Log analysis involves examining system-generated records to identify suspicious activities and security breaches, providing a historical overview of events. Packet analysis inspects data packets transmitted over a network in real-time, enabling the detection of threats such as malware and unauthorized access attempts. Combining both techniques enhances cybersecurity by offering comprehensive visibility into attacks and improving incident response.
Table of Comparison
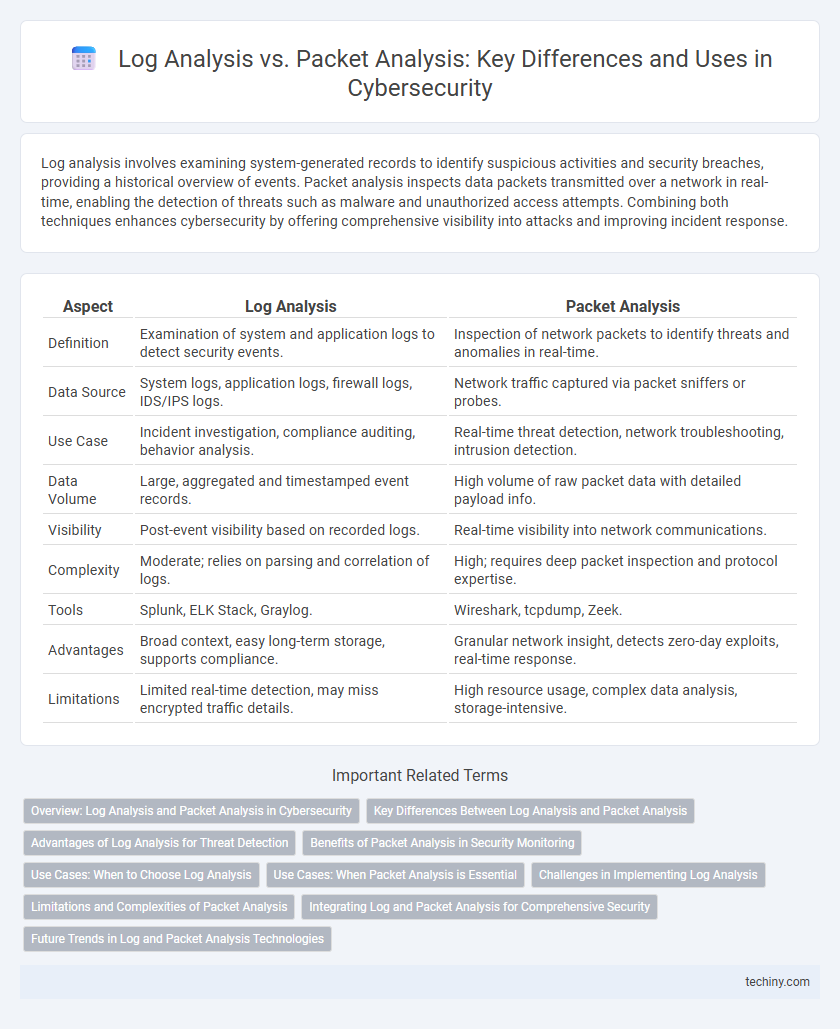
| Aspect | Log Analysis | Packet Analysis |
|---|---|---|
| Definition | Examination of system and application logs to detect security events. | Inspection of network packets to identify threats and anomalies in real-time. |
| Data Source | System logs, application logs, firewall logs, IDS/IPS logs. | Network traffic captured via packet sniffers or probes. |
| Use Case | Incident investigation, compliance auditing, behavior analysis. | Real-time threat detection, network troubleshooting, intrusion detection. |
| Data Volume | Large, aggregated and timestamped event records. | High volume of raw packet data with detailed payload info. |
| Visibility | Post-event visibility based on recorded logs. | Real-time visibility into network communications. |
| Complexity | Moderate; relies on parsing and correlation of logs. | High; requires deep packet inspection and protocol expertise. |
| Tools | Splunk, ELK Stack, Graylog. | Wireshark, tcpdump, Zeek. |
| Advantages | Broad context, easy long-term storage, supports compliance. | Granular network insight, detects zero-day exploits, real-time response. |
| Limitations | Limited real-time detection, may miss encrypted traffic details. | High resource usage, complex data analysis, storage-intensive. |
Overview: Log Analysis and Packet Analysis in Cybersecurity
Log analysis in cybersecurity involves examining system and application logs to identify anomalies, detect security breaches, and understand attack patterns by parsing time-stamped records generated by various sources such as firewalls, intrusion detection systems, and servers. Packet analysis entails capturing and inspecting network packets at the data level to monitor real-time traffic, uncover malware communication, and detect suspicious data flows using tools like Wireshark and tcpdump. Both methodologies complement each other by providing comprehensive visibility into network behavior and aiding in proactive threat detection and forensic investigations.
