Endpoint protection safeguards individual devices by detecting malware, managing vulnerabilities, and controlling access, ensuring threats are neutralized at the source. Network protection monitors and controls incoming and outgoing traffic to prevent unauthorized access, detect anomalies, and block attacks targeting entire network infrastructures. Combining both strategies provides a comprehensive defense, addressing threats at device and network levels to enhance overall cybersecurity resilience.
Table of Comparison
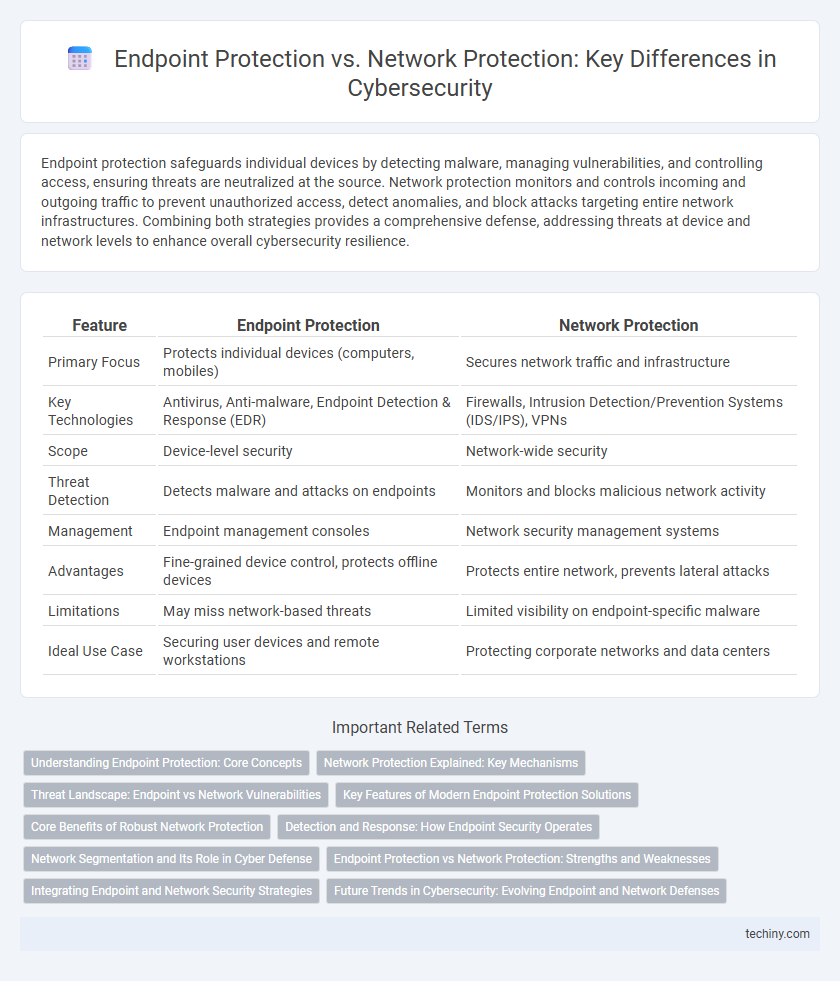
| Feature | Endpoint Protection | Network Protection |
|---|---|---|
| Primary Focus | Protects individual devices (computers, mobiles) | Secures network traffic and infrastructure |
| Key Technologies | Antivirus, Anti-malware, Endpoint Detection & Response (EDR) | Firewalls, Intrusion Detection/Prevention Systems (IDS/IPS), VPNs |
| Scope | Device-level security | Network-wide security |
| Threat Detection | Detects malware and attacks on endpoints | Monitors and blocks malicious network activity |
| Management | Endpoint management consoles | Network security management systems |
| Advantages | Fine-grained device control, protects offline devices | Protects entire network, prevents lateral attacks |
| Limitations | May miss network-based threats | Limited visibility on endpoint-specific malware |
| Ideal Use Case | Securing user devices and remote workstations | Protecting corporate networks and data centers |
Understanding Endpoint Protection: Core Concepts
Endpoint protection secures individual devices such as laptops, smartphones, and desktops by detecting malware, preventing unauthorized access, and ensuring data integrity. Key components include antivirus software, firewalls, intrusion detection systems, and device control policies designed to reduce vulnerabilities at the device level. Endpoint protection emphasizes real-time monitoring, behavioral analysis, and centralized management to defend against threats targeting user endpoints specifically.
