Ransomware encrypts critical data and demands payment for its release, severely disrupting business operations and risking data loss. Scareware tricks users into believing their system is infected, prompting them to purchase fake antivirus software or services. Both threats exploit fear but differ in execution, with ransomware causing direct harm and scareware relying on psychological manipulation.
Table of Comparison
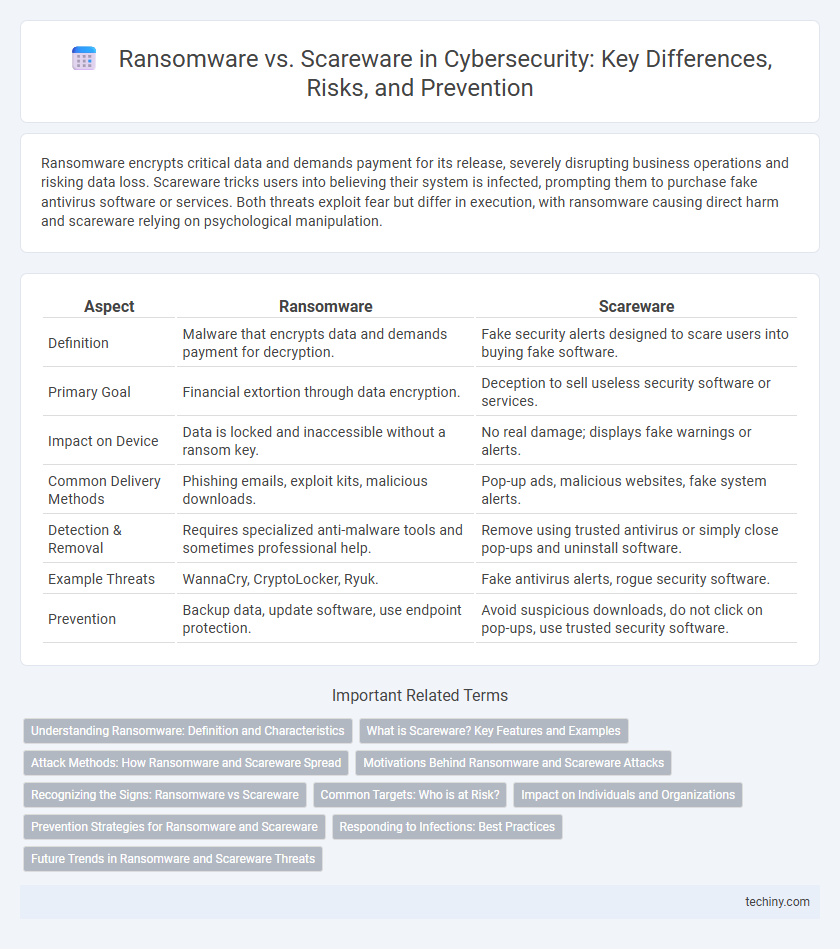
| Aspect | Ransomware | Scareware |
|---|---|---|
| Definition | Malware that encrypts data and demands payment for decryption. | Fake security alerts designed to scare users into buying fake software. |
| Primary Goal | Financial extortion through data encryption. | Deception to sell useless security software or services. |
| Impact on Device | Data is locked and inaccessible without a ransom key. | No real damage; displays fake warnings or alerts. |
| Common Delivery Methods | Phishing emails, exploit kits, malicious downloads. | Pop-up ads, malicious websites, fake system alerts. |
| Detection & Removal | Requires specialized anti-malware tools and sometimes professional help. | Remove using trusted antivirus or simply close pop-ups and uninstall software. |
| Example Threats | WannaCry, CryptoLocker, Ryuk. | Fake antivirus alerts, rogue security software. |
| Prevention | Backup data, update software, use endpoint protection. | Avoid suspicious downloads, do not click on pop-ups, use trusted security software. |
Understanding Ransomware: Definition and Characteristics
Ransomware is a type of malicious software designed to block access to a computer system or data until a ransom is paid, often through encryption of critical files. It typically spreads via phishing emails, exploit kits, and malicious downloads, targeting individuals, businesses, and government agencies. Key characteristics include data encryption, ransom notes demanding payment in cryptocurrency, and the potential for widespread operational disruption.
