Inspection (DPI) excels in identifying sophisticated cyber threats by analyzing the content of data packets beyond header information, making it ideal for detecting malware, intrusion attempts, and enforcing data policies in high-security environments. Packet Filtering, relying on header information like IP addresses and ports, remains effective for basic firewall functions, blocking unauthorized access, and controlling traffic in less complex or high-speed network scenarios. Modern cybersecurity integrates DPI for threat intelligence and compliance, while packet filtering provides foundational network security and performance optimization.
Choosing the Right Solution for Your Network
Deep Packet Inspection (DPI) offers advanced security by analyzing the data within packets, enabling detection of malware, intrusions, and policy violations beyond basic header information. Packet Filtering provides a faster, more resource-efficient method by controlling network access based on IP addresses, ports, and protocols but lacks the depth of inspection necessary for modern threats. Selecting the right solution depends on your network's security requirements, traffic volume, and processing capacity, balancing comprehensive threat detection with performance and scalability.
Deep Packet Inspection vs Packet Filtering Infographic
 techiny.com
techiny.com