Sandboxing isolates applications within a restricted environment to prevent malicious code from affecting the host system, offering lightweight and rapid threat analysis. Virtualization creates full virtual machines with dedicated operating systems, providing stronger security boundaries but requiring more resources and setup time. Choosing between sandboxing and virtualization depends on the balance between performance needs and security requirements in cybersecurity protection.
Table of Comparison
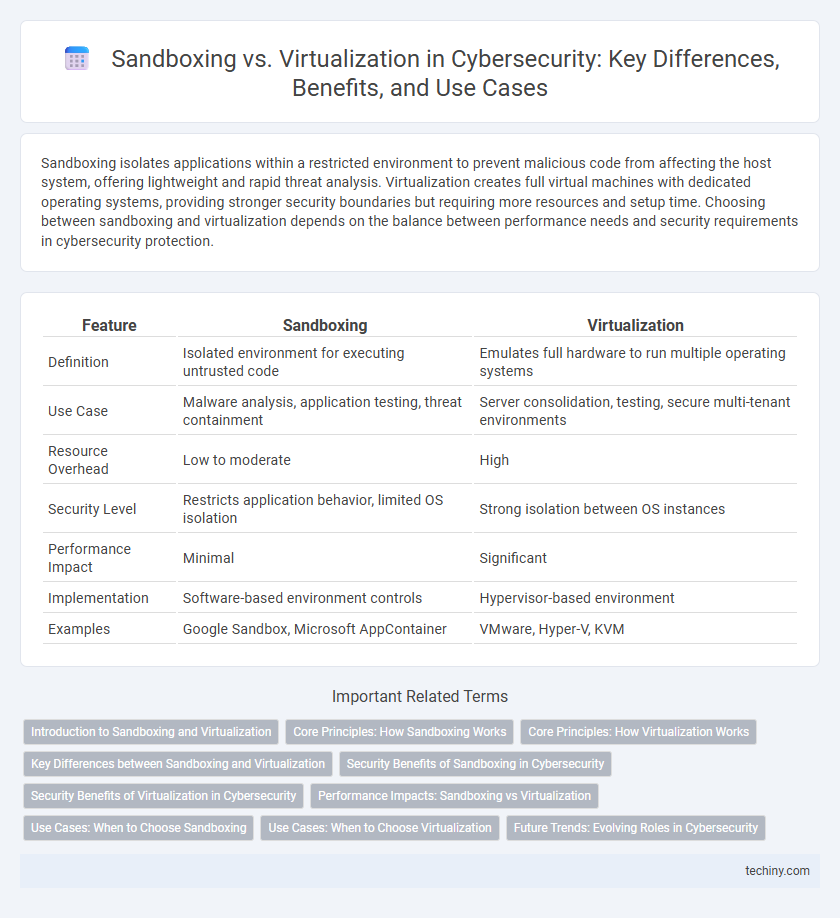
| Feature | Sandboxing | Virtualization |
|---|---|---|
| Definition | Isolated environment for executing untrusted code | Emulates full hardware to run multiple operating systems |
| Use Case | Malware analysis, application testing, threat containment | Server consolidation, testing, secure multi-tenant environments |
| Resource Overhead | Low to moderate | High |
| Security Level | Restricts application behavior, limited OS isolation | Strong isolation between OS instances |
| Performance Impact | Minimal | Significant |
| Implementation | Software-based environment controls | Hypervisor-based environment |
| Examples | Google Sandbox, Microsoft AppContainer | VMware, Hyper-V, KVM |
Introduction to Sandboxing and Virtualization
Sandboxing creates isolated environments to execute untrusted code safely, preventing potential threats from affecting the host system. Virtualization involves running multiple virtual machines on a single physical server, enabling resource optimization and strong isolation. Both technologies are pivotal in cybersecurity for threat containment and secure testing of applications.
