Security policies establish the overarching rules and guidelines that govern an organization's approach to cybersecurity, defining responsibilities and acceptable use for resources. Security procedures are detailed, step-by-step instructions designed to implement these policies effectively, ensuring consistent execution and compliance. Together, they create a comprehensive framework that balances strategic intent with operational practices to protect digital assets.
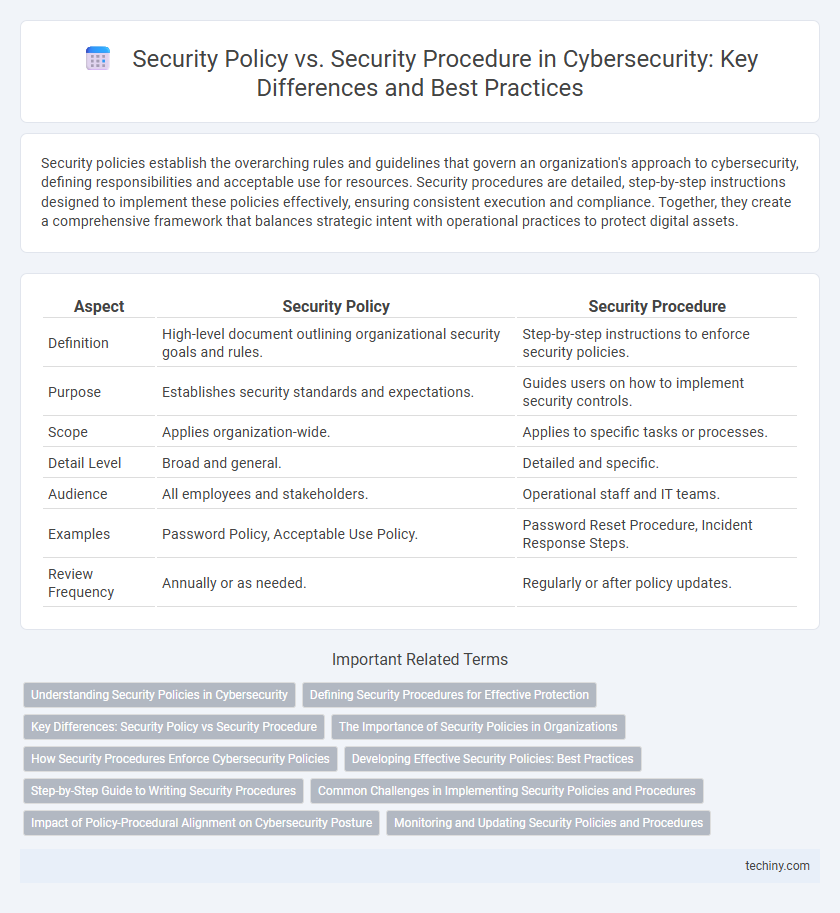
Table of Comparison
| Aspect | Security Policy | Security Procedure |
|---|---|---|
| Definition | High-level document outlining organizational security goals and rules. | Step-by-step instructions to enforce security policies. |
| Purpose | Establishes security standards and expectations. | Guides users on how to implement security controls. |
| Scope | Applies organization-wide. | Applies to specific tasks or processes. |
| Detail Level | Broad and general. | Detailed and specific. |
| Audience | All employees and stakeholders. | Operational staff and IT teams. |
| Examples | Password Policy, Acceptable Use Policy. | Password Reset Procedure, Incident Response Steps. |
| Review Frequency | Annually or as needed. | Regularly or after policy updates. |
Understanding Security Policies in Cybersecurity
Security policies in cybersecurity establish the foundational rules and guidelines designed to protect organizational assets and information from threats. These policies define the strategic objectives and high-level requirements that govern security behavior across the enterprise. Security procedures, derived from these policies, provide detailed, step-by-step instructions to ensure compliance and effective implementation of the overarching security framework.
