Forward proxies act as intermediaries between clients and the internet, primarily used to control and monitor outbound traffic for security and privacy purposes. Reverse proxies stand on behalf of servers, managing inbound traffic to distribute loads, cache content, and protect backend systems from direct exposure. Understanding the distinct roles of forward and reverse proxies is crucial for implementing comprehensive cybersecurity measures in network architecture.
Table of Comparison
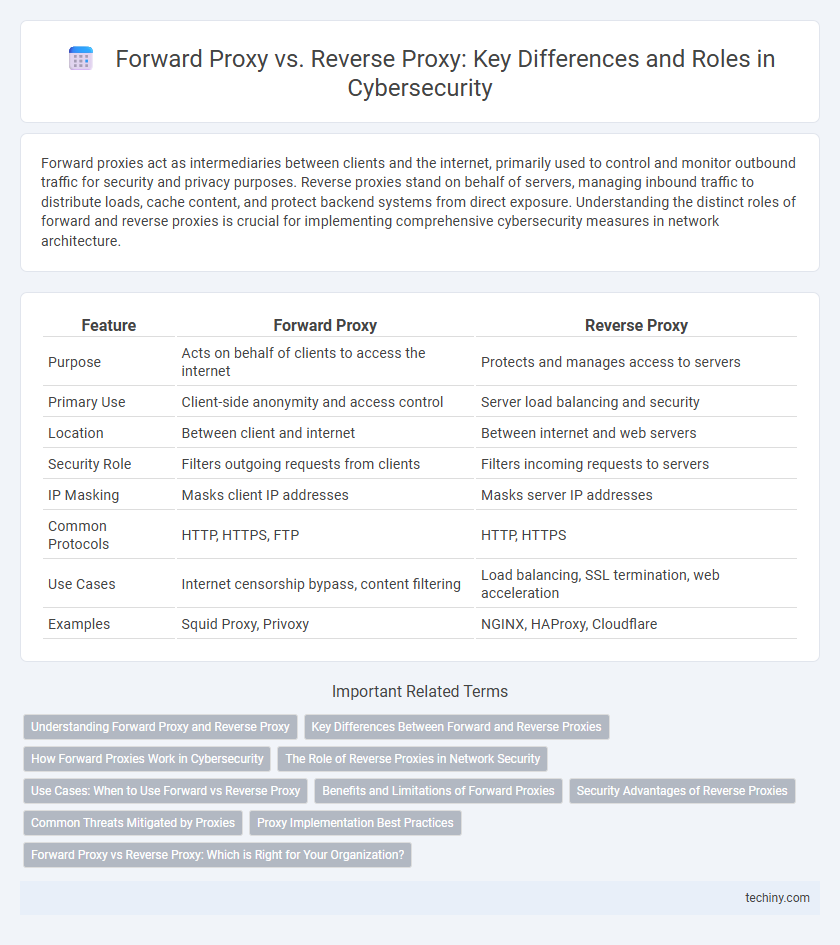
| Feature | Forward Proxy | Reverse Proxy |
|---|---|---|
| Purpose | Acts on behalf of clients to access the internet | Protects and manages access to servers |
| Primary Use | Client-side anonymity and access control | Server load balancing and security |
| Location | Between client and internet | Between internet and web servers |
| Security Role | Filters outgoing requests from clients | Filters incoming requests to servers |
| IP Masking | Masks client IP addresses | Masks server IP addresses |
| Common Protocols | HTTP, HTTPS, FTP | HTTP, HTTPS |
| Use Cases | Internet censorship bypass, content filtering | Load balancing, SSL termination, web acceleration |
| Examples | Squid Proxy, Privoxy | NGINX, HAProxy, Cloudflare |
Understanding Forward Proxy and Reverse Proxy
Forward proxies act as intermediaries between client devices and the internet, masking client IPs and enforcing access controls to protect user privacy and security. Reverse proxies sit in front of web servers, managing incoming traffic, enhancing load balancing, SSL termination, and providing an additional security layer against attacks such as DDoS. Both proxy types improve cybersecurity posture by controlling traffic flow and hiding internal network structures.