Core Principles: How Sandboxing Works
Sandboxing isolates applications and processes within a controlled environment, preventing unauthorized access to the host system and sensitive data by restricting their operations to this confined space. It leverages techniques like namespace isolation, resource access controls, and policy enforcement to monitor and contain potentially malicious behavior. This core principle enhances threat detection by allowing suspicious code to execute without affecting overall system integrity, distinguishing sandboxing from broader virtualization that creates entire virtual machines.
Core Principles: How Virtualization Works
Virtualization fundamentally operates by creating isolated virtual machines (VMs) on a single physical hardware platform, enabling multiple operating systems to run concurrently with dedicated resources. Each VM contains its own guest OS, applications, and virtualized hardware, abstracted from the host system through a hypervisor that manages resource allocation and enforces isolation. This approach ensures strong security boundaries, efficient resource utilization, and flexibility in deploying diverse workloads within controlled environments.
Key Differences between Sandboxing and Virtualization
Sandboxing isolates applications or code within a controlled environment to prevent system-wide impact, focusing on lightweight and temporary containment. Virtualization creates entire virtual machines with dedicated operating systems and resources, enabling complete separation from the host system for running multiple OS instances simultaneously. Sandboxing emphasizes application-level security and behavior analysis, whereas virtualization provides full hardware abstraction and resource management for broader system isolation.
Security Benefits of Sandboxing in Cybersecurity
Sandboxing provides robust security by isolating applications and processes within a controlled environment, preventing malware from spreading to the host system. It enables safe execution of untrusted code, detecting malicious behavior without risking critical infrastructure. Unlike traditional virtualization, sandboxing focuses on granular isolation, making it highly effective for threat containment and dynamic analysis in cybersecurity.
Security Benefits of Virtualization in Cybersecurity
Virtualization enhances cybersecurity by isolating multiple virtual machines on a single physical host, reducing the risk of malware spreading between environments. It enables rapid recovery and system snapshots, allowing quick restoration to secure states after an attack. Furthermore, virtualization supports secure testing and development, minimizing the impact of vulnerabilities on production systems.
Performance Impacts: Sandboxing vs Virtualization
Sandboxing typically incurs lower performance overhead than virtualization because it isolates applications within the same operating system kernel, minimizing resource duplication. Virtualization emulates entire hardware environments, leading to higher CPU and memory consumption due to running multiple guest operating systems concurrently. Consequently, sandboxing offers faster execution speeds and reduced latency, making it ideal for real-time cybersecurity tasks requiring efficient resource usage.
Use Cases: When to Choose Sandboxing
Sandboxing is ideal for analyzing untrusted code or suspicious files in isolated environments without affecting the host system, making it essential for malware detection and threat analysis. It excels in real-time threat containment by allowing secure execution of potentially harmful applications, preventing lateral movement within networks. Organizations prioritize sandboxing for dynamic application testing, email attachment scans, and zero-day exploit detection due to its granular control and rapid response capabilities.
Use Cases: When to Choose Virtualization
Virtualization is ideal for running multiple isolated operating systems on a single physical machine, enabling efficient resource utilization and complex multi-environment testing. It is preferred for scenarios requiring full OS emulation, such as software development, legacy application support, and enterprise-level server consolidation. Virtual machines offer robust security isolation, making them suitable for detailed malware analysis and secure cloud infrastructure deployments.
Future Trends: Evolving Roles in Cybersecurity
Sandboxing and virtualization are set to become more integrated in future cybersecurity frameworks, enhancing threat detection and containment by isolating malicious activities within controlled environments. Advances in AI-driven sandbox environments will enable dynamic analysis of zero-day exploits with greater precision, reducing false positives and accelerating response times. Virtualization is expected to evolve beyond infrastructure efficiency, playing a critical role in adaptive security architectures that isolate workloads and enforce micro-segmentation across distributed cloud systems.
sandboxing vs virtualization Infographic
 techiny.com
techiny.com