What is Scareware? Key Features and Examples
Scareware is a type of malicious software designed to trick users into believing their device is infected with viruses or threats, prompting them to pay for fake antivirus solutions. Key features include alarming pop-up messages, fake system scans, and urgent warnings urging immediate action. Examples of scareware include fake antivirus programs like "Antivirus Security Pro" and deceptive alerts claiming a user's PC is compromised.
Attack Methods: How Ransomware and Scareware Spread
Ransomware primarily spreads through phishing emails containing malicious attachments or links that exploit software vulnerabilities, as well as via drive-by downloads from compromised websites. Scareware uses social engineering tactics, such as fake security alerts and pop-up warnings, to trick users into downloading deceptive software or paying for unnecessary protections. Both attack methods exploit human psychology but differ in technical execution, with ransomware encrypting data and scareware relying on intimidation to drive user actions.
Motivations Behind Ransomware and Scareware Attacks
Ransomware attacks are primarily motivated by financial gain, as cybercriminals encrypt victims' data and demand ransom payments for decryption keys. Scareware campaigns exploit fear and anxiety by displaying fake security alerts to trick users into purchasing unnecessary software or divulging personal information. Both attack types leverage psychological manipulation, but ransomware emphasizes direct monetary extortion while scareware focuses on deceit-driven profit through user deception and fear exploitation.
Recognizing the Signs: Ransomware vs Scareware
Ransomware encrypts files and demands payment for decryption, often accompanied by a threatening message and countdown timer, signaling immediate data loss risk. Scareware uses fake alerts and pop-ups to frighten users into purchasing unnecessary software, without actual system compromise. Identifying ransomware involves detecting locked files and ransom notes, whereas scareware shows persistent fake warnings but leaves system files intact.
Common Targets: Who is at Risk?
Ransomware primarily targets businesses, healthcare institutions, and government agencies due to their valuable data and critical operations, while scareware often focuses on individual users and less tech-savvy victims through deceptive pop-ups and fake security alerts. Both threats exploit vulnerabilities in software, outdated systems, and insufficient cybersecurity training to gain access. High-risk sectors include finance, healthcare, and small to medium enterprises lacking robust cybersecurity protocols.
Impact on Individuals and Organizations
Ransomware encrypts critical data, causing significant financial loss and operational disruption for both individuals and organizations due to demands for ransom payments. Scareware tricks users into believing their system is infected, prompting unnecessary purchases or actions that compromise security and waste resources. The impact of ransomware is more severe as it directly restricts access to data, while scareware primarily exploits fear to generate profit and erode user trust.
Prevention Strategies for Ransomware and Scareware
Effective prevention strategies for ransomware include regular data backups, strong email filtering systems, and maintaining updated security patches to reduce vulnerabilities. Scareware prevention relies on educating users to recognize fake alerts, employing robust anti-malware solutions, and avoiding clicks on suspicious pop-ups or links. Both threats demand comprehensive cybersecurity policies, multi-layered defenses, and continuous employee awareness training to mitigate risks.
Responding to Infections: Best Practices
Responding to ransomware infections requires immediate isolation of affected systems to prevent lateral movement and engaging specialized incident response teams for data recovery through verified backups. In contrast, scareware infections demand user education to recognize fraudulent alerts, thorough malware scans with reputable antivirus software, and careful removal of rogue applications without succumbing to ransom demands. Both cases emphasize regular data backups, updated security patches, and continuous monitoring to mitigate future risks.
Future Trends in Ransomware and Scareware Threats
Ransomware threats are evolving with increased use of artificial intelligence to bypass traditional security measures and target high-value enterprises through multi-stage attacks. Scareware is expected to grow in sophistication by leveraging social engineering and deepfake technologies to manipulate victims into paying ransoms or sharing sensitive data. Emerging cybersecurity strategies emphasize rapid detection, behavioral analysis, and zero-trust frameworks to mitigate future ransomware and scareware risks effectively.
Ransomware vs Scareware Infographic
 techiny.com
techiny.com