Key Differences Between Forward and Reverse Proxies
Forward proxies act as intermediaries between clients and the internet, masking client IP addresses to enhance privacy and control outbound traffic. Reverse proxies sit in front of web servers, managing incoming requests, balancing loads, and providing security by hiding server details. Key differences include their placement relative to clients and servers, with forward proxies primarily serving client needs and reverse proxies protecting server resources.
How Forward Proxies Work in Cybersecurity
Forward proxies act as intermediaries between client devices and the internet, masking client IP addresses while managing outbound web traffic to enhance privacy and security. They filter requests, block malicious sites, and enforce organizational policies by examining and controlling data packets before reaching external servers. This mechanism protects internal networks from direct exposure, reduces the risk of cyber threats, and ensures secure browsing within corporate environments.
The Role of Reverse Proxies in Network Security
Reverse proxies serve as a critical security layer by intercepting client requests and forwarding them to backend servers, thus masking the internal network structure from external users. They provide protection against cyber threats such as DDoS attacks, SQL injections, and cross-site scripting by filtering malicious traffic before it reaches the application servers. By enabling load balancing and SSL termination, reverse proxies enhance both security and performance, making them indispensable in modern cybersecurity strategies.
Use Cases: When to Use Forward vs Reverse Proxy
Forward proxies are ideal for client-side use cases such as controlling user access, enhancing privacy, and caching content to improve performance in corporate or educational networks. Reverse proxies, positioned server-side, are crucial for load balancing, protecting web servers from attacks, and enabling SSL termination to secure and optimize inbound traffic. Organizations should deploy forward proxies to manage outbound user requests and reverse proxies to safeguard and distribute incoming web traffic efficiently.
Benefits and Limitations of Forward Proxies
Forward proxies enhance user privacy and security by masking client IP addresses and controlling access to external resources, making them ideal for corporate environments managing internet usage. They improve performance through caching frequently requested web content but may introduce latency due to additional processing and require careful configuration to avoid becoming security vulnerabilities themselves. Limitations include their ineffectiveness in protecting the target servers and challenges in handling encrypted HTTPS traffic without advanced setup.
Security Advantages of Reverse Proxies
Reverse proxies enhance cybersecurity by masking the identity and location of backend servers, reducing direct exposure to potential attackers. They offer centralized control over incoming traffic, enabling advanced security measures such as SSL termination, web application firewall (WAF) integration, and rate limiting. This centralized filtering helps prevent DDoS attacks, unauthorized access, and data breaches, significantly strengthening the overall network defense.
Common Threats Mitigated by Proxies
Forward proxies mitigate threats such as IP address spoofing, unauthorized access, and malware by filtering outbound client requests and hiding internal network details. Reverse proxies protect web servers from Distributed Denial of Service (DDoS) attacks, application-layer threats, and data breaches by inspecting incoming traffic and blocking malicious requests before they reach backend servers. Both proxy types enhance security posture by enabling content caching, SSL offloading, and traffic monitoring to detect and prevent cyber threats.
Proxy Implementation Best Practices
Forward proxy implementation best practices emphasize strict access control, ensuring only authorized users can route requests through the proxy to external networks. Reverse proxy configurations should prioritize load balancing, SSL termination, and robust web application firewall integration to protect backend servers from malicious traffic. Regularly updating proxy software and monitoring traffic logs are essential to maintain high security and performance in both forward and reverse proxy setups.
Forward Proxy vs Reverse Proxy: Which is Right for Your Organization?
Forward proxies serve as intermediaries that mask internal clients' IP addresses while accessing external resources, ideal for controlling employee internet use and enhancing privacy. Reverse proxies sit in front of web servers, managing incoming traffic, improving load balancing, and providing an additional security layer against attacks such as DDoS. Organizations seeking to protect internal user identities and monitor outbound traffic should consider forward proxies, whereas those focusing on securing and optimizing inbound web traffic should prioritize reverse proxy solutions.
Forward Proxy vs Reverse Proxy Infographic
 techiny.com
techiny.com