Key Differences Between Log Analysis and Packet Analysis
Log analysis examines recorded data entries generated by systems and applications, focusing on event tracking and forensic investigation over time. Packet analysis inspects raw network traffic in real-time, enabling detection of intrusions, protocol anomalies, and detailed communication patterns. The key difference lies in log analysis providing historical context via stored data, whereas packet analysis offers immediate visibility into live network activity.
Advantages of Log Analysis for Threat Detection
Log analysis offers comprehensive historical data, enabling the detection of persistent and slow-moving cyber threats by examining system and application records. It provides contextual insights through detailed event logs, which enhance the accuracy of threat identification and support incident correlation. Centralized log management also facilitates efficient monitoring across multiple devices, improving response times and overall security posture.
Benefits of Packet Analysis in Security Monitoring
Packet analysis provides granular visibility into network traffic, enabling the detection of advanced threats like zero-day attacks and data exfiltration attempts that may not generate logs. It captures real-time data at the packet level, allowing security teams to identify anomalies, inspect payloads, and trace the exact attack vectors. This detailed monitoring supports proactive threat hunting and incident response, significantly enhancing overall security posture.
Use Cases: When to Choose Log Analysis
Log analysis is essential for identifying patterns and anomalies in historical data, making it ideal for forensic investigations and compliance auditing. It excels in detecting insider threats, policy violations, and long-term trends by examining system, application, and security logs. Organizations prioritize log analysis when detailed context and event correlation over extended periods are required for threat detection and regulatory reporting.
Use Cases: When Packet Analysis is Essential
Packet analysis is essential for real-time network troubleshooting, identifying malicious payloads, and detecting sophisticated attacks such as zero-day exploits. It provides granular visibility into network traffic, enabling security teams to inspect headers and payloads for anomalies that log analysis might miss. Packet analysis is crucial in incident response scenarios where precise traffic reconstruction and deep protocol understanding are required to dissect attack vectors.
Challenges in Implementing Log Analysis
Implementing log analysis in cybersecurity faces challenges such as managing massive volumes of heterogeneous logs from multiple sources, which can overwhelm storage and processing capabilities. Incomplete or inconsistent log data often hinders accurate threat detection, complicating incident response efforts. Ensuring real-time analysis and maintaining data integrity require sophisticated tools and skilled personnel, increasing operational complexity.
Limitations and Complexities of Packet Analysis
Packet analysis encounters significant limitations due to the vast volume of data generated in network traffic, making real-time inspection resource-intensive and potentially leading to performance bottlenecks. Encrypted packets further complicate analysis by obscuring payload content, hindering threat detection and forensic investigations. The complexity of reconstructing session data from fragmented packets demands advanced expertise and tools, increasing operational overhead compared to log analysis.
Integrating Log and Packet Analysis for Comprehensive Security
Integrating log analysis and packet analysis offers a comprehensive security strategy by combining detailed event records with real-time network traffic insights. Log analysis provides historical data on user activities and system events, while packet analysis captures live communication patterns and anomalies at the network level. Leveraging both techniques enhances threat detection, incident response, and forensics, enabling more accurate identification of sophisticated cyberattacks and reducing blind spots in security monitoring.
Future Trends in Log and Packet Analysis Technologies
Future trends in log and packet analysis technologies emphasize the integration of artificial intelligence and machine learning to enhance threat detection accuracy and reduce false positives. Advanced analytics platforms leverage real-time data processing and automation to identify complex attack patterns and support proactive cybersecurity measures. Growing adoption of cloud-native solutions and improved encryption handling techniques are transforming how organizations monitor and secure network traffic and system logs.
Log Analysis vs Packet Analysis Infographic
 techiny.com
techiny.com