Defining Security Procedures for Effective Protection
Security policies establish the overarching rules and principles guiding an organization's cybersecurity framework, while security procedures provide detailed, actionable steps to implement these policies effectively. Clearly defined security procedures ensure consistent application of controls such as access management, incident response, and data encryption, reducing vulnerabilities and enhancing threat mitigation. Regularly updating and testing these procedures aligns operational practices with evolving security policies and emergent cyber threats.
Key Differences: Security Policy vs Security Procedure
Security policies define the overall framework and rules for protecting an organization's information assets, establishing the "what" and "why" behind security measures, while security procedures specify the detailed steps and instructions on "how" to implement those policies effectively. Security policies are broad, high-level documents approved by management, focusing on risk management and compliance, whereas security procedures are operational, actionable guides used by staff to maintain security controls day-to-day. The key difference lies in scope and purpose: policies set strategic objectives and requirements, whereas procedures translate these into practical workflows and protocols.
The Importance of Security Policies in Organizations
Security policies establish the foundational rules and guidelines essential for protecting an organization's information assets from cyber threats. These high-level directives ensure consistent security practices, compliance with regulations, and risk management across all departments and technologies. Clear security policies enable organizations to define roles, responsibilities, and acceptable behaviors, thereby reducing vulnerabilities and promoting a secure operating environment.
How Security Procedures Enforce Cybersecurity Policies
Security procedures translate cybersecurity policies into actionable steps that ensure compliance, consistency, and effective risk management across an organization. These procedures specify detailed processes such as access controls, incident response actions, and user authentication methods, enabling systematic enforcement of high-level policy objectives. By operationalizing policies through precise guidelines and workflows, security procedures bridge the gap between strategic security goals and practical implementation.
Developing Effective Security Policies: Best Practices
Developing effective security policies involves clearly defining organizational objectives, regulatory requirements, and risk management strategies to establish a strong cybersecurity framework. Security policies set the overarching rules and guidelines, while security procedures provide detailed, step-by-step instructions to implement those policies consistently across the organization. Ensuring alignment between policies and procedures enhances compliance, reduces vulnerabilities, and strengthens incident response capabilities in cybersecurity management.
Step-by-Step Guide to Writing Security Procedures
A security policy defines the overall principles and rules for protecting an organization's information assets, while security procedures provide detailed, step-by-step instructions to implement those policies effectively. Writing security procedures involves identifying specific tasks, assigning responsible personnel, detailing required tools and inputs, and establishing clear, actionable steps to ensure compliance and consistency. Clear documentation and regular updates of these procedures help maintain robust cybersecurity defenses and support incident response efforts.
Common Challenges in Implementing Security Policies and Procedures
Common challenges in implementing security policies and procedures include resistance to change among employees, insufficient training, and lack of clarity in policy documentation. Organizations often struggle with ensuring consistent enforcement and alignment between policies and evolving cybersecurity threats. Inadequate resource allocation and poor communication can further hinder effective policy adoption and procedural compliance.
Impact of Policy-Procedural Alignment on Cybersecurity Posture
Security policy establishes overarching principles and goals that guide organizational cybersecurity efforts, while security procedures provide detailed, actionable steps to implement these policies effectively. Alignment between security policy and procedures ensures consistent enforcement of security measures, reducing vulnerabilities and enhancing incident response capabilities. This synergy significantly strengthens the organization's cybersecurity posture by promoting compliance, minimizing risks, and facilitating rapid recovery from cyber threats.
Monitoring and Updating Security Policies and Procedures
Security policies define the overarching rules and guidelines for an organization's cybersecurity framework, while security procedures detail the specific steps to implement those policies effectively. Continuous monitoring involves regularly assessing the efficacy of these policies and procedures to detect vulnerabilities and compliance gaps. Updating security policies and procedures ensures they adapt to evolving cyber threats, regulatory changes, and technological advancements, maintaining robust defense mechanisms.
Security policy vs security procedure Infographic
 techiny.com
techiny.com