Network Protection Explained: Key Mechanisms
Network protection employs firewalls, intrusion detection systems (IDS), and encryption techniques to safeguard data flow and prevent unauthorized access within corporate networks. Key mechanisms include deep packet inspection, anomaly detection, and secure VPNs, which collectively monitor and control inbound and outbound traffic to identify and mitigate cyber threats. Effective network protection reduces the attack surface by segmenting networks and enforcing strict access controls, ensuring comprehensive defense against malware, ransomware, and advanced persistent threats (APTs).
Threat Landscape: Endpoint vs Network Vulnerabilities
Endpoint protection targets vulnerabilities on individual devices such as laptops, smartphones, and desktops, addressing threats like malware, ransomware, and phishing attacks that exploit user behavior and software flaws. Network protection focuses on securing the infrastructure by monitoring traffic, preventing unauthorized access, and mitigating attacks like DDoS, man-in-the-middle, and network intrusions that exploit protocol weaknesses and misconfigurations. The evolving threat landscape requires integrating endpoint and network defenses to address sophisticated attack vectors exploiting both device-level vulnerabilities and network communications.
Key Features of Modern Endpoint Protection Solutions
Modern endpoint protection solutions integrate advanced threat detection techniques, such as machine learning and behavioral analysis, to identify and mitigate malware, ransomware, and zero-day attacks directly on devices. These platforms offer real-time monitoring, automated response capabilities, and comprehensive device control features like application whitelisting and data encryption to safeguard sensitive information. Endpoint protection emphasizes individualized device security, complementing network protection systems that focus on perimeter defense and traffic inspection.
Core Benefits of Robust Network Protection
Robust network protection offers comprehensive defense against external cyber threats by monitoring and controlling incoming and outgoing traffic, effectively preventing unauthorized access and malware spread across the entire network. It enhances visibility into network activity, enabling early detection of suspicious behavior and reducing the risk of data breaches. Unlike endpoint protection, which secures individual devices, network protection provides centralized security management, ensuring consistent enforcement of security policies across all connected systems.
Detection and Response: How Endpoint Security Operates
Endpoint security operates by continuously monitoring and analyzing data on individual devices to detect malware, suspicious behavior, and unauthorized access in real time. It leverages advanced technologies such as machine learning, behavioral analytics, and threat intelligence to provide rapid detection and automated response, isolating compromised endpoints to prevent lateral movement. Unlike network protection, which focuses on traffic and perimeter defense, endpoint security offers granular visibility and control at the device level, essential for identifying sophisticated threats that bypass traditional network defenses.
Network Segmentation and Its Role in Cyber Defense
Network segmentation is a critical component of network protection that enhances cybersecurity by dividing a larger network into smaller, isolated segments to limit the spread of cyber threats. This technique restricts unauthorized lateral movement within the network, reducing the attack surface and containing potential breaches more effectively than endpoint protection alone. Incorporating network segmentation alongside endpoint protection creates a layered defense strategy, strengthening overall cyber resilience against complex and evolving threats.
Endpoint Protection vs Network Protection: Strengths and Weaknesses
Endpoint protection excels in securing individual devices by detecting malware, unauthorized access, and suspicious behavior directly on endpoints such as laptops, smartphones, and desktops, providing granular control and real-time threat response. Network protection focuses on monitoring and guarding data in transit across the entire network infrastructure, effectively blocking external attacks like DDoS, intrusion attempts, and lateral malware movement but may miss threats originating inside endpoints. Combining both strategies offers comprehensive cybersecurity, as endpoint protection addresses device-level vulnerabilities while network protection fortifies overall traffic and perimeter defenses.
Integrating Endpoint and Network Security Strategies
Integrating endpoint and network security strategies enhances threat detection and response by providing comprehensive visibility across all access points and communication channels. Endpoint Protection Platforms (EPP) safeguard individual devices from malware, ransomware, and unauthorized access, while Network Protection focuses on monitoring traffic, preventing intrusions, and enforcing segmentation policies. Combining these approaches enables organizations to correlate endpoint data with network activity, improving incident detection accuracy and reducing response times.
Future Trends in Cybersecurity: Evolving Endpoint and Network Defenses
Future trends in cybersecurity emphasize the integration of AI-powered endpoint protection with adaptive network defense systems to counter increasingly sophisticated threats. Endpoint protection leverages behavioral analytics and zero-trust architectures to secure devices at the edge, while network protection evolves through real-time threat intelligence and automated segmentation. Emerging technologies like extended detection and response (XDR) unify endpoint and network data streams, enabling faster threat mitigation and proactive defense strategies.
Endpoint Protection vs Network Protection Infographic
 techiny.com
techiny.com